Latest News and Resources
Windows 10: Helping Your Office Bridge the Gap Between PCs and Tablets
How to Use Windows 10 for Seamless Transitions Between Office Devices
When Microsoft released Windows 8, it went too far in focusing on the tablet experience, leaving desktop computer users out to dry. Now it’s time for Windows 10 to show that Microsoft has an operating system truly capable of bridging the gap between PCs and tablets.
Approximately 74 percent of companies promote some form of bring your own device (BYOD) policy, according to ZD Net, resulting in a mix of tablets and other mobile devices in the office. Now Windows 10 is going to allow users to easily switch between tablet and PC without major transitions each time.
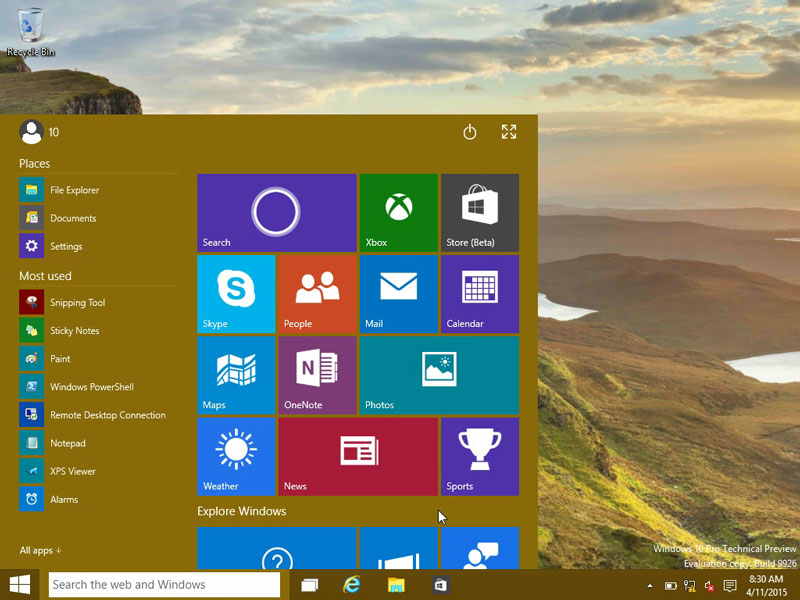
Universal Apps
Apps from the Microsoft App store are no longer treated differently from other programs. They have a similar appearance, are controlled the same, and are also universal between tablets and PCs.
Instead of using two different programs in your office for mobile and desktop uses, you can now use the same app on both platforms. For example, Adobe Photoshop Express allows you to start work on a desktop and then open up the app on your tablet.
The Microsoft Office suite is another universal app that allows you to use the same program on both devices. This cuts down on training time and improves productivity.
Redesigned User Interface
One of the biggest problems the original Windows 8 user interface (UI) had is that it focused too much on the touchscreen dynamic. The shake-up caused many people to reach out to IT help desk services to figure out how to use the UI on a non-touchscreen desktop, and it caused significant frustration.
Microsoft has learned its lesson with Windows 10. The UI retains the familiar Start menu, with the Windows 8 metro style design incorporated as a small part of this menu. Microsoft also added a virtual desktop feature, allowing you to group and organize open programs into their own desktop. You get a good balance of familiar features and new ones that makes this operating system easier to use.
Seamless Tablet Mode
Some of the most popular tablets on the market can switch between tablet and laptop mode. Windows 10 accommodates for that by seamlessly switching to the tablet mode UI as soon as the keyboard is detached from the tablet.
