Latest News and Resources
Office IT Tips: DIY Simple Internet and Router Troubleshooting
Simple Internet and Router Troubleshooting: DIY Tips for the Office
Modern information technology is a wonderful thing – that is, as long as it’s working. When it fails to do so, the results can range from a bad case of nerves to lost revenue for frustrated business owners.

Fortunately, many computer-related maladies are fairly easy to fix. With that in mind, here are some simple Internet and router troubleshooting tips:
1. A new router fails to connect to the web
While this has many possible causes, a surprisingly common issue is that the modem is still attuned to the old router. To solve this issue, disconnect the network and power cables from the modem and from the new router. Leave everything alone for 30-60 seconds. Then reconnect the wires to the modem and wait until the little light that says WAN/Internet is burning. Then reattach the router cables, switch the router back on and try surfing the net.
2. Internet connection is spotty or non-existent
As with the previous issue, this can be caused by numerous problems, including overheating. To find out if this is the problem, simply place your hand on your router. If it feels uncomfortably warm, then move it to a spot where it gets plenty of airflow; you may even want to unplug it for a while to let it cool. If it works fine afterwards, then keep it in a well-ventilated location going forward.
3. A wireless connection runs slowly or frequently fails to work
Often a poorly placed router is the cause of this problem. All sorts of things can interfere with wireless signals, including brick and concrete walls, electrical wiring and other electronics. Try moving the router to a different room or, if that’s impractical, to a higher spot near the same location. You can also try moving your computer closer to the router.
One common yet unexpected office IT obstacle can stem from having your office microwave located too close to your business technology equipment. If you have a microwave in your business, make sure it is properly stored away from your wireless router if at all possible! If any of these steps help to solve the issue, then you’ve found the root of the dilemma.
4. Your Android tablet won’t connect to your network
With more and more people using mobile devices these days, this is an especially common issue. One quick fix that often does the trick is to go into your system settings, find the network to which are trying to connect and choose the “forget” option. Then try reentering the network password. This causes the system to flush out old, obsolete connection information.
5. Your wireless printer won’t connect to your network
The culprit might be your security suite. You might need to configure its settings to allow the printer to work. Avoid disabling the suite, however, as this may expose your system to malware.
If you’ve gone ahead and tried each of these simple Internet and router troubleshooting tips but find that they don’t take care of your office technology problem, then you may benefit from partnering with professional IT services support specialists.
When you have a dedicated team on your side, identifying the root causes of your technology issues is suddenly a priority and gets you on the road to keeping your business operations running smoothly, reliably and to maximizing office productivity. Contact us today to schedule your free business consultation and get started identifying the best options for your business!
Read More6 Ways Professional IT Support Helps Your Business Succeed
6 Benefits of Outsourcing IT Services
Modern information technology (IT) is both amazingly useful and annoyingly imperfect. Computers freeze, connections go down and viruses infect. When these problems occur, having the right IT professionals can make the difference between a minor bump in the road and a crisis that threatens your company’s ability to survive a disaster.

As you research your options and consider how to best meet your IT needs, here are six of the most common reasons Bay Area businesses choose to entrust these key responsibilities to a dedicated professional IT support firm:
1. To level the playing field by harnessing the power of seasoned experts
Everyone knows that major players like GM, eBay and Amazon have the best IT professionals money can buy. This can create disadvantages for smaller firms that must make every dollar count. One way to even out the odds is to work with an IT services provider.
When it comes to diagnosing technology issues, experience in the field can be equally if not even more important than formal training or job title.
If your company depends solely on a limited (often times single) internal resource, as soon as that person is tied up, all of your other technology needs get pushed to the side where they rapidly start piling up…Soon enough, your users learn that whenever they have an IT problem, they are better off trying to fix it themselves (which opens the door to a whole host of new problems).
Instead of struggling each time your office technology starts having problems, you can turn this fact into an advantage by outsourcing your help desk support to a team of experts.
2. To enjoy the cost savings that come from economies of scale
Over the years, many clients who choose t
o work with external IT consultancy services have found that it is actually often more cost-effective than handling technology management in-house.
When you eliminate the need to source, screen, interview and vet candidates, you eliminate the time, cost and anxiety associated with struggling to find the best technicians possible for your available budget.
Instead of struggling to onboard a new technical employee, working with a it managed service provider allows your organization to save time, money and internal resources to help free up capital that’s needed elsewhere, thus enhancing efficiency and profitability.
