Latest News and Resources
How An Excellent IT Workflow Will Keep Your Business Running Steady
Elect
Hire
Why
iPhone, iPad and iOS Fall Victim to YiSpecter Malware Attacks
Everyone was YiSpecter Fighting, Those Hacks Were Fast as Lightening
Your “how to” blog post should teach the reader how to do something by breaking it down into a series of steps.
Begin your blog post by explaining what problem you are going to solve through your explanation and be sure to include any relevant keywords. Add in a personal story to establish your credibility on this topic. And make sure to end your blog post with a summary of what your reader will gain by following your lead.
Need some inspiration? Check out these “How-To” examples from the HubSpot blog:
- How to Write a Blog Post: A Simple Formula to Follow
- How to Do Keyword Research: A Beginner’s Guide
- How to Write an Effective Meta Description (Yes, They Still Matter)
BODY:
Now deliver what you promised in the first section. This is the longest part of the post, so make it easy to read. Use short paragraphs, bullet lists, and bold headings to set different sections apart.
Some common section headers include:
Step 1: Getting Started
Step 2: Do Your Background Research on…
Step 3: First Steps for…
Step 4: Analyze and Repeat
Step 5: Wrapping Up
You can use bulleted lists, numbered list, or multiple headings. Include as many steps, numbers, or bullets that will allow you to discuss your topic thoroughly.
Here are some pointers to make the best possible body of your blog:
- Include visuals
- Include short explanatory phrases in your headers
- At the end, transition into your conclusion
CONCLUSION:
Now it’s time to say goodbye and wrap up your post. Remind your readers of your key takeaway, reiterate what your readers need to do to get the desired result, and ask a question about how they see the topic to encourage comments and conversation. Don’t forget to add a Call-to-Action to turn your blog post into a marketing machine!
Congratulations! What a lovely how-to post you’ve created.
Read More
Experts Finding Malware Creativity Advancing Faster Than Ever
Experts Finding Malware Creativity Advancing Faster Than Ever
How many technology solutions does your business rely on? Integrated software packages, softphone-based VoIP systems, productivity enhancing smartphones — technology has transformed workplace productivity, but it comes with a dark side. Malware, which is malicious software such as viruses and trojans, continue to be a major problem. One anti-virus software company detected 2,205,858,791 attacks in Q1 2015.

As more businesses gather sensitive data stored in on-premise and cloud-based tech solutions, the malware attacks become more sophisticated. User computers, network infrastructure, and mobile devices are all viable attack vectors for a creative cybercriminal. Once your computers get infected, the direct and indirect costs can be enormous, and you might not even know how the malware got in. Here are two of the most creative, and most dangerous malware threats to the business world.
Cryptowear
What would happen if you lost access to mission-critical parts of your business system for a day? A week? Cryptowear is one of the latest malware trends. It locks down essential parts of a system and demands payment before you can use the system normally again. In many cases, these applications look like legitimate software prior to launching the attack. If you don’t pay up, you’re going to need to go through a lengthy backup restoration process to get everything back to normal.
Malware App Mods
Does your business have a bring your own device (BOYD) policy, where employees can use their own personal mobile devices for business purposes? If you do, you could be inviting all manner of malware into your network. One of the latest mobile malware trends are apps that offer modification or cheat codes for popular mobile games. The user downloads and installs the mod app, which actually contains malware. If it’s not detected early, the infection could end up hitting your entire business network.
How to Protect Your Business From Malware
So how do you stay a step ahead of the cybercriminals? The right IT security safeguards and solutions go a long way to staying on top of potential attack vectors. A technical support provider gives you the ability to use your resources to get the knowledgeable help you need to handle IT security issues.
Need help with keeping malware from ruining your business? Contact us for all your Bay Area IT services needs, whether you’re fighting an active malware infection or you want to proactively handle issues.
Read More3 Ways to Grow Your Business With IT Services
Want to kick-start new business leading into 2016? Enable growth with best-in-class technology and IT Support Services
42 percent of small businesses have no IT department, yet many of these businesses rely on technology-based solutions to fuel their future growth. Without dedicated IT professionals, business owners or other critical personnel are regularly pulled away from their core business responsibilites to address ongoing IT issues.
Your business can’t grow if you’re constantly running around and putting out fires, but you aren’t at the point where your budget supports having a full-time technical staff. It’s time to consider the ways San Francisco IT support helps your business grow over the long term.
