Latest News and Resources
Business IT Security And Why You’re Floundering Without It
Business IT Security and Why You’re Floundering Without It
Intitially, the term “IT security” may seem out of reach for many small business owners, or possibly even like a luxury, but as ransomware, BYOD-policies and compliance requirements become incraesingly common in the workplace, a lack of security can actively hamper growth, even and particularly with. At worst, it can sink the entire enterprise.
Many small- and medium-business owners know that IT security is something they should care about, but they have no idea how to manage it. One study by the National Cyber Security Alliance found that a whopping 59 percent of small business owners have no plan in place to prevent data breaches.
Even industries that revolve around preparing for the worst can be affected. IT help desk services can often be the first the line of defense for insurance companies, financial services firms, and healthcare providers in San Francisco, Oakland, or elsewhere throughout the greater Bay Area.
In fact, insurance companies are one example where a lack of network support services might have an outsized impact. Insurance companies regularly deal with highly sensitive data, including names, Social Security numbers, birthdays and addresses. Having the right IT support is essential.
What’s at Stake
The cost of data breaches can be enormous for small business owners. Research from Atlanta-based payment technology firm First Data shows that as many as 90 percent of data breaches can be traced back to small businesses, and the average cost of a breach to small businesses can be as high as $50,000 or more. That would be devastating for most small businesses and doesn’t even begin to account for the loss of trust from your customers. IT service continuity is critical.
What Companies Can Do
Experts say that, at the very least, small businesses can enact the following controls:
- Secure all your business data. Security experts at Kroll say businesses should only keep the data they need.
- Stay current with security patches and updates. This can be more difficult than it seems, especially for busy small businesses.
- Require the strongest possible passwords.
- Establish an Internet usage document and make employees sign it.
- Limit access to your network outside of private workspaces.
- Consider a professional IT security audit.
Looking Inward
No one wants to think about a worst-case scenario, but threats to business data aren’t likely to go away any time soon. Unfortunately, employees are often at unwittingly at the center of them. Data from TrendMicro found that nearly 60 percent of employees surveyed “very frequently or frequently stored sensitive data on their laptops, smartphones, tablets, and other mobile devices.” This may mean that more sophisticated IT support is needed to prevent a worst-case scenario in the era of Bring Your Own Device (BYOD). Rather than relying on stop-gap measures, having your IT services provider regularly work on prevention may secure your business now and in the future.
Read More
OCIE’s Focus on 2015 Cybersecurity Examination Initiatives
Understanding OCIE’s 2015 Cybersecurity Examination Initiative
Following
In its summary report of those
The OCIE further announced that it planned to focus on cybersecurity compliance
OCIE 2015 Cybersecurity Examination
OCIE examiners will pursue investigations into any
1. Governance
The OCIE may examine whether companies have existing
The
- Information security when dealing with third parties
- Software
patching, especially regarding critical security updates - Board minutes
and briefing documents containing or related to sensitive information and cybersecurity - A firm’s chief information security officer (CISO) or equivalent
position - The firm’s organizational structure as related to cybersecurity
- The
firm’s procedures for risk assessment, proactive threat identification, penetration tests, and vulnerability scans
2. Access Rights and Controls
The
The OCIE notes its intention to highlight concerns related to the following:
- Controls and safeguards for network segmentation and access levels across
different security clearances - Perimeter-facing procedures such as failed
logins, password retrieval, dormant accounts, and unauthorized logins - Network
access from outside devices - The firm’s documentation and dissemination
of its cybersecurity procedures to all relevant users
3. Data Loss and Prevention
OCIE
Examiners may highlight
- Identifying and preventing unauthorized data transfers
- Verifying
the authenticity of requests to transfer funds - Mapping data to verify information
ownership and privileges - Data classification and security levels
4. Vendor
As third-party vendors are a prominent source
The OCIE
5.
