Latest News and Resources
HIPAA Healthcare IT: Protect Patient Privacy
Using IT Services to Conform to HIPAA Reqs and Protect Your Patients’ Privacy
On average, two million Americans face medical identity theft each year, costing U.S. healthcare organizations an estimated $41 billion [1]. Healthcare practices are finding it increasingly difficult to comply with patient privacy regulations. After the enactment of the HIPAA Privacy statute in 1996, there have been several regulations regarding patient privacy: HITECH, ARRA Meaningful Use, and the Omnibus Rule.

Patient privacy breaches attract severe penalties, both criminal and financial, along with harm to reputation. When the stakes are so high, a solid foundation is necessary — involving policy, procedures and technology — for ensuring patient privacy throughout the healthcare organization.
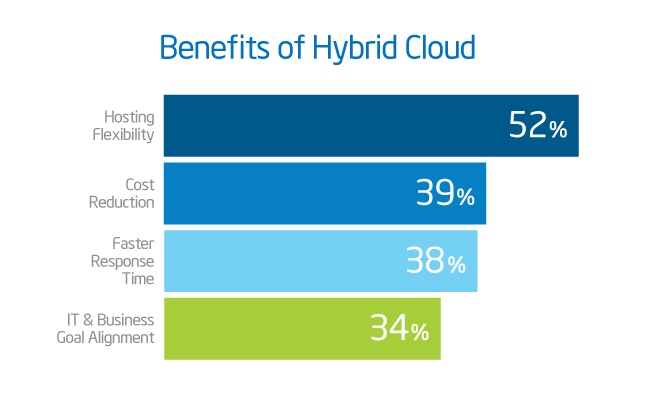
Top Challenges in Securing Patient Privacy Data
Although healthcare is the most regulated industry in the US today, in order to comply with the strict regulations and for avoiding stiff penalties, healthcare organizations face three primary challenges in protecting patient data. Every access to patient data must be logged — this is a HIPAA requirement. Massive volumes of access records are generated and need to be audited. Lastly, diverse data needs to be consolidated.
A Three-Step Methodology Can Lead To a Solid Foundation
As patient privacy compliance program [2], such as the Healthcare IT Support Services from Bay Computing in the San Francisco Bay Area, can provide a solid foundation and reduce the risk of a data breach with the following three elements:
1. Defining Appropriate Policies
When healthcare practices accept principles regarding patient privacy, those are reflected in their policies. These help establish a culture and expectation binding all stakeholders, including the doctors, office managers, and decision-makers of small to mid-sized practices.
2. Setting up Suitable Procedures
To enforce the policy, healthcare practices need suitable processes for developing, documenting, implementing, and communicating procedures. Mostly this involves defining who can access what data [3].
3. Using Current Technology
Tasks that cannot be addressed manually need to be handled with technology and this must be augmented in the procedures by IT support. As appropriate technology allows automatic monitoring of patient privacy data access, healthcare practices can be free of the limitations of random and manual audits.
Conclusion
Located in the San Francisco Bay Area, Bay Computing helps healthcare providers succeed by providing comprehensive, accessible and readily available healthcare IT support.
With IT services that focus on providing your users a great helpdesk and technical support experience, your patient care providers can now take advantage of your existing IT investments to satisfy increasing demands while observing Meaningful Use, navigating any new implementations following HIPAA Compliance Assessments, and any other number of industry requirements.
Ready to get started? Contact Bay Computing today and receive a free onsite network assessment!
References:
[1]
https://www.experianplc.com/media/news/2012/more-people-aware-of-medical-identity-theft/
[3]
http://fas.org:8080/sgp/crs/misc/R40599.pdf
The Benefits of a Hybrid Cloud Environment
The Benefits of a Hybrid Cloud Environment
If your business has all its mission-critical hardware located on-site—with applications installed directly on local workstations or through on-premise servers—it may be time for a change. This setup is becoming increasingly rare these days for many reasons including; heavy upfront costs, redundancy concerns, physical security issues and the overall cost of maintenance.
What is the Hybrid Cloud?
Why You Should Consider the Hybrid Cloud
Unlike a complete cloud-based infrastructure, hybrid clouds allow access to on-premise hardware. You can deploy virtualization solutions to emulate cloud-based resource sharing or use your on-premise hardware normally.
Switching from a completely on-premise infrastructure to a hybrid cloud infrastructure can be as simple as incorporating cloud-based applications into your regular workflows. For example, cloud-based email and video chat services can serve as a natural starting point.