1. Cost-Effective Technology Procurement
You know what processes you deal with on a day-to-day basis, but you don’t have time to read up on every technology business solution available to figure out which options make the most sense for your company.
If you sit down to do the research yourself, you take time away from your actual business duties. IT Services Bay Area helps you identify your business work flows that benefit most from technology, locates the best vendors for these options and helps you with the procurement and deployment process.
Think of the IT service as a trusted friend who knows all about the hottest restaurants in town, and exactly what to order off the menu to suit your tastes.
2. Proactive Maintenance
You don’t think about what could go wrong with your IT infrastructure—until it’s your busiest day of the year and all of your mission-critical business systems are down. Instead of ignoring small problems until they snowball into major blows to your business growth and finances, using IT services for proactive maintenance keeps your infrastructure stable and strong. If you take your car in for its regular oil change, why wouldn’t you get systems looked at when they’re critical for your business success?
3. Leveraging IT Expertise
Let’s face it: As a business owner who isn’t working in a technology sector, you don’t have time to stay up to date with IT best practices, the latest threats, company-changing innovations and other tech-based business intelligence.
You need the ability to put this information to use to stay competitive without dealing with the overhead costs associated with brining on a full-time IT employee. Some days you only need simple troubleshooting, other emergencies may require a full technical support team.
When you partner with a Bay Area IT support services provider, you leverage their entire team’s expertise so your business stays on top of the latest threats and trends, and is provided with a cost-effective method of handling your IT needs and creating a solid foundation for your future business growth.
San Francisco IT support goes far beyond simply providing helpdesk technicians to fix technical problems as they occur. With the right managed services provider, your organization helps you design, implement and create a technology foundation for fueling your business success.
When you keep your IT systems healthy and functioning at peak performance, you continuiously build upon your competitive advantages and improve your opeational capabilities to help blow your completition away.
Read More5 Pervasive Myths About Cloud Computing
Businesses in the United States spend well over $13 billion each year on cloud computing services. As “Cloud” picks up steam as the latest buzzword, migrating to the cloud is no longer an expensive, risky venture reserved only for major enterprises.

With prices continuing to drop as the technologies develop and mature, the latest studies are finding that companies with fewer than 19 employees are now 20 times more likely to adopt cloud technologies than their larger competitors.
The Lay of the Land
The hybrid cloud, a mix of public and private cloud computing options, is a new choice that’s growing quickly in popularity. Gartner predicts 50 percent adoption by 2017 of this flexible and secure option. Despite the fact that cloud is a quickly growing choice, there are some pervasive myths surrounding it:
1. The Cloud Is Insecure
Modern organizations are rightly concerned about cybercrime leading to costly data breaches. However, Gartner highlights that the idea that cloud is less secure is based on a “trust issue,” and not necessarily fact.

As with any other major technology investment, when considering cloud services, proper due dilligence is necessary to confirm that appropriate security has been implemented. That being said, many cloud providers are not only aware of common information security concerns, but proactive in their approaches to cybersecurity.
In many cases, as an additonal assurance to their customers, cloud providers will voluntarily undergo a number of industry security and compliance audits, such as PCI-DSS and SSAE 16 SOC 1 and SOC 2.

Furthermore, for those companies who feel more comfortable with a tighter control over their organization’s security, it should be noted that both cloud computing and hybrid cloud solutions can provide critical protection for small and medium-sized businesses (SMB).
2. Cloud Solutions Are Inflexible
There are some cloud vendors that are highly inflexible; these companies may demand high penalties for service termination or upgrades. However, writer Chris Quinn reports that a large percentage of companies are turning to hybrid solutions to ensure flexibility.
This provides the choice to “deploy and consume” as needed in combination with more traditional solutions. In many cases, San Francisco and Bay Area offices have found hybrid options to offer the “best of both worlds.”
3. The Cloud Is Virtualization
Virtualization can be used to provide cloud computing, but they’re not one and the same. The cloud can offer distinct advantages, including automated management, distributed control, and scalability. Additionally, there are certain security and end-user benefits tied to the cloud above virtualization, making it a more popular choice for both SMB and major enterprises.
4. Cloud Implementations Are Painful
Much like any technology solution, cloud implementations have both pros and cons. Companies that opt to entirely outsource their cloud to an out-of-the-box solution are dependent on their vendor’s support (or lack thereof), rely on vendor security measures for protection, and may face uncertain periods of downtime. Depending on the solution and organization selected, being locked-in long-term to a suboptimal solution can accidentally become your reality.