Security procedures are only as effective
6. Incident Response
The OCIE will examine a firm’s policies and
Examiners may further highlight procedures related to the following:
- How
cybersecurity fits into a firm’s business continuity plan - A firm’s testing
and drilling procedures for cybersecurity incidents and all data disasters - System-generated
alerts to automatically notify key personnel of potential incidents - Actual
customer losses related to cybersecurity incidents
Recommended Actions
Ultimately, the OCIE’s examination priorities reveal that it considers
A
To achieve
1. Data Protection
A
2. Proactive Security
A
3. Cyber-Perimeter
A
4. Documentation
84% of Dropper File Malware Attacks Hit Healthcare – Here’s What to Do
File Dropper Malware Targets Healthcare
As organizations worldwide work to increase data protection, cyber criminals are continuing to launch increased attacks against businesses. One of the greatest risks facing modern organizations are “dropper files.” These common risks are a form of advanced malware that gain entry into business systems through vulnerabilities to gather protected information to sell.

There was a significant spike in dropper file attacks in March, which constituted 90 percent of these malware attacks to date. Healthcare organizations are four times as likely as other industries to be targeted by dropper attacks, which constitute 84 percent of cyber crimes in this niche. This is a major threat in the information security realm, but there are ways businesses can take action to protect themselves against costly data breaches.
A dropper, or Trojan dropper, is a form of file that injects viruses and worms into a computer system. In some cases, these files can execute without being saved to a computer’s disk, which aids in avoiding detection by on-staff IT professionals. Droppers can encompass many forms of information security attack, including ransomware, a term used to describe a common method in which information security attacks are executed.
Due to the incredible sophistication of successful dropper attacks, a comprehensive information security practice is the only effective means of preventing this type of cyber crime. Symantec recommends a variety of approaches, including maximum firewall security, a comprehensive password policy and regular review of user permissions. By reducing vulnerabilities, including unnecessary file sharing and extraneous services, businesses can limit the ways in which dropper files can enter their networks.
Information security is inherently complex. Humans, compromised computers and outdated patches can all present means for dropper attacks to gain entrance to a company’s network. Working with an expert information security consultancy to identify risks can allow businesses of all sizes to prioritize and act upon their greatest vulnerabilities. Experts can assist with creating a broadly focused framework for protection and training.
A sophisticated, varied approach to information security is the only effective means of protection in today’s complex cyber crime climate. By partnering with an experienced IT services provider, your Bay Area business can get started reducing the risk of human error enabling malicious attacks, cut back on network related risks, and develop a comprehensive, customized approach to using technology to protect, preserve and promote your office productivity.
Stegoloader Malware Targeting Healthcare Providers Throughout North America — Is your Practice Safe?
Stegoloader Malware Targeting Healthcare Providers Throughout North America—Is Your Practice Safe?
There have been number of reports about how stegoloader malware is being used to target healthcare providers across North America, which is cause for concern because the malware is sophisticated enough to go undetected. To avoid being targeted, partner up with experienced IT security experts who have the skills to detect this complex malware. Read on if you live in the San Francisco Bay area to find out how we can help your organization.
What Is Stegoloader Malware?
Stegoloader is advanced malware that utilizes digital steganography by hiding within a Portable Network Graphic (PNG) hosted on a valid website. Once this malware is accidentally accessed, it remains on the computer, lurking in the background, often evading detection. It is so sophisticated that when it detects security or analysis tools running on the infected system, it will suspend its main program code, allowing it to stay hidden. Furthermore, it has been designed to ‘look’ for reverse engineering tools and terminate them, making it difficult for providers to regain control of their computer systems even when a security threat has been identified.
North American Healthcare Providers Targeted
A report carried out by Trend Micro found that North American healthcare providers were major targets, as many of their machines were infected with stegoloader Trojan malware. It appears that cyber criminals are interested in stealing healthcare information because it can be worth much more on the black market than credit card details. This puts healthcare providers in a vulnerable position as their system security may have been breached without them even being aware of it.
Keeping Your Organization Safe
Stegoloader malware is impacting healthcare providers across North America. Many of these organizations would have been initially complacent because they thought they had adequate security measures in place. If you are concerned that your healthcare practice may have already been targeted, or want to prevent your system security from being infiltrated, we can help! Bay Computing has a wealth of experience and technological solutions that can prevent your organization from having its security compromised.
When It Comes to Patch Management, Zero Day Can Be the Longest Day
Zero-Day, the Longest Day?
Ever since childhood, you learn that things go “Boom!” when you count down to zero…
Sometimes that’s a good thing: The engines ignite and a rocket lifts off
Sometimes that’s a bad thing: A bomb detonates
The question for software development and IT support teams is what does zero-day mean in terms of impact on end-users and what, if anything, they can and should do about it.