The scaling benefits of hybrid cloud computing are particularly useful if you publish a lot of media, especially videos that have viral traffic-potential. It’s not feasible to keep enough servers on-premise to handle peak demand when your typical usage is minimal. A cloud-based content platform can seamlessly scale your capacity to handle the additional load without incurring the heavy equipment costs of traditional infrastructure upgrades and setups.
How to Deploy a Hybrid Cloud
It’s important to consider how your on-premise hardware and cloud-based services are going to integrate. Setup and maintenance can get complicated when you add development platforms, hosting, data storage and other services. Even Forbes ended up asking, “What’s Right For Your Business?” in a recent article examining private, public or hybrid cloud computing.
Maybe your IT department is overloaded and is in desperate need of extra help, or maybe your offices doesn’t have a dedicated IT staff- No matter what your office environment looks like, working with a SF Bay Area IT services firm gives you the expertise required to roll out—and maintain—a hybrid cloud that will improve your business infrastructure and help expedite your daily operations.
Put your on-premise hardware to the best use possible while taking advantage of cloud-based perks with a hybrid cloud system. Add in an IT support team with hybrid cloud experts and you have an excellent foundation for kick-starting your business growth. Get in touch with Bay Computing’s implementation specialists and get your free onsite network assessment sscheduled today!
Read MoreTop 10 New Features of Windows 10 for Your Business Users
Top 10 New Features of Windows 10
Released in July 2015, Windows 10 has many new features as compared to Windows 8. From the reintroduction of the Start menu to windowed Metro apps, here are the 10 top new features to watch out for in Windows 10.
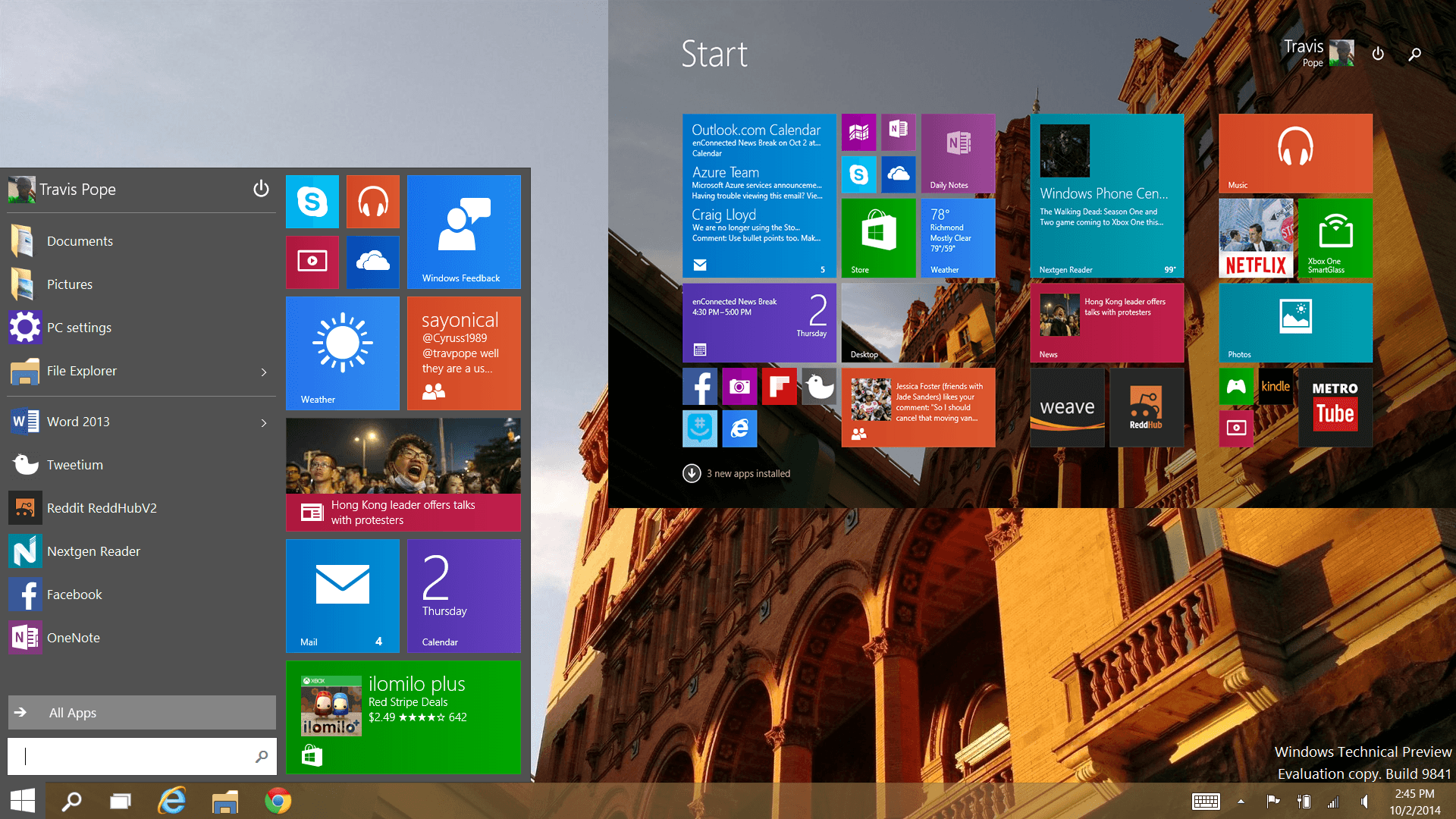
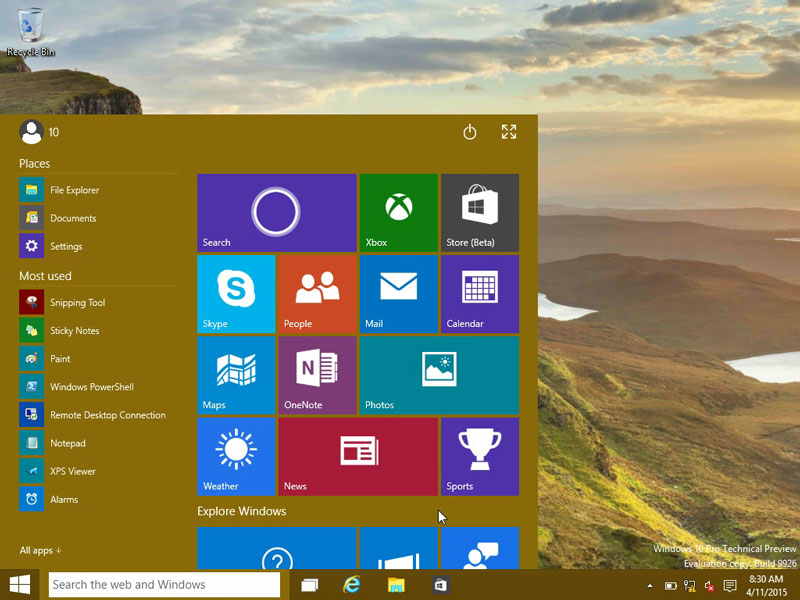
1. Start Menu
The Start menu is back in Windows 10!
Simply click on the Windows icon in the lower left corner of the desktop to view installed programs and search for files.
By default, the Windows 10 Start menu features Live Tiles, similar to the Start screen in Windows 10, but there is an option to turn them off.
2. Windowed Metro Apps
Metro apps have been updated to better meet the needs of desktop users in Windows 10.
Whereas Windows 8 forced desktop users to open Metro apps in full-screen mode, Windows 10 opens them in windows that can be resized.
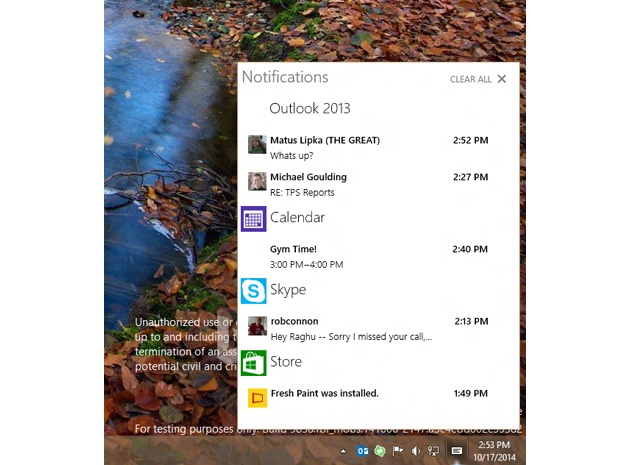
3. Action Center Notifications
Windows 10 features a centralized Action Center, which uses popup notifications to help you keep track of your important office reminders, lateste messages and time-sensitive deadlines.