3. To focus on your core competencies
In today’s business world, it no longer makes sense to be a Jack or Jill of all trades. Letting others handle your IT support services can enable you to concentrate on what it is that you do best, whether that’s providing the best care possible to patients within your healthcare practice or providing financial services to clients seeking to plan for the future in the San Francisco Bay Area.
4. To enable implementations of cutting-edge technology
Not only does outdated technology limit your productivity, it can even pose a threat to your business operations and cybersecurity.
Some enthusiasts would even argue that yesterday’s technology is nearly as useless to a modern enterprise as stone knives and smoke signals, but the right managed service provider understands how to take the specific needs of your business into account and to help facilitate the transition from legacy systems to the latest technologies.
Yet finding and hiring the right specialists with the requisite knowledge could take weeks or even months by using an in-house approach. You won’t have that worry when you outsource your IT services to a local IT support firm- a dedicated managed services provider takes pride in helping your company stay on top of the latest technologies and guides you through selecting the best solutions to meet your office and business technology needs.
5. To enjoy the benefits of ongoing relationships and deep understanding of your needs without the HR headaches
Hiring, training, onboarding and otherwise investing in new employees is always a gamble- Perhaps they will work out, perhaps not. Even when your new hire has the technical skillset necessary to complete their job responsibilities, there are a number of variables which can pose a threat to your success. Personality and corporate cultural fits, work ethic and management requirements, or even external influences such as staffing during an unexpected departure or employee illness can leave you unexpectedly stranded/ high and dry. You can avoid these uncertainties by letting trained specialists take care of your IT needs.
6. To enable you to conserve your mental energy
If you’re looking to improve the quality of your worklife and up your office productivity, get started on the path to progress with a free network assessment today.
How Healthcare BYOD Policies Affect Network Security
How Healthcare BYOD Policies Affect Network Security
Healthcare organizations
Simultaneously, technologies are also evolving in
Capability and Efficiency
Actual bandwidth requirements depend on several factors such as the location, number of users, real-time
Protect Your Network
A
Segment Your Network
Isolate the Electronic Health Record system on the network along
Detect
Install an intrusion detection system as it will drop
Audit Your Setup
Workstations accessing the EHR system must comply with
Review All Privileges
Manage user rights centrally and
Conclusion
Although HRSA does not mention
HIPAA Audits – Not as Bad as They Sound with the Right Healthcare IT Support Services
How to Show HIPAA Auditors Your Practice’s Good Faith Effort
Since the enactment of HIPAA in 2003, patient privacy has continued to be a priority for the federal government. To ensure compliance, the Office for Civil Rights (OCR) is performing a series of on-site and desk audits. Desk audits can be particularly tough, as auditors leave little time to comply with audit information and develop appropriate policies or conduct a comprehensive risk assessment. With entry-level HIPAA violations starting at $200,000, practices need to have policies in place is before an audit occurs.

What Auditors Want
Like their IRS counterparts, HIPAA auditors are looking for a good faith effort to follow the law. They’ll ask to see a comprehensive risk management procedure that outlines how each potential risk is handled. In addition, they’ll assess your breach policy, including how patients and the media will be advised of a potential data breach.
Finally, auditors will ask for complete documentation of all training for HIPAA compliance. HIPAA training, in their eyes, is not a single event, but continuing education.
Best Practices to Pass an Audit
Before you are notified of an audit, perform a risk analysis. Take into account all factors concerning HIPPA auditors—listed below—while performing your risk analysis.

Proper Documentation
Document the practice’s plans for data management, security training and notifying patients in the event of a data breach. These plans should be in writing and available for an auditor’s review.
Password Security
Keep a secure password policy. Passwords should meet security standards and not be stored where they are easily accessible.
Proper Encryption
All Protected Health Information (PHI) must be encrypted. Scans and images must be encrypted when being sent or received, as well.
Use SSL for Electronic Health Records
All electronically-transmitted PHI or EHR data, like test results or scans, must use SSL when accessed via the internet. Since most practices can access patient data from hospitals, SSL is vital.
Designate a Security Manager
Each practice should have a point person who acts as the security manager and is responsible for the encryption techniques. One or two additional staff members should also be familiar with the encryption in case the security manager is unavailable.
Use VPNs to Access Patient Data Remotely
Any staff member who accesses patient data remotely must do so over VPN (Virtual Personal Network) to ensure security outside the office environment.