Zero-Day Defined
Despite software vendors’ best (or sometimes not) efforts, all software has bugs in it. Some of these bugs present opportunities that malicious users can take advantage of to gain access to a network, functionality, or data that they aren’t authorized to use.
Zero-day vulnerabilities are the bugs the vendor doesn’t know about. When hackers exploit them, this is called a zero-day exploit. Once vendors learn of a vulnerability, they work to create a patch to close it. Microsoft regularly issues patches on one or two Tuesdays per month, with occasional patches issued at other times.
Patches Close Zero-Day Vulnerabilities
Once a patch is issued, you can close the vulnerability by installing the patch. Yet it must be noted- If you don’t install it, your vulnerability to the zero-day exploit continues indefinitely. This is one reason it’s important to remain on supported versions of operating systems and application software, as well as pay for maintenance support. When you’re on an unsupported version, patches are no longer created — even if a security hole is later identified. Because code is commonly shared between versions, a hole found in the latest, supported version of the OS might exist in your older, unsupported version. But the vendor will only issue a patch for the supported version, meaning the zero-day vulnerability can’t be closed on an older system.
Because of the risk of these exploits, many companies require their computers to be maintained at current patch levels. In some ways, this is the “safe” decision. It’s important to realize, though, that there are risks associated with patching systems as well.
Patches Have Risks
The biggest risk is that installing a patch will somehow break an application. Patches are software, and as likely to contain bugs as any other software. There’s also the cost of downtime involved with deploying a patch, plus the potential of a failed deployment leaving a computer unusable until it can be restored. If the patch isn’t simply “under the hood” but makes a change that end-users can see, they may need some time to become familiar with the new way things work.
Create a Patch Management Strategy
Rather than automatically deploying all patches to every computer, companies should evaluate the risks involved. If a PC isn’t connected to the network, there may be very little risk of leaving it unpatched. When patches do need to be deployed, companies should think through how they can complete the deployment while minimizing the risk to their operations. Deploying to a few machines at a time and keeping some machines unpatched as a fallback are two options to consider.
The best way to develop a patch management strategy is to speak with an IT services provider like Bay Computing. We can help you evaluate the threat of vulnerabilities and plan a safe approach to deploying patches. Contact us, your San Francisco IT Services Provider to hit “stop” on the countdown to zero.
Read More‘Backoff’ Malware Steals Directly From POS Systems
‘Backoff’ Malware Steals Directly From POS Systems
Whenever new of the latest data breach hits the airwaves, chances are, it’s already too late. Why? As stories gain coverage, consumer awareness rises and preventative measures start being implemented, which is exactly why cybercriminals are constantly upping the ante to stay ahead of the curve.
With that in mind, every day new malware threats emerge, developed with the intent of infiltrating and infecting computers to enable hackers to steal valuable private information from businesses. The “treasure” malicious hackers are after can vary, yet personal data and payment card information such as credit card numbers are top targets.

Point-of-Sale (POS) outlets (which have become standard in small business environments for payment card processing) connect to online systems and present an extremely enticing target for cybercriminals using malware for their exploits. One of the most effective exploits in recent years has proven to be the Backoff group of malware programs, which specialize in spreading to POS software running on Windows systems.
Backoff Forwards Customer Data to Criminal Hackers
Backoff attacks begin when hackers penetrate the defense systems of the computers involved in business processes. Vulnerabilities such as unprotected internet connections, weak passwords and outdated firewalls let hackers into your IT systems with greater ease.
At this point, the attacker downloads files into your computers that are encoded to avoid detection, while simultaneously uploading private data back to his computer. Backoff malware is particularly effective because of its ability to accept patches that help the program evolve to remain hidden while discovering new sources of potentially valuable information.
Since Backoff attaches to POS systems, this malware is adept at recording credit card numbers, names, addresses, account information and any other personal or financial information that criminals can use to steal funds or commit identity theft.
Prevention Avoids Punishment
Companies such as Supervalu and Dairy Queen have experienced data theft by hackers using Backoff, leading to the compromise of millions of credit cards and countless reams of private customer data. In fact, more than 1,000 retailers may already suffer from data theft due to this group of malware. Even worse, many of these companies still might not know that they’ve been compromised.