Instead of having key information fall through the cracks on a busy day, the Windows action center is a great tool to help out your business organization. You can also use the Action Center to quickly toggle Bluetooth or Wi-Fi on and off, just as you would on an iPhone or Android phone.
4. Cortana
Windows 10 brings Cortana, the digital assistant from Windows Phones, to desktop users. Cortana is able to quickly find information online or on the computer’s hard drive. As with the virtual assistant on the Windows Phone, you can talk to Cortana using natural language, such as “Find me the photos I took in January.”
5. Project Spartan Browser
Microsoft has finally provided an alternative to Internet Explorer. Windows 10 features Project Spartan, a browser that is built for speed and compatibility with the modern Web.
6. New Mail App
Windows 10 features a new and improved Mail app, which is much faster and more responsive in comparison to the Windows 8 version. If you’re using the Mail app on a touchscreen laptop or tablet, then you can use customizable swipe gestures to move through your emails.
7. Virtual Desktops
Organize your apps into virtual desktops, which you can easily move between using Alt+Tab. It’s an easy way of organizing all your apps and windows into an arrangement that works for you.
8. Improved Windows Explorer
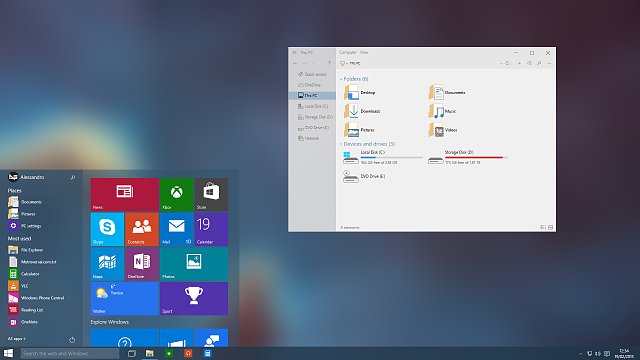
Windows Explorer has been upgraded for Windows 10.
There is now an easily accessible list of the folders you regularly visit on the left of the panel, along with a list of your recently opened files readily avaialble.
9. Continuum
Using Windows 10 on a touchscreen laptop? Thanks to the Continuum feature, you can easily switch between desktop mode and a swipe mode that’s suitable for touchscreen use.
10. Single Settings Menu
You can now manage all your Settings in one place, rather than having to use the two separate Settings menus for Metro and Desktop interfaces on Windows 8. Access the Windows 10 Settings menu from the Start menu.
Read MoreThe New Office Monster…HIPAA
Your Office’s Latest Challenge…HIPAA Compliance

The Health Information Portability and Accountability Act, otherwise known as HIPAA, may be the new the headache of every cybersecurity professional who deals with HIPAA customers.
To understand the headaches often associated with HIPAA compliance, you must first understand what HIPAA is.
Personally Identifiable Information Regs
This federal law protects an individual’s personally identifiable information (PII) by setting administrative, security and technical standards and safeguards nation-wide. Those who collect, process or use the data must ensure it is reasonably protected, and the same rules apply to everyone in the health care industry.
Companies or organizations that deal in HIPAA data are known as Covered Entities and Business Associates, and they are required to have your written consent to use PII data. Among all the paperwork you sign when you go to a hospital is a HIPAA agreement.
How HIPAA Affects Security
Security measures such as restricting access to HIPAA-related data, locking individual workstations and requiring employees to wear ID badges are expected to be followed.
Being HIPAA compliant is more about standards and practices then it is about a specific cybersecurity tool.
HIPAA compliance includes methods of restricting physical and digital access to the data, proper log management, contingency planning, appropriate training and valid incident response plans.

Why HIPAA Compliance Can Be A Headache
Protecting PII seems like a reasonable request for any organization that consciously agrees to work in the healthcare space.
The headache for many businesses and providers comes from the fact that the standards and practices are meant for everyone in and associated with the organization, not just those directly handling HIPAA data.
The security standards for HIPAA compliance are strict, with infractions carrying hefty fines from the Department of Health and Human Services.For example, in a HIPAA-restricted workplace something as simple as forgetting your employee badge could potentially get the organization fined thousands of dollars.
Also, organizations claiming HIPAA compliance are subject to random auditing from the Department of Health and Human Services, so standards must be followed at all times.