However, there are significant advantages to cloud implementations, which can include increased storage capacity, efficiency gains, and cost savings.
By working with your IT services provider, your organization has easy access to dependable cloud computing technical support while also having the advantages of cloud technologies at their fingertips. With the right technical support team, implementing cloud-based technologies can be far less painful than you have ever anticipated.
5. Working With the Cloud Must Be “Mysterious”
Many people who are new to cloud technologies believe that incorporating cloud options translates into an automatic lack of transparency.
But hybrid and private cloud deployments can offer total transparency to users, particularly when technology teams work with your organization’s office end users to help them understand their technology infrastructures clearly and fully.
Are You Accidentally Violating HIPAA Regulations?
In a busy medical office, it’s hard to keep track of each and every HIPAA regulation, and accidental HIPAA violations can easily occur.
In many cases, practices discover multiple violations in place upon beginning compiance examinations before you or your users even realize you’ve done anything wrong.
Unfortunately, violations can lead to stiff fines if you’re caught breaching regulations. Every year, the U.S. Department of Health and Human Services receives approximately 4,000 complaints about HIPAA violations. Make sure your office isn’t on the list by avoiding these common HIPAA related “trouble areas.”
Accident #1: Exposing Confidential Information to Other Patients
Although everyone in your office understands it’s important not to discuss one patient with another or provide information to a family member without a signed release form, your team may not realize just how easy it is to accidentally expose protected information with the next patient in your exam room or even the entire waiting room.
Keeping patient information private requires scrupulous attention to the way your entire office handles files and all possible forms of patient information.
It’s easy to say, but harder to remember: Don’t leave anything containing Protected Health Information (PHI) unprotected where other patients can see it, and always sign out (or lock) any computer screens that contain patient information before showing the next patient into an exam room.
Keep in mind, even simple info such as addresses are considered private information. It’s far better to ask patients to review forms than to rattle off an address to verify if the one listed is current.
Accident #2: Neglecting Your Computer Network
Patient records are a treasure trove of information for identity thieves and cybercriminals. Once they hack into your system, it’s game over.
In one fell swoop, the bad guys suddenly have unlimited, centralized access patient names, addresses, social security numbers and credit card information.
Your firewall stops thieves from accessing your system, but no firewall can do its jop properly with its hands tied (AKA when it isn’t kept up to date.)
Make sure your IT services resource sets your network firewall to receive automatic updates and regularly monitors and checks your log files for signs of attempted intrusions.
From there, make sure your office team doesn’t ignore alerts and any time you suspect a breach, reach out to your managed services provider follows HIPAA reporting procedures for any computer breaches if your office falls victim to a malicious attack.
Being Lax with Your Laptop
Thanks to your laptop, you’re no longer chained to the office computer. Now you can take your work home with you and not miss out on family time!

That being said- No matter the setting, you must stay vigilant and make sure to not let a relaxed family setting lull you into being careless. After all, ePHI is still protected by HIPAA, be it at the office or inside your home.
It may seem simple, but it is imperative that you do not leave information on your screen, even if you’re only leaving the room to get a glass of water.
Password protect your laptop, close out all screens and tabs when not in active use and make sure to keep your computer locked away when it is not in active use.
More specifically, with the increasing rates of automobile theft in the San Francisco Bay Area, save yourself the time, money and headache of having to file a technology incident report andmake sure you do not leave your computer unattended in your car.
Texting Confidential Information
Texting is one of the fastest ways to share information with another medical professional, but it sends that information into cyberspace where anyone can potentially access it.

Make sure all users know the rules:
-Don’t text unless you’re using a special encrypted program to send texts.
-Only send those texts to other people if you’re positive they’re using the same appropriate program.
By keeping these potential programs in mind and educating your staff about HIPAA basics, you can avoid a costly, and potentially embarrassing, violation.
Read MoreDual Customer Focus – Healthcare IT Best Practices Benefit Patients and Employees Alike
Customer focus and supporting the effective delivery of quality care is the aim of healthcare information technology solutions. However, it can be all too easy to forget that practices have two customer bases to please: employees and patients. As you seek to satisfy the needs of both sides, consider implementing the following healthcare IT best practices.
