BYOD and Your Business: Why BYOD Policies Are Key to Success
Bring Your Own Device: Right for Your Office IT?
When you first hear “BYO” mentioned, office technoligies may not be the first thing that springs to mind…
Things have changed in the workplace, and BYO (Bring Your Own) has taken on a new significance as the popularity and importance of Bring Your Own Device (BYOD) has continued to grow rapidly over the last few years.
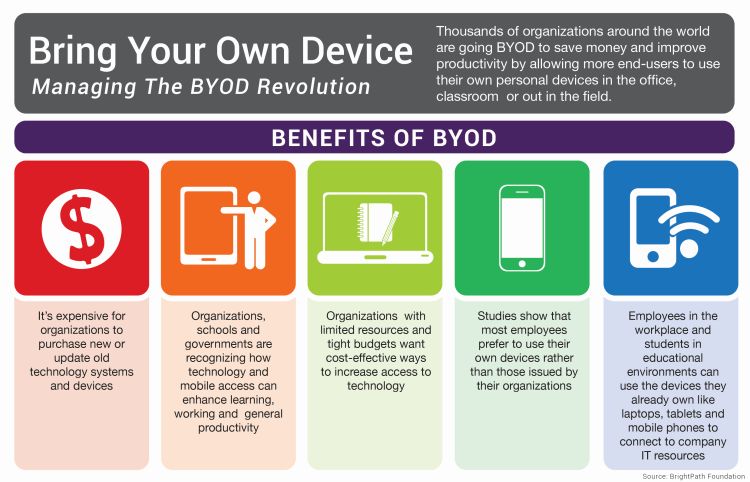
Why Are Businesses Choosing BYOD?
Organizations and businesses throughout the Bay Area have taken note of BYOD’s:
- Cost-Savings Opportunities
- Incorporation of Employees’ Preferences
- Streamlining Potential
- And the Benefits of Greater Flexibility
Before you introduce BYOD into your workplace, it is crucial for your organization to identify, recognize and address the potential impacts of providing full business access on employee-owned devices.
More specifically, this is the time to consider how providing access to your files, increasing the scope of your data security responsibilities,and how introducing unintentional side effects could affect your business, your operations and even your clients’ experiences.
How to get started: Proactively implement policies and procedures to govern their use from the very beginning.
Think of it this way, you want the tracks in place, headed in the right direction before you start running the train.
Why Do We Need An Official BYOD Policy?
It’s hard to remember, but small details such as not saving work login credentials may seem obvious to one user, yet could easily appear completely harmless to the next.
Without the context provided by employer education or at the very minimum, a BYOD Policy (and possibly Mobile Device Management, or MDM Policy), what at first seems like a simple, seamless transition can accidentally spin out of control into a company-wide data breach or worse.

But IT Security Is Simple! It’s Common Sense, Right?
What starts out as a small concern can easily go undetected and spiral out of control when well-intentioned yet uninformed users are behind the wheel.
It’s Hip to Be Square: While standard company issued laptops or PCs may scream Office IT and lack the “sexiness” of your personal top-choice device, there’s a reason corporate devices exist.
The effects of simple “ut oh” mistakes from well-intentioned yet uninformed users are exponentially magnified as soon as devices with unstandardized configurations, a hodgepodge of unapproved softwares and unknown applications gain access to your computer network, services or advanced IT management solutions.
Why Standards Matter

When your configurations and installations are completed on-the-go, whenever a user sees fit, it’s common for key security safeguards such as antivirus installations and regular updates to fall through the cracks undetected.
You may get lucky and manage to skirt problems in your day-to-day business, but as soon as an attack slips through, you’re suddenly trying to put out a five-alarm fire with a garden hose…
When it comes to BYOD, your employees have the capacity to make decisions which can have far-reaching (and sometimes unintended) consequences.
For example, if one of your veteran employees just purchased a brand-new MacBook Pro…and for convenience…and because they like it more… they started bringing that laptop to work.

That same employee has been thoroughly enjoying having all of their work files, credentials, and possibly even sensitive client information that they need to complete their job…
Fast forward, and now it’s Monday morning.
- That same employee is frantically telling you about how they were tying up some loose ends over the weekend…
- They were just a few steps away from their table, ordering another coffee, when a thief ran by, scooped up their beautiful new MacBook, and ran
- They can’t believe it, happened right in the middle of working- fully logged in, device unlocked, and with a report containing secured client information open.
Soon it starts to sink in… All of the project details, sensitive client information and even the small quick-reference workbook filled with your company’s account logins have been compromised.
But My Employees Would Never Try to Harm Us!
Clearly not, you trust your team, and you’re worked hard to find the right people for your Bay Area business.
When BYOD fails, it’s usually obvious there was no malicious intent, just like scenario above. (And in the rare instances where malicious intent is at hand, a conversation on “social engineering” and “insider attacks” would be necessary.)

Yet it’s simple, unplanned events such as these which can leave you fighting to protect the precious intangibles of your business such as client trust and confidence in your capabilies as well as their security.
This is exactly why BYOD Policies are crucial. When employee owned devices are not fully discussed, their access levels examined and their rights agreed upon, the “grey” area becomes a danger-zone. .
No matter how detailed, well thought out and comprehensive a policy document is, if users don’t understand or don’t care or know it won’t be enforced, a BYOD policy becomes useless.
How Do I Set My Business Up For BYOD Success?
When you have expert resources, make sure you use them!
You know the ins and outs of your organization’s operations, but when it comes to the details of your business network and advanced technology solutions, make sure you collaborate with your IT services provider to construct practical, easy-to-understand, and simple-to-enforce policies.
By working together you can make sure that:
- Proper IT security measures are being put in place
- They are crafted to be as user-friendly as possible from an end-user’s perspective
When your Bring Your Own Device guidelines and policies are easily understood, well-explained, and consistently enforced, you can rest easier knowing that you have set your users and your business technology solutions up for success.
If you’re considering implementing BYOD in your workplace- Don’t wait, get started building a strong foundation for your business IT today!