For organizations striving to become HIPAA compliant, the challenges of implementing and maintaining proper patient confidentiality and information security stems from the classic battle between convenience versus security. Unfortunately, without the right guidance, office procedures and Healthcare IT services solutions, convenience often wins.
If you’re looking to get started tackling the technical challenges of bringing your organization into compliance, contact your local Bay Area healthcare technology team for your free network assessment today!
Read More
Windows 10: Helping Your Office Bridge the Gap Between PCs and Tablets
How to Use Windows 10 for Seamless Transitions Between Office Devices
When Microsoft released Windows 8, it went too far in focusing on the tablet experience, leaving desktop computer users out to dry. Now it’s time for Windows 10 to show that Microsoft has an operating system truly capable of bridging the gap between PCs and tablets.
Approximately 74 percent of companies promote some form of bring your own device (BYOD) policy, according to ZD Net, resulting in a mix of tablets and other mobile devices in the office. Now Windows 10 is going to allow users to easily switch between tablet and PC without major transitions each time.
Universal Apps
Apps from the Microsoft App store are no longer treated differently from other programs. They have a similar appearance, are controlled the same, and are also universal between tablets and PCs.
Instead of using two different programs in your office for mobile and desktop uses, you can now use the same app on both platforms. For example, Adobe Photoshop Express allows you to start work on a desktop and then open up the app on your tablet.
The Microsoft Office suite is another universal app that allows you to use the same program on both devices. This cuts down on training time and improves productivity.
Redesigned User Interface
One of the biggest problems the original Windows 8 user interface (UI) had is that it focused too much on the touchscreen dynamic. The shake-up caused many people to reach out to IT help desk services to figure out how to use the UI on a non-touchscreen desktop, and it caused significant frustration.
Microsoft has learned its lesson with Windows 10. The UI retains the familiar Start menu, with the Windows 8 metro style design incorporated as a small part of this menu. Microsoft also added a virtual desktop feature, allowing you to group and organize open programs into their own desktop. You get a good balance of familiar features and new ones that makes this operating system easier to use.
Seamless Tablet Mode