Make and Practice a Disaster Recovery Plan
A disaster recovery plan must be documented and should be practiced at regular intervals.
Sources:
Get the IT Support Your Bay Area Practice Needs
Your Bay Area Medical Organization Needs Healthcare IT Pro Services

Professional IT support is a valuable investment for any business, but it is an especially important consideration for healthcare providers. Given the healthcare industry’s reliance on computer systems and the sheer amount of highly sensitive personal data healthcare practices retain, technical support is necessary for a secure and efficient office.
Security
Professional IT support offers many direct benefits to healthcare providers. Arguably, one of the most important components of your office technology support it IT security. Data breaches are a very real and increasingly common threat. Statistically, the vast majority of medical practices, regardless of size, area or specialty, will experience at least one data breach. Nearly half will suffer five or more instances of data theft. Given highly sophisticated theft methods and the vast amount of electronically-stored data, IT support is not an option, it’s a necessity. Professional technology support can customize security options for your office. Should a breach occur, IT will move quickly to neutralize the threat, restore operations and reduce damage.

Support
Computer systems, particularly those powerful enough to carry a medical practice, require maintenance, updates and repairs, all of which are time consuming and often frustrating. Should a system fail, even briefly, it may be difficult or impossible for a practice to continue until it’s fixed. By retaining support, offices have the assurance that IT professionals will respond quickly. This results in drastically reduced system downtime, which directly increases the office’s performance and efficiency.

Reliability
Solutions provided by professional IT Support are reliable. Whether tech support works with your practice on security issues, system performance, your network, database assistance or storage, professional IT support will work to develop the best solution for you. IT professionals will provide necessary support to ensure operations run smoothly.
Having local Bay Area IT support on-call significantly reduces the strain on doctors and staff, which results in more time with patients, more energy and effort to direct into the practice. This means increased efficiency and overall improved productivity as well. Not only do IT professionals assume a frustrating and time-consuming burden, they provide peace of mind, ultimately allowing you to spend your time providing care to your patients.
Read More3 Considerations for Choosing an EHR System that Works for Your Practice
3 Considerations for Choosing an EHR System that Works for Your Practice
IT Collaboration
Survey the Practice
Deployment Concerns
The shift from
HIPAA Healthcare IT: Protect Patient Privacy Using IT Support Services
Using IT Services to Conform to HIPAA Reqs and Protect Your Patients’ Privacy
On average, two million Americans face medical identity theft each year, costing U.S. healthcare organizations an estimated $41 billion [1]. Healthcare practices are finding it increasingly difficult to comply with patient privacy regulations. After the enactment of the HIPAA Privacy statute in 1996, there have been several regulations regarding patient privacy: HITECH, ARRA Meaningful Use, and the Omnibus Rule.

Patient privacy breaches attract severe penalties, both criminal and financial, along with harm to reputation. When the stakes are so high, a solid foundation is necessary — involving policy, procedures and technology — for ensuring patient privacy throughout the healthcare organization.
Top Challenges in Securing Patient Privacy Data
Although healthcare is the most regulated industry in the US today, in order to comply with the strict regulations and for avoiding stiff penalties, healthcare organizations face three primary challenges in protecting patient data. Every access to patient data must be logged — this is a HIPAA requirement. Massive volumes of access records are generated and need to be audited. Lastly, diverse data needs to be consolidated.
A Three-Step Methodology Can Lead To a Solid Foundation
As patient privacy compliance program [2], such as the Healthcare IT Support Services from Bay Computing in the San Francisco Bay Area, can provide a solid foundation and reduce the risk of a data breach with the following three elements:
1. Defining Appropriate Policies
When healthcare practices accept principles regarding patient privacy, those are reflected in their policies. These help establish a culture and expectation binding all stakeholders, including the doctors, office managers, and decision-makers of small to mid-sized practices.
2. Setting up Suitable Procedures
To enforce the policy, healthcare practices need suitable processes for developing, documenting, implementing, and communicating procedures. Mostly this involves defining who can access what data [3].
3. Using Current Technology
Tasks that cannot be addressed manually need to be handled with technology and this must be augmented in the procedures by IT support. As appropriate technology allows automatic monitoring of patient privacy data access, healthcare practices can be free of the limitations of random and manual audits.
Conclusion
Located in the San Francisco Bay Area, Bay Computing helps healthcare providers succeed by providing comprehensive, accessible and readily available healthcare IT support.