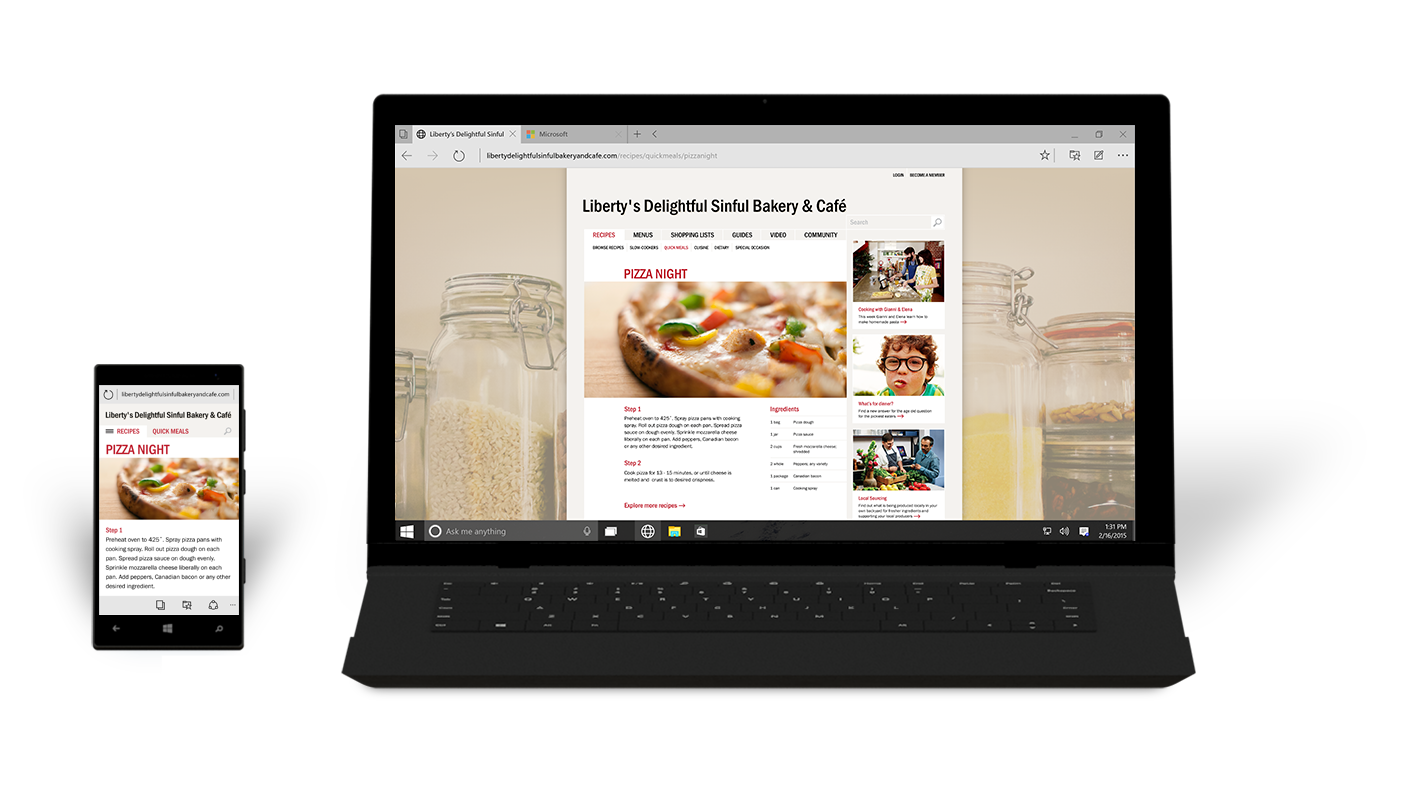
This mode optimizes the UI for touchscreen control, taking windows and apps full screen. Once you connect the keyboard back to the tablet, it switches to standard Windows 10 view.
Windows 10 learned many lessons from Windows 8, resulting in an operating system that allows users to easily transfer from PC to tablet and back again.
Read MoreAvoid Data Breaches: Key IT Security Strategies for Your Business
Effective Strategies Your Business Can Implement to Avoid a Data Breach
Digital security is a vital concern for all businesses. In an era of constant security breaches, in a climate where businesses are targeted regardless of size, and unprecedented sophistication of data thieves, the most vital information can – and, according to statistics, likely will be – compromised at some point. Once a severe data breach occurs, the damage can derail organizations with crippling costs and possibly even destroy once-bright future growth.