Some of the most popular tablets on the market can switch between tablet and laptop mode. Windows 10 accommodates for that by seamlessly switching to the tablet mode UI as soon as the keyboard is detached from the tablet.
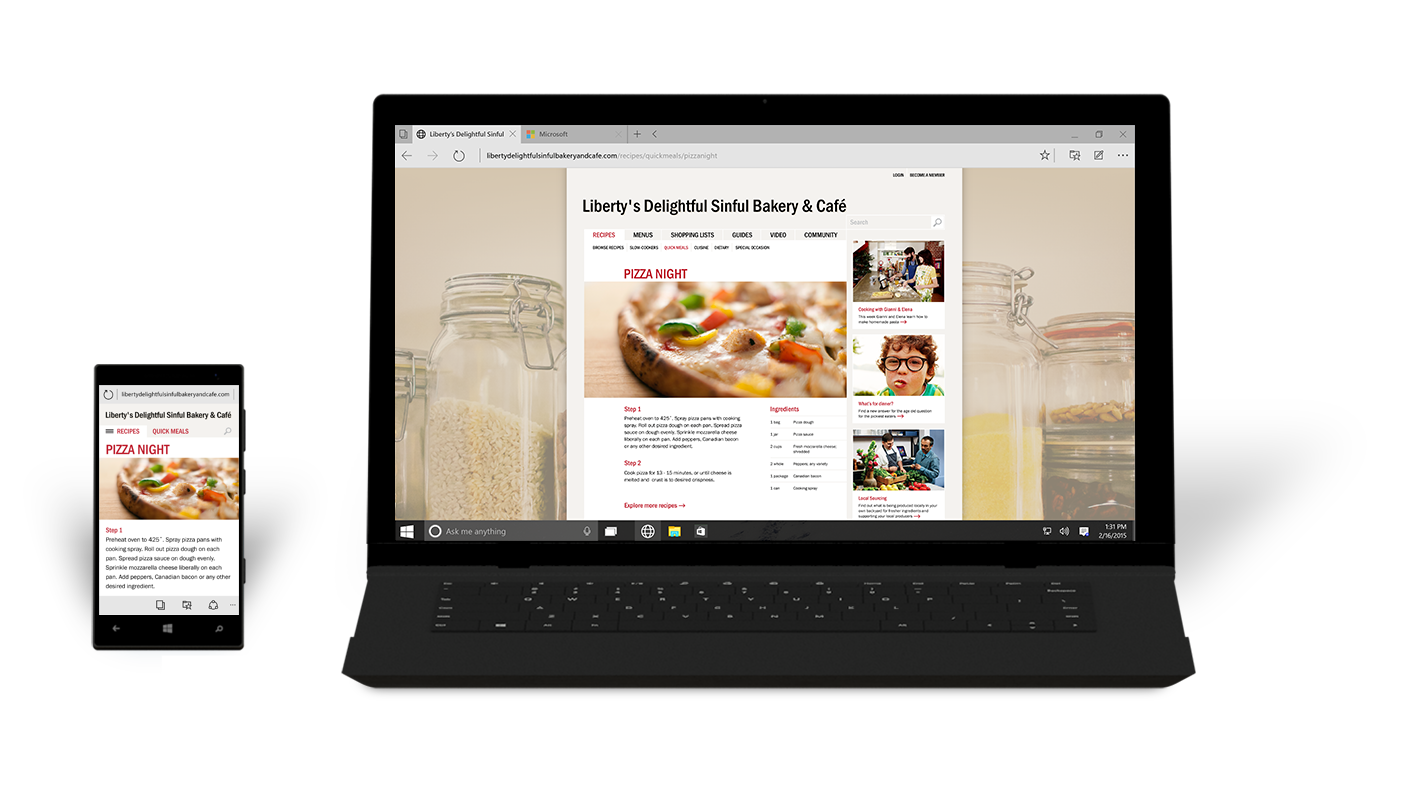
This mode optimizes the UI for touchscreen control, taking windows and apps full screen. Once you connect the keyboard back to the tablet, it switches to standard Windows 10 view.
Windows 10 learned many lessons from Windows 8, resulting in an operating system that allows users to easily transfer from PC to tablet and back again.
Read MoreAvoid Data Breaches: Key IT Security Strategies for Your Business
Effective Strategies Your Business Can Implement to Avoid a Data Breach
Digital security is a vital concern for all businesses. In an era of constant security breaches, in a climate where businesses are targeted regardless of size, and unprecedented sophistication of data thieves, the most vital information can – and, according to statistics, likely will be – compromised at some point. Once a severe data breach occurs, the damage can derail organizations with crippling costs and possibly even destroy once-bright future growth.
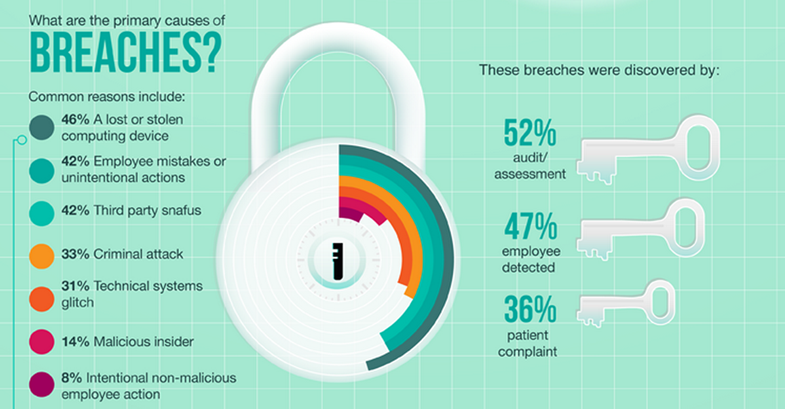
However, businesses can prevent data breaches. In fact, it is much easier to prevent a data breach than to recover from one, and the strategies at a small business’s disposal are simple and effective.
IT Support
The first line of defense against a data breach is professional tech support. While most methods can theoretically be implemented by a business in the absence of outside help, professional IT support greatly enhances security in every facet of data theft prevention.
Invest in a Strong Security Suite
The sheer number of security solutions available can be overwhelming. Sales tactics abound, and it can be difficult not only to choose a solution, but to know what you need in the first place. When you partner with seasoned IT professionals with years of experience working with local businesses, they are naturally well-versed in this area. A good tech support firm will recommend and provide the right solutions tailored to fit your business needs.
Restrict Access
An extremely important and oft-ignored consideration is access restriction. By restricting network, download, hardware, software, and database access to a user-specific degree, you automatically strengthen your security. However, setting user-specific permissions can be time consuming and confusing, and any errors will probably result in system down time. Professional IT support can easily set user-appropriate permissions specific to each role in the organization.