Mirror Portals
Patient information technology has developed at different rates. In-office computerized patient record systems came into common use years before many practices invested in patient-facing electronic health records. However, when portals are a mix of these two different record systems, communication is made difficult. Care must be taken to align these systems.
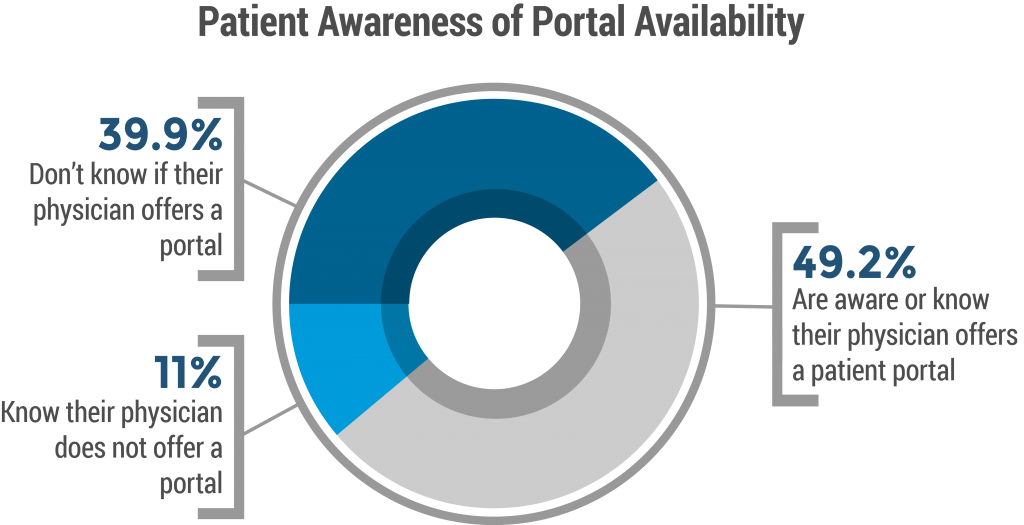
Ensure information like test results, prescribed medications and prior procedures accessible to internal customers—nurses, medical assistants and aides—mirrors information available to patients at home. After all, patient engagement often relies on information availability and transparency, as well as timely communication. Make sure your patients aren’t among the 40 percent of patients who are unsure if their physicians have a patient portal system.
Keep Information Where Your Customers Are
Patients receive information about their health in a variety of media. Most IT-related solutions ensure that data can be accessed through mobile devices, home computers or printed documents. Caregivers also need the same ability to access information to respond to patient queries quickly.
Consider how much time can be saved if an out-of-office practitioner can access a secure patient snapshot and answer a simple question. Now, the issue doesn’t need to be elevated, diverted or put on hold until Monday. Easy access from anywhere also ensures that information sharing isn’t subjected to a gatekeeper. If only one person knows about an issue, other equally qualified professionals are unable to respond if the gatekeeper is out-of-reach.
Respect Your Time and Your Patients’ Time
Precious time is often wasted updating routine health information at the start of appointments. With the availability of next-level technology, instead request patients update their records from home prior to appointments, or during time spent in the waiting room. Practice-supplied tablets can be handed to patients upon check-in, primed to walk patients through a questionnaire. This same software can then alert the caregiver to changes and prompt on-target discussion.

The most beneficial healthcare IT solutions for your medical practice are those that are equally beneficial to both health professionals, caregivers, and patients alike.
From mirrored portals to accessible data and optimized in-office time, by working with the right IT services provider, practices can leverage technology to heighten both patient and employee satisfaction.
Read MoreCoreBot Malware: What Is It, How It Works, How and If It Affects You
Latest Trojan CoreBot Targets Online Banking Sites Malware: What Is It, How It Works, How It Can Affect Your Business
A few months ago, you may have heard about DyreWolf phishing malware scam which specialized in targeting businesses and organizations (as opposed to attacking individuals)…And now CoreBot malware is one of the latest threats to cybersecurity.
The malware got its name from the developer who called the file “core.” The Trojan is delivered through a drop file that leaves as soon as CoreBot is executed on the target machine. The stealer then adds a code to the Windows Registry to stay alive.
The malware can steal passwords, and the modular plugin allows the developer to easily add more functions. CoreBot currently can’t intercept data in real time, but it is a threat to email clients, wallets, FTP clients, private certificates and some desktop apps.
How It Works
First, the malware gets a foothold on Internet Explorer, Firefox and Chrome so that it can monitor your browsing habits, grab forms you fill out and execute web injections. When it detects a relevant website, the form-grabber kicks in to steal your personal information.