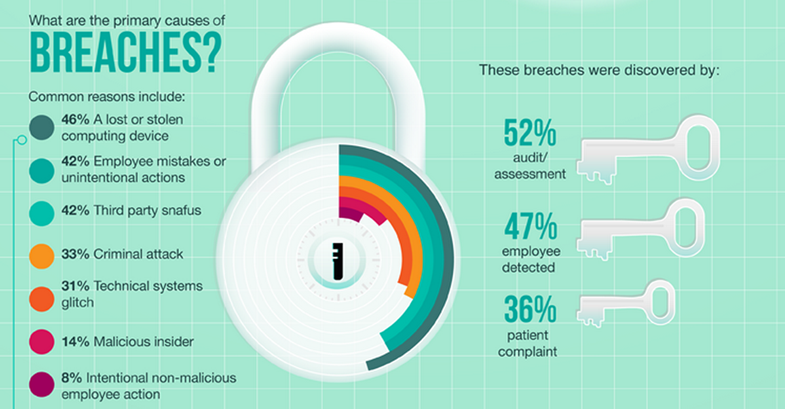
However, businesses can prevent data breaches. In fact, it is much easier to prevent a data breach than to recover from one, and the strategies at a small business’s disposal are simple and effective.
IT Support
The first line of defense against a data breach is professional tech support. While most methods can theoretically be implemented by a business in the absence of outside help, professional IT support greatly enhances security in every facet of data theft prevention.
Invest in a Strong Security Suite
The sheer number of security solutions available can be overwhelming. Sales tactics abound, and it can be difficult not only to choose a solution, but to know what you need in the first place. When you partner with seasoned IT professionals with years of experience working with local businesses, they are naturally well-versed in this area. A good tech support firm will recommend and provide the right solutions tailored to fit your business needs.
Restrict Access
An extremely important and oft-ignored consideration is access restriction. By restricting network, download, hardware, software, and database access to a user-specific degree, you automatically strengthen your security. However, setting user-specific permissions can be time consuming and confusing, and any errors will probably result in system down time. Professional IT support can easily set user-appropriate permissions specific to each role in the organization.
Appropriate Data Storage
Appropriate security, timely purging, and selective storage of data mitigate data theft. Thieves can’t take what you don’t have. IT support will monitor, encrypt, restore, and purge stored date in an appropriate and efficient manner.
Data Loss Plan
The best data loss plans help enable business continuity and make disaster recovery as painless as possible by providing a course of action for whatever emergency your business may end up facing. Just like a friend wouldn’t let you go into battle without the right equpiment, a reliable and proactive IT support team will work personally with your business and your key users to construct and implement a customized data loss plan, to ensure that threats can be neutralized upon discovery.
Education
Employee education is vital. From providing industry updates on the latest cybersecurity threats (such as Rombertik), and technical resources to helping educate end users whenever they help resolve technical issues, your IT support team can work with you to promote the best ongoing education strategies for your employees.
The best defense against a data breach is to:
- Keep your network and servers secure
- Implement security solutions and the right antivirus for your Bay Area business
- Backup your data
- Regularly monitor network activity
- And to have disaster recovery solutions in place a part of your contingency plan should the worst happen
While you can implement these strategies independently, professional IT Support will help your organization develop these defenses, and will bring their experience to implementing, regularly updating and maintaining those defenses for you. Should a data breach occur, your tech support team will move in immediately to stop the breach from doing any further harm to your business, repair the damage as possible, and reconstruct any lost funcationalities and improve your security, making IT support a key investment into your business success and protecting your future earnings.
Read More3 Reasons to Use IT Services as a Startup Business
3 Reasons to Use IT Services as a Startup Business
When you start a new business, you’re often running with a lean operation during the startup phase. You and your employees wear multiple hats to handle job duties, you’re working with a limited budget and you have a lot of upfront infrastructure to put in place. One area small businesses may skimp out on is IT support and staff. If you aren’t running a technology-centric startup, you might not place a high priority on your IT department. However, today’s modern businesses rely on a variety of technology to operate efficiently. Your startup business doesn’t need full-time IT staff it can’t afford at the beginning of its journey, though. IT services can offer major benefits to a business that’s just getting started.