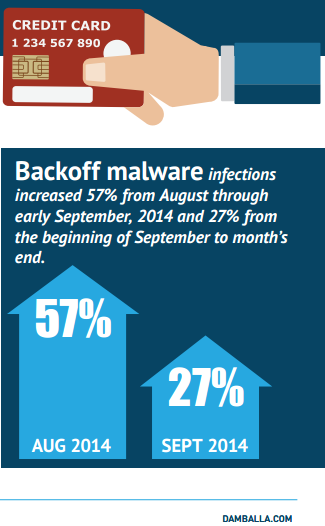
Considering a recent court ruling that allows the FTC to pursue damages due to negligent online security, companies need to make sure that all potential vulnerabilities become sealed off from online attacks. Taking care of the basics is no longer just an important part of building trust with customers; it’s also a legal requirement that must be upheld to avoid prosecution.
Implementing the best-fit protections against malicious infiltration means that your business needs to cover multiple vectors of attack. Wireless routers, hard drives and cloud storage should be encrypted. Firewalls and anti-virus programs should repel intrusions. IT systems shoul be consistently monitored and configured to immediately report unauthorized users.
Having a complete suite of online security diminshes the power of malware intrusions to help make sure attacks like Backoff doesn’t have a chance. A cost-effective solution that provides maximum protection involves partnering with a trusted managed service provider (MSP). With the help of full service IT support team, you can even the playing field, to give your small to medium-sized business (SMBs) the same lockdown security enjoyed by large enterprises.
Know you need to get started but feeling a bit overwhelmed by PCI-DSS Compliance or cybersecurity in general? Get started with a free onsite network assessment today to identify your existing vulnerabilities before the bad guys do!
Read MoreIT Services Security Alert: Cryptowall Ransomware
IT Services Security Alert: CryptoWall Ransomware
CryptoWall: Holding Your Data for Ransom
On June 23, 2015, the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) issued a warning about CryptoWall, a ransomware threat that can endanger your business and cost you money. Ransomware is malicious software that infects your computer and encrypts your data, locking you out of your files. Your information is held for “ransom,” a request for money usually between $200 and $10,000. Failure to pay by a certain deadline results in your data being destroyed.
The FBI has received more than 992 complaints of CryptoWall incidents since April 2014. They estimate the cost of these incidents totals more than $18 million. This cost not only includes the ransom itself, but recovery expenses and potential legal fees.

Becoming Infected
CryptoWare gets into your computer when you open infected ads, emails or attachments, or by visiting infected websites. Once the virus enters your computer, it quickly encrypts your data, preventing access.
Once your system is infected, an electronic ransom note alerts you to the amount you need to pay to recover access to your computer. Payment is usually demanded in Bitcoins, a form of digital currency that is anonymous, quick and untraceable.
Protect Yourself
Here are some key steps you can take to protect yourself against CryptoWare and other malicious software attacks:
- Use firewall protection
- Use advanced anti virus protection
- Enable pop up blockers
- Back up your computer routinely
- Do not open emails or messages from unrecognizable sources
- If you do receive a ransomware pop up or alert on your computer, the FBI recommends that you “immediately disconnect from the Internet to avoid any additional infections or data losses. Alert your local law enforcement personnel and file a complaint at www.IC3.gov.”
Get Help With Bay Area IT Services
Your focus should be on your business. Distractions and detriments such as CryptoWall can be overwhelming and costly. That is why many businesses choose to bring in professional partners, such as Bay Computing, to handle these problems. Your Bay Area IT service technician can ensure that your firewall and anti virus protection are up to date and active, and that your data is appropriately backed up. They can help train staff to prevent virus infections and, in the case of an infection, help you regain your data.
Contact our Bay Area IT services firm for your a free assessment or more information regarding your data’s safety.
Read More
Understanding the SEC OCIE’s Cybersecurity Examination Initiative
OCIE Focusing In On Cybersecurity Exam Initiatives:
The SEC’s top 6 priorities, and how working with an IT services provider ensures your firm is fully prepared
With the Securites and Exchange Comission’s Office of Compliance release of cybersecurity summary reports and exam intiatives, many financial services firms are being forced to reprioritize cybersecurity in preparation for potential SEC exams.
Without the right technology services partner in place, the initiatives are daunting, and getting started can feel overwhelming. Just look at the numbers.