With IT services that focus on providing your users a great helpdesk and technical support experience, your patient care providers can now take advantage of your existing IT investments to satisfy increasing demands while observing Meaningful Use, navigating any new implementations following HIPAA Compliance Assessments, and any other number of industry requirements.
Ready to get started? Contact Bay Computing today and receive a free onsite network assessment!
References:
[1]
https://www.experianplc.com/media/news/2012/more-people-aware-of-medical-identity-theft/
[3]
http://fas.org:8080/sgp/crs/misc/R40599.pdf
The Benefits of a Hybrid Cloud Environment
The Benefits of a Hybrid Cloud Environment
If your business has all its mission-critical hardware located on-site—with applications installed directly on local workstations or through on-premise servers—it may be time for a change. This setup is becoming increasingly rare these days for many reasons including; heavy upfront costs, redundancy concerns, physical security issues and the overall cost of maintenance.
What is the Hybrid Cloud?
Why You Should Consider the Hybrid Cloud
Unlike a complete cloud-based infrastructure, hybrid clouds allow access to on-premise hardware. You can deploy virtualization solutions to emulate cloud-based resource sharing or use your on-premise hardware normally.
Switching from a completely on-premise infrastructure to a hybrid cloud infrastructure can be as simple as incorporating cloud-based applications into your regular workflows. For example, cloud-based email and video chat services can serve as a natural starting point.
The scaling benefits of hybrid cloud computing are particularly useful if you publish a lot of media, especially videos that have viral traffic-potential. It’s not feasible to keep enough servers on-premise to handle peak demand when your typical usage is minimal. A cloud-based content platform can seamlessly scale your capacity to handle the additional load without incurring the heavy equipment costs of traditional infrastructure upgrades and setups.
How to Deploy a Hybrid Cloud
It’s important to consider how your on-premise hardware and cloud-based services are going to integrate. Setup and maintenance can get complicated when you add development platforms, hosting, data storage and other services. Even Forbes ended up asking, “What’s Right For Your Business?” in a recent article examining private, public or hybrid cloud computing.