2. Budget-Friendly IT Help Desk Services: You aren’t responsible for overhead costs or salaries with IT services. Instead, you can simplify your operations by only dealing with a transparent, upfront and predictable cost for an entire technical support team which lightens the load on your startup business budget.
3. Adjusting to Your Workload: Rapidly growing businesses often have a variety of one-time IT needs while getting business operations up and running or building for when your key resources are tied up working on core operations. No matter if you’re facing a large-scale deployment, building an entire infrastructure from scratch or looking to expand in the most cost-effective yet long-term sustainable way, your IT demands may suddenly be much higher during these peak demand time periods.
Your startup business will demand your full time, attention, and resources from the get go. Instead of getting overwhelmed with your IT needs, bring on IT services and get the expert advice you need to create a foundation that is built to last as your business grows.
Are You Unwittingly Violating HIPAA Regulations?
Are You Unwittingly Violating HIPAA Regulations?
In a busy medical office,
Exposing Confidential Information to Other Patients
Although everyone in your office understands it’s important not to discuss
Keeping patient information private requires scrupulous attention to the
Neglecting Your Computer Network
Patient records
Being Lax with Your
Thanks to your laptop, you’re no longer chained to the office
Texting Confidential Information
Texting is one of the fastest
By keeping these potential programs in mind and educating
Making the Decision to Move Your Business to the Cloud
How to Decide for Your Business: Making the Decision to Move to the Cloud
The technology world makes frequent mention of “the cloud”, which often makes it difficult to determine if this too is just another tech buzzword or if “the cloud” is actually a key tool to help enable your business operations to succeed.
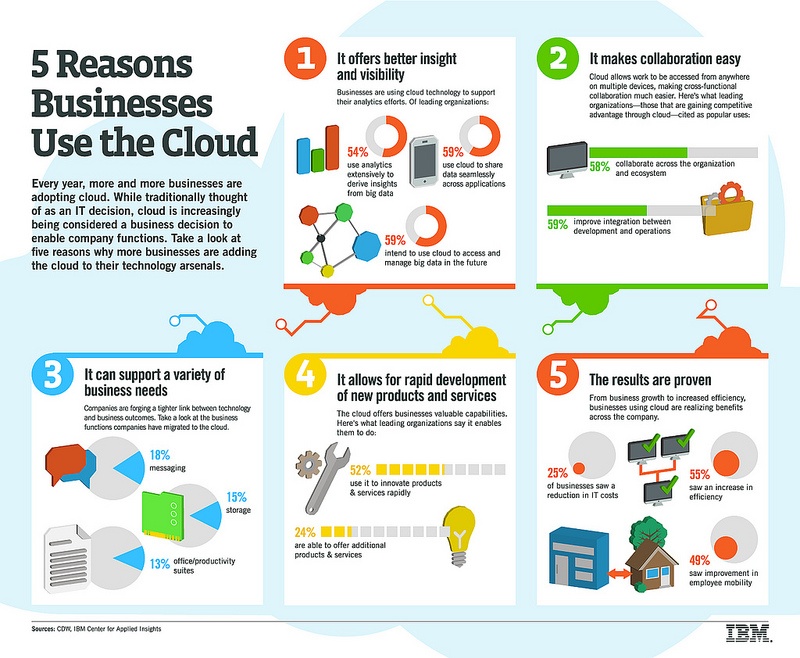
At the most basic level, cloud-based technology consist of hardware and software resources that you access through off-site based resources, instead of through an on-premise installation.The cloud also pools its resources together for higher performance and greater redundancy, instead of assigning a single piece of hardware to your business.
What Makes the Cloud Worthwhile?
With 87 percent of small and medium sized businesses already using some form of cloud technology, according to PC World, it is evident that the cloud has a strong following with SMBs. You may even be using cloud services in your business without realizing it — Gmail, Dropbox and Evernote are all commonly used cloud applications.
The cloud provides your business with a wide range of tools, from software to complete infrastructures, opening up your access to high performance technology. Instead of running your internal communication program off an aging server in an unused closet, you get access to integrated solutions running off the latest high end hardware.