In its summary report of those examinations, released in February of 2015, the OCIE stated that of those organizations it examined, 88 percent of the broker-dealers and 74 percent of the RIAs had experienced a cybersecurity incident recently.
This year, OCIE followed up with the Examination Priorities for 2016, where it was confirmed that in 2016 emphasis will be placed on testing how firms have implemented the procedures and controls initially examined in 2015.
The OCIE further announced that it planned to focus on cybersecurity compliance in its 2015 Examination Priorities. Last September, the office released the 2015 Risk Alert providing compliance guidance for industry entities that might be subject to examination.
Following a string of high-profile cybersecurity incidents in recent years, the Securities and Exchange Commission’s (SEC) Office of Compliance Inspections and Examinations (OCIE) kicked off the latest push when it released a Risk Alert in April of 2014 for relevant industries. Additionally, OCIE announced its intention to conduct examinations throughout the year to assess cybersecurity procedures and preparation in the securities industry.
In its summary report of those examinations, released in February of 2015, the OCIE stated that of those organizations it examined, 88 percent of the broker-dealers and 74 percent of the RIAs had experienced a cybersecurity incident recently.
The OCIE further announced that it planned to focus on cybersecurity compliance in its 2015 Examination Priorities. In September, the office released the 2015 Risk Alert providing compliance guidance for industry entities that might be subject to examination.
OCIE 2015 Cybersecurity Examination Initiative Priorities
OCIE examiners will pursue investigations into any area they deem necessary, but the 2015 Risk Alert highlights examination priorities in the following six primary areas:
1. Governance and Risk Assessment
The OCIE may examine whether companies have existing processes and procedures for cybersecurity and risk assessment. Examiners may also seek to determine whether your firm regularly reviews those procedures for efficacy and suitability to its own industry, along with how effectively high-level leadership is informed of, and participates in, those efforts.
The OCIE further highlights its intention to scrutinize compliance in areas regarding the following:
- Information security when dealing with third parties
- Software patching, especially regarding critical security updates
- Board minutes and briefing documents containing or related to sensitive information and cybersecurity
- Your firm’s chief information security officer (CISO) or equivalent position
- The firm’s organizational structure as related to cybersecurity
- The firm’s procedures for risk assessment, proactive threat identification, penetration tests, and vulnerability scans
2. Access Rights and Controls
The examiners will emphasize cybersecurity risks stemming from access to systems and information, especially related to basic safeguards like multifactor authentication and prompt access adjustments following personnel changes.
The OCIE notes its intention to highlight concerns related to the following:
- Controls and safeguards for network segmentation and access levels across different security clearances
- Perimeter-facing procedures such as failed logins, password retrieval, dormant accounts, and unauthorized logins
- Network access from outside devices
- The firm’s documentation and dissemination of its cybersecurity procedures to all relevant users
3. Data Loss and Prevention
OCIE examiners will assess your firm ‘s procedures for data transferred outside of the network through emails or other data uploads.
Examiners may highlight procedures for the following:
- Identifying and preventing unauthorized data transfers
- Verifying the authenticity of requests to transfer funds
- Mapping data to verify information ownership and privileges
- Data classification and security levels
4. Vendor Management
As third-party vendors are a prominent source of cybersecurity incidents, examiners may focus on vendor management, including how vendors are chosen, vetted and monitored. Examiners may also ascertain whether your firm considers vendor security to be an integral component of its overall cybersecurity procedures.
The OCIE additionally highlights the importance of clear vendor contracts regarding security responsibilities, along with documentation for all related areas, and your firm ‘s contingency plans for dealing with vendor-related breaches.
5. Training
Security procedures are only as effective as the training received by relevant personnel, including third-party partners. Therefore, examiners may verify that such training is thorough, widespread, and well documented.
6. Incident Response
The OCIE will examine your firm ‘s policies and procedures for responding to incidents, including documentation of the same, along with how policies are adjusted (when appropriate) following those incidents.
Examiners may further highlight procedures related to the following:
- How cybersecurity fits into your firm ‘s business continuity plan
- Your firm ‘s testing and drilling procedures for cybersecurity incidents and all data disasters
- System-generated alerts to automatically notify key personnel of potential incidents
- Actual customer losses related to cybersecurity incidents
Recommended Actions
Ultimately, the OCIE’s examination priorities reveal that it considers the cybersecurity status quo to be ill-suited to modern realities.