Maybe your IT department is overloaded and is in desperate need of extra help, or maybe your offices doesn’t have a dedicated IT staff- No matter what your office environment looks like, working with a SF Bay Area IT services firm gives you the expertise required to roll out—and maintain—a hybrid cloud that will improve your business infrastructure and help expedite your daily operations.
Put your on-premise hardware to the best use possible while taking advantage of cloud-based perks with a hybrid cloud system. Add in an IT support team with hybrid cloud experts and you have an excellent foundation for kick-starting your business growth. Get in touch with Bay Computing’s implementation specialists and get your free onsite network assessment sscheduled today!
Read MoreTop 10 New Features of Windows 10 for Your Business Users
Top 10 New Features of Windows 10
Released in July 2015, Windows 10 has many new features as compared to Windows 8. From the reintroduction of the Start menu to windowed Metro apps, here are the 10 top new features to watch out for in Windows 10.
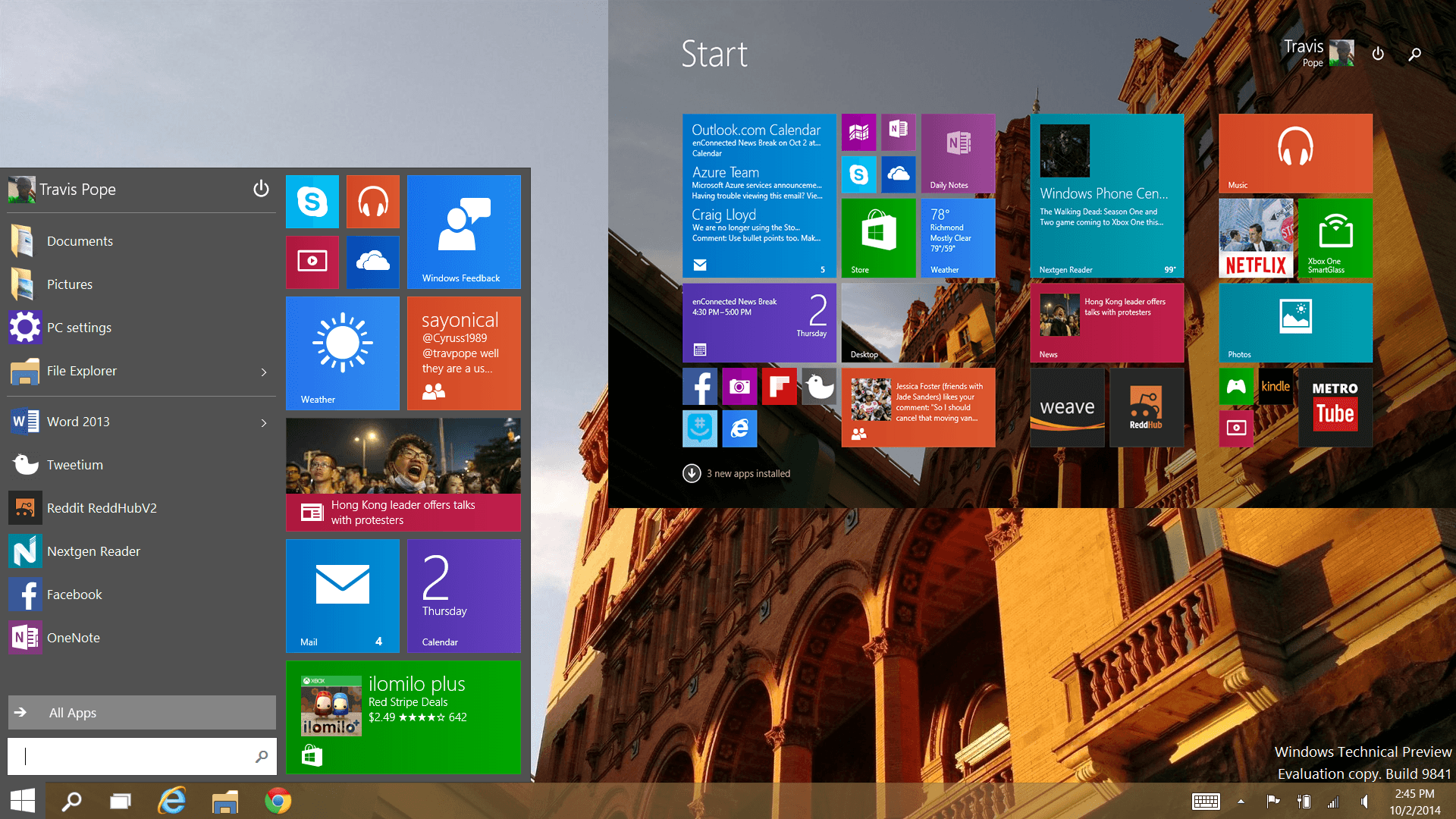
1. Start Menu
The Start menu is back in Windows 10!
Simply click on the Windows icon in the lower left corner of the desktop to view installed programs and search for files.
By default, the Windows 10 Start menu features Live Tiles, similar to the Start screen in Windows 10, but there is an option to turn them off.
2. Windowed Metro Apps
Metro apps have been updated to better meet the needs of desktop users in Windows 10.
Whereas Windows 8 forced desktop users to open Metro apps in full-screen mode, Windows 10 opens them in windows that can be resized.
3. Action Center Notifications
Windows 10 features a centralized Action Center, which uses popup notifications to help you keep track of your important office reminders, lateste messages and time-sensitive deadlines.
Instead of having key information fall through the cracks on a busy day, the Windows action center is a great tool to help out your business organization. You can also use the Action Center to quickly toggle Bluetooth or Wi-Fi on and off, just as you would on an iPhone or Android phone.
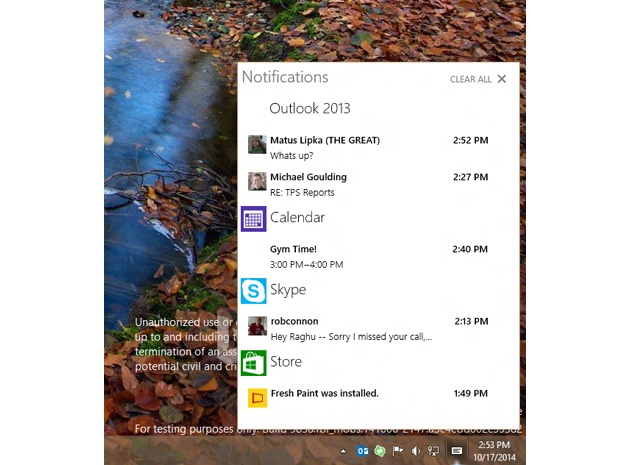
4. Cortana
Windows 10 brings Cortana, the digital assistant from Windows Phones, to desktop users. Cortana is able to quickly find information online or on the computer’s hard drive. As with the virtual assistant on the Windows Phone, you can talk to Cortana using natural language, such as “Find me the photos I took in January.”