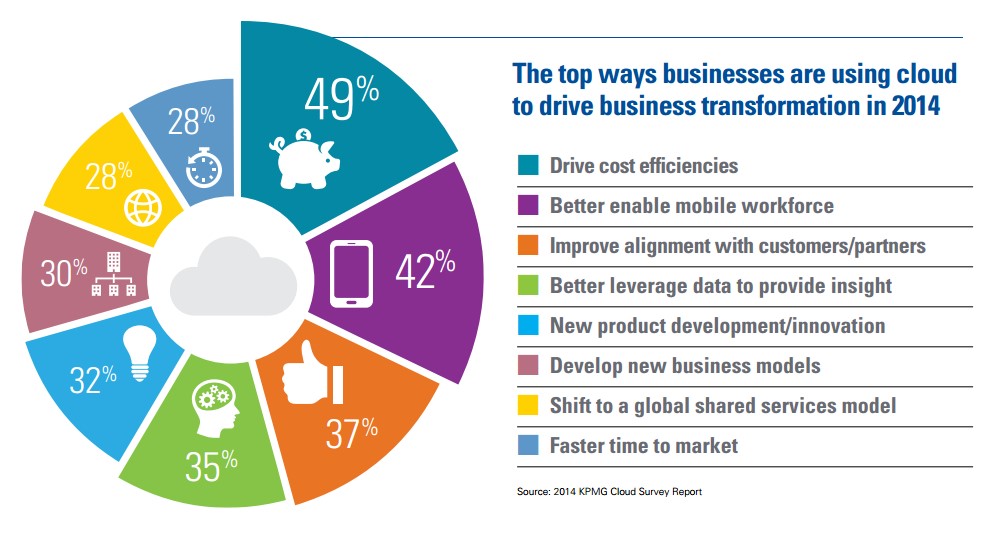
Security is a common concern for many businesses considering cloud adoption. Fortunately, the security available often exceeds what you may currently have at your own office. A study by Right Scale found that only 13 percent of companies who have adopted cloud technologies have significant security concerns, compared to 31 percent of companies who are new to cloud technology adoption.
Maintaining strong security is in each cloud vendor’s best interests, as their entire business models revolve around reliable access, data integrity and the security of sensitive information.
The flexibility offered by cloud services also make this technology budget friendly for SMBs. Many cloud vendors operate on a subscription model that may be a flat rate or a per user rate, so instead of paying for costly hardware, a large number of software licenses and the costs associated with deployment upfront, your business pays a recurring fee for access to the services provided.
Your organization can then easily scale your users or your capacity up and down as needed, because the service cost scales with your business as opposed to having to implement large projects after hitting particular usage thresholds.
Your IT security budget may be competing with a range of other expenses within your overall business budget, but with the right guidance from your IT support services team, identifying the best cloud computing solutions who place high priority on maintaining the appropriate security measures can pay off in significant savings as well as improved office IT performance.
What You Need to Support Cloud Deployment
Cloud technology isn’t reserved only for businesses with full in-house IT departments. In many cases, your small to midsize business may be examining options when it comes time for an infrastructure upgrade, and while reviewing what you currently have in place and the softwares deployed, you may start to question the value proposition associated with the higher upfront costs of having your business upgrade or replace outdated or failing onsite infrastructure.

When looking to move your office technologies forward, you want to find out the best ways possible to streamline and cut outunnecessary IT work from the outset. So what do you do once you’re all set up with your cloud services but you don’t have the IT resources to properly train and support users?
Instead of holding back on adopting technology that could vastly improve your business productivity simply because you don’t currently have the IT manpower available, bring on a IT support service provider to get your organization started leveraging cloud technology the right way from the very beginning and to keep everything running smoothly going into the future.
7 Reasons You Might Switch To Windows 10 This Year
7 Reasons to Switch to Windows 10 This Year
Windows 10 (Win10) is the next generation of Microsoft operating systems.
1. Free for a Limited Time
If you currently have computers with Windows 7 or Windows 8.1, then
2. The Start Menu
When
3. Re-Sizeable Apps
You can now re-size apps that were previously full screen-only as if they were
4. Virtual Desktops
Windows
5.