The web injections are then activated to display a phishing page that tricks you into supplying additional information. This is when the cybercriminals behind the scam are alerted and take charge of the session in real time by way of a Man-in-the-Middle (MitM) attack.
You are kept busy with a “please wait” message while the hacker connects to your intended destination through a virtual network computing (VNC) module. Once in, the cybercrook initiates new transactions or hijacks the current transfer process to send the money to another account.
How It Can Affect Your Business
So far the victims of CoreBot have been large financial institutions, so your business is probably not yet at risk. If you think you might be affected, contact a technology support specialist in the Bay Area to get started with your free network assessment started for a health-check of your network environment.
With the right strategic San Francisco IT support on your side, not only will you be able to address your existing concerns for your organization’s technological health, but also plan ahead to anticipate, avoid and mitigate any future disasters.
Business tech support firms monitoring botnets see about 60 CoreBot infections every day. Approximately one quarter of the infections occur in the United States, but the malware is also found in the United Kingdom, Russia, Japan, Egypt, Moldova, Taiwan, India and Vietnam.
While data theft can pose a threat to the average end-user, cyber criminals targeting sensitive data and financial information know that the greatest damage can be done when they breach corporate systems.
With that in mind, malware attacks such as CoreBot are only the beginning as cybercriminals seek to gather the data needed to infiltrate organizations and steal valuable information!
Read MoreLatest in Malware: eFast Browser Attacks with False Google Chrome, Traps Users with Adware
Latest Malware Attack Replaces Users Chrome Browsers Entirely by Bunding with Legitimate Software Downloads
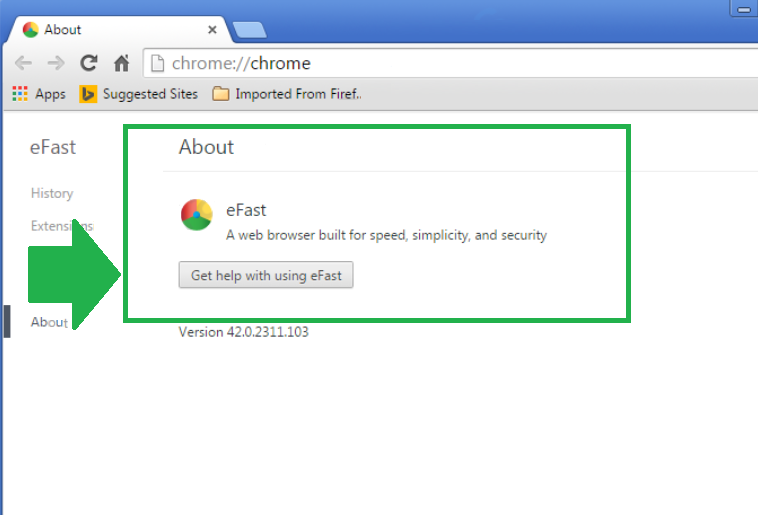
Just last Friday, Malwarebytes announced the discovery of the eFast hijacking scam which boldly attacks by replacing users’ default Google Chrome browsers with eFast, which targets victims with the promise of “A web browser built for speed, simplicity and security”
Suddenly Flooded with Pop-Up Ads? Find yourself constantly redirected to unrelated websites? It might be time to check your Chrome browser …
That being said, the malware attack acts as a stowaway within other software downloads and once it has successfully piggy-backed on a user-generated installation. But what type of installation would this be?
Have you ever had a “security software” offer to install for free or gotten a pop-up “urgent notice” that your machine needed to be scanned ASAP?
Maybe you panicked, and went ahead and clicked “yes” instead of reaching out to your IT services provider to check that the programs were actually legitimate..
What about one of those “too good to be true” free software offers (freeware) which bundle (use bundling) with the original software you were seeking with another offer promising faster online browsing or an enhanced shipping experience? We all know those little check boxes can be tricky…
Forget Taking Over, eFast Eliminates Competition
As business IT advances and office technology users become more savvy, the developers of eFast have made sure to impersonate the genuine Google Chrome browser, with an eye for attention to detail across both original Chrome icons and Chrome windows.
Instead of simply hijacking a browser, eFast specializes in erasing and completely replacing Google Chrome.
By leveraging strong user dependence on browsers and their associated functions, the developers of eFast made sure that escaping wouldn’t be easy.