With PCIE’s release of the 2016 Examination Priorities for 2016, it was reiterated that the priority placed on cybersecurity compliance and controls will be further emphasized throughout the year.
This will most likely be seen through testing and the assessment of of how firms have implemented and integrated technical procedures and controls into their office technology environments.
Simply put, instead of a reactive, incident-based response, the OCIE wants firms to demonstrate that they have adopted a proactive, holistic stance regarding cybersecurity and workplace technology management.
Your firm ‘s default mindset should be that it is under threat from cyber-intrusions, and it should be able to demonstrate through robust documentation and actual practice that it is actively on alert for cybersecurity incidents.
To achieve this goal, your firm needs to ensure that it is working with an IT services provider that can serve as a full partner in security initiatives and procedures. Financial technology support partners can work with firms to establish, demonstrate and document its procedures in these four key areas:
1. Data Protection
Your firm must be able to rank all data according to a risk hierarchy (low, medium, high) and operational priority. Cybersecurity procedures should be strengthened accordingly, with the highest risk and highest operational priority data being subject to robust, multi-layered safeguards.
2. Proactive Security
Furthermore, your firm should implement, document and demonstrate a clear commitment to vigilant, proactive monitoring of security risks. Relevant procedures should be a top priority for all related personnel, and the firm should have a clearly understood process for how cybersecurity incidents will be identified, addressed and mitigated at all levels of the organization.
3. Cyber-Perimeter
Additionally, firms are expected to be able to demonstrate a clear understanding that its cyber-perimeter extends into the world of third parties, including vendors, partners and customers. Its procedures and practices for that outlying perimeter should be just as robust (if not more so) as its procedures for in-house data sites.
4. Documentation
Read More
5 Ways Managed IT Services for Insurance Companies Help Reduce Your Operation Expenses
Top 5 Ways for Insurance Firms to Reduce Operational Costs by Using Managed IT Services
1. Increased Employee Productivity
Experts estimate that up to 80 percent of unplanned technology outages are caused by poor administrative IT planning. These hours of downtime cost the least effective companies millions each year. Downtime caused by outdated equipment, network issues, and employee confusion can be significantly minimized with the right technology and appropriate employee training.
2. Predictable Recurring Costs
Unplanned technology costs can be challenging for insurance agencies. The experience of having to hire a contractor for an emergency fix can be incredibly expensive. By choosing to hire managed IT support, insurance agency owners can include a predictable monthly cost in their annual budgets. This is much easier for you to plan for than unexpected, high-dollar invoices for outages.
3. Proactive Maintenance
Managed IT services offer the benefit of expert support for maintenance. Proactive maintenance is critical to preventing unplanned outages and technology issues. In many cases, regular proactive maintenance is sufficient to prevent downtime and system issues, and the accompanying loss of productivity.
4. Expert Upgrade Advice
Did you know that the most common software selection tactics used by SMBs are actually highly ineffective? The process of choosing technologies is much simpler with expert guidance. Managed IT services for insurance understand your business and your industry. Experts who work with your company are able to offer far more personalized guidance than typical self-guided research processes.
5. Increased Information Security
The average cost of a cyber crime attack is 11.56 million dollars. Businesses who suffer a data breach are held fiscally responsible for notifying clients, which can devastate SMB brands. Managed IT services can provide in-depth assistance and expert guidance to help keep your information secure, including network protection and crucial employee training. Information security is a critical part of doing effective, ethical business in the technology age.
Visual Based Post [Blogging Blueprint]
INTRODUCTION:
An image post uses a visual element as the centerpiece of your post, such as a SlideShare presentation, infographic, comic, or high-resolution images.
Use your introduction to provide a caption for your image(s). Why is it valuable? What’s the point? Image posts don’t require a lot of text, so choose your words wisely.
Here are some examples of how we use Visual blog posts here at HubSpot:
BODY:
After just a few lines of introductory text, insert the visual.

Call out the most important elements of the visual. Include “Tweet this!” links that mention key points and vital takeaways from your visual.
CONCLUSION:
Now it’s time to say goodbye and wrap up your post. Remind your readers of your key takeaway, reiterate what your readers need to do to get the desired result, and ask a question about how they see the topic to encourage comments and conversation. Don’t forget to add a Call-to-Action!
Congratulations! What a lovely image post you’ve created.
Read More