With this
6. Futuristic Biometrics
Windows Hello is a brand new,
7. Tons of Customization
Microsoft has gone from clunky and
Key Raider Malware Targets Apple iOS Devices: What is it? Who is is affected? Should I worry?
KeyRaider Malware Targets Apple Devices

This week Palo Alto Networks announced their identification of the KeyRaider malware attack, “the largest known Apple account theft caused by malware,” which to date has compromised the IT security of over 225,000 Apple accounts.
How Does KeyRaider Work?
KeyRaider targets “jailbroken” iDevices, which strips Apple devices of their built-in security measures.
Why would someone “jailbreak” their device? There are a variety of reasons users may choose to “jailbreak” their devices ranging from using banned apps to customizing control centers, but typically the reasons all boil down to wanting to use prohibited downloads or running programs which are not allowed by Apple.
By focusing in on exploiting jailbroken iPhones, KeyRaider is able to: Scrape sensitive account information and steal iTunes usernames, passwords, and sensitive payment information.
Furthermore, KeyRaider is believed to steal Apple push notification service certificates and also to disable native and remote unlocking functionalities on iPhones and iPads.
According to Stephen Coty, the chief security evangelist for Alert Logic, this means that KeyRaider can “lock your phone very similarly to ransomware that has been plaguing many individuals across the world.”
Two iOS Jailbreak Tweaks Leading to Disaster

Throughout their research, WeipTech and Palo Alto Networks identified two iOS jailbreak tweaks which are believed to have stemmed from the popular jailbreaking tool, Cydia.
The tweaks were then downloaded over 20,000 times and have compromised the sensitive information of users across 18 countries in the attack on more than 225,000 accounts.
Should I be worried? What does KeyRaider mean for my organization’s IT security?
Once More: If you do not have any jailbroken iOS devices in use, your organization is safe from KeyRaider.
If you are worried about having any sensitive information from your business being compromised by KeyRaider, the first thing you need to do is check that your organizations’ users do not have any jailbroken Apple iPhones or iOS devices in use.
Establish Policies: Prohibit Any and All Jailbroken Device Use Within Your Organization
Throughout this process, make sure to remember that KeyRaider’s success or failure relies on user victims having “hacked” their own iPhones first.
By jailbreaking iOS devices, users directly open the door to threats such as KeyRaider to compromise accounts.

It’s Safe to Say: Don’t Stay Silent
At the same time, your employees and office users must know that they are safe to report that they have a jailbroken device in use.
Otherwise, without the promise of “safety” you could suffer the consequences of a KeyRaider attack due to users staying silent, devices going unreported, and accounts being exploited.
How can I check if there is a jailbroken iPhone or iOS device in use at my organization?
Unsure if you have any jailbroken devices in place? It may be time to conduct an IT asset inventory.
If you work with an IT services provider, chances are, they already have a detailed inventory technologies and devices with access to and being supported for your business.
IT Security Is Not A One-Off Engagement
Remember, the success of your information security, IT support and ongoing technology improvement programs all require buy-in from your users.
If your people have have never seen your company’s IT policy, employees have no idea of what security best practices are or your organization still needs to be setup to facilitate ongoing updates and regular system maintenance, it may be time so seek out professional IT support services.
Feel like you need to double-check?
Reach out to your San Francisco Bay Area IT services provider to have our local helpdesk team perform a free network assessment of your business IT environment.
Instead of allowing your technology to suffer, keep your users safe from the latest malware and ransomware attacks by having full team of IT specialists ready to answer your questions and solve your problems today!
Read More
Still Stuck on Windows Server 2003? Get Your Business Back on Track
Survival Steps After Windows Server 2003 End of Support
On July 14, 2015, Microsoft stopped providing extended support for Windows Server 2003 (WS2003). Ending this support meant no more security updates or incident support for customers who retained the older operating system.

While this change didn’t cause everyone’s computer to suddenly stop working, implode or jump the track, it does mean that over time, both security and safety could be compromised. It also means that if you are still using WS2003, some changes need to be implemented to ensure that your company remains safe, secure and compliant.