5. Project Spartan Browser
Microsoft has finally provided an alternative to Internet Explorer. Windows 10 features Project Spartan, a browser that is built for speed and compatibility with the modern Web.
6. New Mail App
Windows 10 features a new and improved Mail app, which is much faster and more responsive in comparison to the Windows 8 version. If you’re using the Mail app on a touchscreen laptop or tablet, then you can use customizable swipe gestures to move through your emails.
7. Virtual Desktops
Organize your apps into virtual desktops, which you can easily move between using Alt+Tab. It’s an easy way of organizing all your apps and windows into an arrangement that works for you.
8. Improved Windows Explorer
Windows Explorer has been upgraded for Windows 10.
There is now an easily accessible list of the folders you regularly visit on the left of the panel, along with a list of your recently opened files readily avaialble.
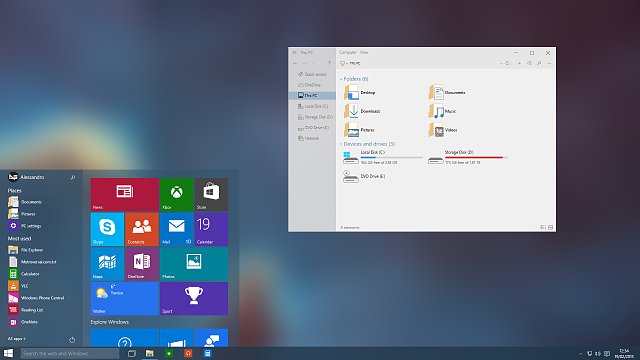
9. Continuum
Using Windows 10 on a touchscreen laptop? Thanks to the Continuum feature, you can easily switch between desktop mode and a swipe mode that’s suitable for touchscreen use.
10. Single Settings Menu
You can now manage all your Settings in one place, rather than having to use the two separate Settings menus for Metro and Desktop interfaces on Windows 8. Access the Windows 10 Settings menu from the Start menu.
Read MoreThe New Office Monster…HIPAA
Your Office’s Latest Challenge…HIPAA Compliance

The Health Information Portability and Accountability Act, otherwise known as HIPAA, may be the new the headache of every cybersecurity professional who deals with HIPAA customers.
To understand the headaches often associated with HIPAA compliance, you must first understand what HIPAA is.
Personally Identifiable Information Regs
This federal law protects an individual’s personally identifiable information (PII) by setting administrative, security and technical standards and safeguards nation-wide. Those who collect, process or use the data must ensure it is reasonably protected, and the same rules apply to everyone in the health care industry.
Companies or organizations that deal in HIPAA data are known as Covered Entities and Business Associates, and they are required to have your written consent to use PII data. Among all the paperwork you sign when you go to a hospital is a HIPAA agreement.
How HIPAA Affects Security
Security measures such as restricting access to HIPAA-related data, locking individual workstations and requiring employees to wear ID badges are expected to be followed.
Being HIPAA compliant is more about standards and practices then it is about a specific cybersecurity tool.
HIPAA compliance includes methods of restricting physical and digital access to the data, proper log management, contingency planning, appropriate training and valid incident response plans.

Why HIPAA Compliance Can Be A Headache
Protecting PII seems like a reasonable request for any organization that consciously agrees to work in the healthcare space.
The headache for many businesses and providers comes from the fact that the standards and practices are meant for everyone in and associated with the organization, not just those directly handling HIPAA data.
The security standards for HIPAA compliance are strict, with infractions carrying hefty fines from the Department of Health and Human Services.For example, in a HIPAA-restricted workplace something as simple as forgetting your employee badge could potentially get the organization fined thousands of dollars.
Also, organizations claiming HIPAA compliance are subject to random auditing from the Department of Health and Human Services, so standards must be followed at all times.
For organizations striving to become HIPAA compliant, the challenges of implementing and maintaining proper patient confidentiality and information security stems from the classic battle between convenience versus security. Unfortunately, without the right guidance, office procedures and Healthcare IT services solutions, convenience often wins.
If you’re looking to get started tackling the technical challenges of bringing your organization into compliance, contact your local Bay Area healthcare technology team for your free network assessment today!
Read More