Appropriate Data Storage
Appropriate security, timely purging, and selective storage of data mitigate data theft. Thieves can’t take what you don’t have. IT support will monitor, encrypt, restore, and purge stored date in an appropriate and efficient manner.
Data Loss Plan
The best data loss plans help enable business continuity and make disaster recovery as painless as possible by providing a course of action for whatever emergency your business may end up facing. Just like a friend wouldn’t let you go into battle without the right equpiment, a reliable and proactive IT support team will work personally with your business and your key users to construct and implement a customized data loss plan, to ensure that threats can be neutralized upon discovery.
Education
Employee education is vital. From providing industry updates on the latest cybersecurity threats (such as Rombertik), and technical resources to helping educate end users whenever they help resolve technical issues, your IT support team can work with you to promote the best ongoing education strategies for your employees.
The best defense against a data breach is to:
- Keep your network and servers secure
- Implement security solutions and the right antivirus for your Bay Area business
- Backup your data
- Regularly monitor network activity
- And to have disaster recovery solutions in place a part of your contingency plan should the worst happen
While you can implement these strategies independently, professional IT Support will help your organization develop these defenses, and will bring their experience to implementing, regularly updating and maintaining those defenses for you. Should a data breach occur, your tech support team will move in immediately to stop the breach from doing any further harm to your business, repair the damage as possible, and reconstruct any lost funcationalities and improve your security, making IT support a key investment into your business success and protecting your future earnings.
Read MoreWhy Use IT Services as a Startup Business
3 Reasons to Use IT Services as a Startup Business
When you start a new business, you’re often running with a lean operation during the startup phase. You and your employees wear multiple hats to handle job duties, you’re working with a limited budget and you have a lot of upfront infrastructure to put in place. One area small businesses may skimp out on is IT support and staff. If you aren’t running a technology-centric startup, you might not place a high priority on your IT department. However, today’s modern businesses rely on a variety of technology to operate efficiently. Your startup business doesn’t need full-time IT staff it can’t afford at the beginning of its journey, though. IT services can offer major benefits to a business that’s just getting started.
2. Budget-Friendly IT Help Desk Services: You aren’t responsible for overhead costs or salaries with IT services. Instead, you can simplify your operations by only dealing with a transparent, upfront and predictable cost for an entire technical support team which lightens the load on your startup business budget.
3. Adjusting to Your Workload: Rapidly growing businesses often have a variety of one-time IT needs while getting business operations up and running or building for when your key resources are tied up working on core operations. No matter if you’re facing a large-scale deployment, building an entire infrastructure from scratch or looking to expand in the most cost-effective yet long-term sustainable way, your IT demands may suddenly be much higher during these peak demand time periods.
Your startup business will demand your full time, attention, and resources from the get go. Instead of getting overwhelmed with your IT needs, bring on IT services and get the expert advice you need to create a foundation that is built to last as your business grows.
How Do HIPAA Violations Happen Unintentionally
Are You Unwittingly Violating HIPAA Regulations?
In a busy medical office,
Exposing Confidential Information to Other Patients
Although everyone in your office understands it’s important not to discuss
Keeping patient information private requires scrupulous attention to the
Neglecting Your Computer Network
Patient records
Being Lax with Your
Thanks to your laptop, you’re no longer chained to the office
Texting Confidential Information
Texting is one of the fastest
By keeping these potential programs in mind and educating
Making the Decision to Move Your Business to the Cloud
How to Decide for Your Business: Making the Decision to Move to the Cloud
The technology world makes frequent mention of “the cloud”, which often makes it difficult to determine if this too is just another tech buzzword or if “the cloud” is actually a key tool to help enable your business operations to succeed.
At the most basic level, cloud-based technology consist of hardware and software resources that you access through off-site based resources, instead of through an on-premise installation.The cloud also pools its resources together for higher performance and greater redundancy, instead of assigning a single piece of hardware to your business.
What Makes the Cloud Worthwhile?
With 87 percent of small and medium sized businesses already using some form of cloud technology, according to PC World, it is evident that the cloud has a strong following with SMBs. You may even be using cloud services in your business without realizing it — Gmail, Dropbox and Evernote are all commonly used cloud applications.
The cloud provides your business with a wide range of tools, from software to complete infrastructures, opening up your access to high performance technology. Instead of running your internal communication program off an aging server in an unused closet, you get access to integrated solutions running off the latest high end hardware.