As soon as eFast breaks in, it deletes all of your desktop shortcuts and taskbars to Google Chrome and replaces them with impostor links and shortcuts. From there, cybercriminals are enabled to hijack your file associations, track each of your keystrokes and and monitor each link that you visit.
![]()
Furthermore, irrelevant of which browser you start out using, eFast is set up to override program viewers for .jpg, .gif and .pdf as well as for protocols such as ftp, http, https and mailto. Basically, eFast and will force itself upon its unsuspecting users whenever they open files…And then the real fun begins as as the malware attack then injects an endless stream pop-us and ads into each of your searches…
While the unauthorized adware can generate profits for malware developers, users must also be aware that a malicious attack easily leaves your passwords, login credentials and banking information vulnerable to exploitation.
Since Google’s Chrome Team Has Been Hard At Work….
Clara Labs, the people responsible for eFast (as well as a variety of other malicious softwares such as Unico, Tortuga and BoBrowser) are now having to up their exploit strategy game with each new development.
As one critic (@SwiftOnSecurity) put it, cybercriminals and hackers are finding that, “it’s getting so hard to hijack… that malware literally has to replace it to effectively attack.”
If You Suspect You’ve Been Hit By eFast, It’s Time to Get Help Today
Being hit by a malicious attack can feel overwhelming as your business suddenly needs technical triage, is forced to decipher just what information has been compromised, and then has to remediate on a tight timeline to avoid any aftershocks or additional impact.
Getting the right IT support provider means having experts take over and stopping damages in their tracks. Instead of spinning your wheels, get your business on the road to recovery with a free onsite assessment today.
Read More
Too Small for IT Security? Data Says Think Again! Attacks on SMB Rise
Is Your Organization at Risk? If You Run Your Business Without Strategic IT Security, the Answer is…
For many small business owners IT security planning can seem like a luxury, but a lack of proactive security can actively hamper growth, even among the smallest of businesses.At its worst, not having the right defenses in place can sink your business operations as your entire enterprise is brought to a standstill by a malicious attack.

Many small- and medium-business owners know that IT security is something they should care about, but they have no idea how to manage it. One study by the National Cyber Security Alliance found that a whopping 59 percent of small business owners have no plan in place to prevent data breaches.
Even industries that revolve around preparing for the worst can be affected. IT help desk services can often be the first the line of defense for insurance companies, financial services firms, and healthcare providers in San Francisco, Oakland, or elsewhere throughout the greater Bay Area.
In fact, insurance companies are one example where a lack of network support services might have an outsized impact. Insurance companies regularly deal with highly sensitive data, including names, Social Security numbers, birthdays and addresses. Having the right IT support is essential.
What’s at Stake
The cost of data breaches can be enormous for small business owners. Research from Atlanta-based payment technology firm First Data shows that as many as 90 percent of data breaches can be traced back to small businesses, and the average cost of a breach to small businesses can be as high as $50,000 or more.

Not only would the cost of a malicious cyber attack or data breach be devastating for most small businesses, but the these costs and don’t even begin to account for the cost associated with the loss of trust from your customers.
Working with the right IT support firm to address the security, continuity and disaster recovery needs of your business are all critical to successfully maintaining and protecting your organization.
What Companies Can Do
Experts say that, at the very least, small businesses can enact the following controls:
- Secure all your business data. Security experts at Kroll say businesses should only keep the data they need.
- Stay current with security patches and updates. This can be more difficult than it seems, especially for busy small businesses.
- Require the strongest possible passwords.
- Establish an Internet usage document and make employees sign it.
- Limit access to your network outside of private workspaces.
- Consider a professional IT security audit.
Looking Inward
No one wants to think about a worst-case scenario, but threats to business data aren’t likely to go away any time soon. Unfortunately, employees are often at unwittingly at the center of them. Data from TrendMicro found that nearly 60 percent of employees surveyed “very frequently or frequently stored sensitive data on their laptops, smartphones, tablets, and other mobile devices.”
This may mean that more sophisticated IT support is needed to prevent a worst-case scenario in the era of Bring Your Own Device (BYOD). Rather than relying on stop-gap measures, an ounce of prevention may secure your business now and in the future.
If you are looking to get started in addressing your IT security concerns or looking to implement a strategic business technology plan for your organization, look no further and contact Bay Computing to get your complimentary onsite assessment started today.
Read More