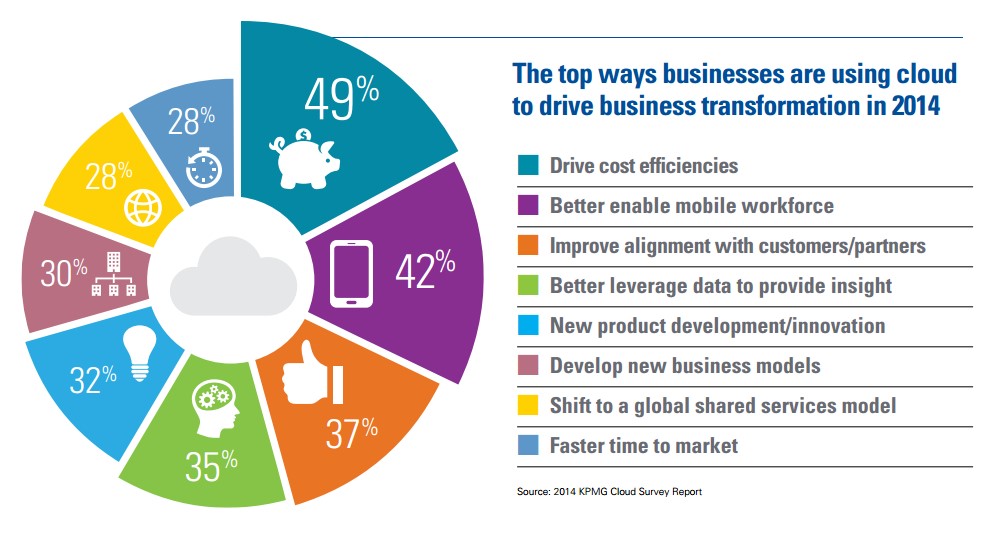
Security is a common concern for many businesses considering cloud adoption. Fortunately, the security available often exceeds what you may currently have at your own office. A study by Right Scale found that only 13 percent of companies who have adopted cloud technologies have significant security concerns, compared to 31 percent of companies who are new to cloud technology adoption.
Maintaining strong security is in each cloud vendor’s best interests, as their entire business models revolve around reliable access, data integrity and the security of sensitive information.
The flexibility offered by cloud services also make this technology budget friendly for SMBs. Many cloud vendors operate on a subscription model that may be a flat rate or a per user rate, so instead of paying for costly hardware, a large number of software licenses and the costs associated with deployment upfront, your business pays a recurring fee for access to the services provided.
Your organization can then easily scale your users or your capacity up and down as needed, because the service cost scales with your business as opposed to having to implement large projects after hitting particular usage thresholds.
Your IT security budget may be competing with a range of other expenses within your overall business budget, but with the right guidance from your IT support services team, identifying the best cloud computing solutions who place high priority on maintaining the appropriate security measures can pay off in significant savings as well as improved office IT performance.
What You Need to Support Cloud Deployment
Cloud technology isn’t reserved only for businesses with full in-house IT departments. In many cases, your small to midsize business may be examining options when it comes time for an infrastructure upgrade, and while reviewing what you currently have in place and the softwares deployed, you may start to question the value proposition associated with the higher upfront costs of having your business upgrade or replace outdated or failing onsite infrastructure.

When looking to move your office technologies forward, you want to find out the best ways possible to streamline and cut outunnecessary IT work from the outset. So what do you do once you’re all set up with your cloud services but you don’t have the IT resources to properly train and support users?
Instead of holding back on adopting technology that could vastly improve your business productivity simply because you don’t currently have the IT manpower available, bring on a IT support service provider to get your organization started leveraging cloud technology the right way from the very beginning and to keep everything running smoothly going into the future.
7 Reasons You Might Switch To Windows 10 This Year
7 Reasons to Switch to Windows 10 This Year
Windows 10 (Win10) is the next generation of Microsoft operating systems.
1. Free for a Limited Time
If you currently have computers with Windows 7 or Windows 8.1, then
2. The Start Menu
When
3. Re-Sizeable Apps
You can now re-size apps that were previously full screen-only as if they were
4. Virtual Desktops
Windows
5.
With this
6. Futuristic Biometrics
Windows Hello is a brand new,
7. Tons of Customization
Microsoft has gone from clunky and