Change In Product
WS2003 has undergone a number of changes since its release in April 2003, including two major updates in 2008 and 2012. However, many companies did not upgrade. An AppZero Study reported that more than 10 million computers were still using WS2003 just prior to the cessation of all support. Some of their reasons for retaining WS203 were:
- Lack of urgency for switching operating systems as long as Microsoft continued to offer support for WS2003
- Difficulty modifying customized or packaged applications software to the new operating systems
- Financial concerns, i.e. cost of upgrading existing system and software
What If It Still Works?
Although your computers and businesses will continue to function, problems will accumulate over time.
For instance, lack of security updates leave your system vulnerable to new viruses or inventive hacking.
Power outages may mean crashed systems, lost data and impossible recovery.
Existing software applications may no longer function or be available as companies adapt to the newer operating systems.

And for organizations tied to compliance regulations (such as healthcare and HIPAA or businesses who deal with credit card information and PCI), compliance issues will emerge sooner rather than later.
Furthermore, simultaneously putting your business through a server migration in addition to a compliance assessment can put your business operations at risk as the demands on your internal resources spikes and accelerated deadlines are being enforced by auditors, industry regulators or your clients themselves.
Instead of placing your organization under the gun of tight timelines to hit a compliance assessment date, get started now to make sure your your migration is built to last.
What To Do
There are steps you can take to keep your computers — and your business — running while you migrate to a new operating system. Ed Tech Magazine recommends the following actions:
- Step 1: Conduct an assessment and determine which applications are still running on Windows Server 2003.
- Step 2: Prioritize your applications by importance and ease of transition.
- Step 3: Test your applications with free trials of newer platforms before purchase.
- Step 4: Build a migration plan.
Get Help
If these steps seem overwhelming, your Bay Area IT support specialists at Bay Computing have years of experience and are available to help your organization avoid complications and safely navigate the transition.
Instead of struggling through the process alone and running the risk of prolonged downtime, let our team architect your implementation plan, complete your migration and test your applications to make sure your systems are configured to perform optimally and to help you avoid future business interruptions.
One Stop Shop for Small Business Server Migrations
Our team of experts can help you get started by conducting your free onsite network assessment and then help prioritize your needs throughout each step of the the migration as they work with your team to develop a thorough understanding of how your team uses each specialty application.
You invest in technology to help improve your business operations. Make sure your business continues to run uninterrupted as you run your company and accomplish your goals, all while strengthening and moving your IT infrastructure into the future.
Don’t wait until disaster strikes or a deadline is looming. Contact your Bay Area IT support specialists and get your business back on track today!
Read More
Healthcare IT: Addressing Challenges of Information Security
![Healthcare IT HIPAA EHR Management Support Healthcare IT HIPAA EHR Management Support]() Information Security: What’s It Mean for Healthcare IT ?
Information Security: What’s It Mean for Healthcare IT ?
The pervasive use of Electronic Health Records (EHR) has made sharing patient information significantly easier. While this has dramatically improved the quality of patient care, how secure is your confidential patient information?
Information Security in Health Care
The goal of EHR is to collate information for better patient care and encourage smarter spending. But what happens when patients are wary of the accuracy and confidentiality of their EHR? They may refuse to divulge information crucial to getting proper medical care.
Security Breach Risks
Ideally, healthcare IT should be an invulnerable fortress. But is it really? Let’s take a look at the weak spots that need improved fortification.
Endpoint Encryption
According to this Forrester report, several healthcare organizations get by on a miserly security budget, and only 43 percent of healthcare firms have a comprehensive data security budget. As a result, securing endpoint data does not get the priority it should. Very few healthcare organizations use file-level or full-disk encryption.
Hackers
Progressive technology is a breeding ground for sophisticated hackers. Hackers are more interested in financial fraud and identity-theft-related data, such as a patient’s social security number, than health-related information. In fact, recent months have seen a 600 percent increase of such attacks.
Healthcare Workers
Healthcare workers’ passwords are often the first breach in the battlefront of patient information security. For example, sometimes they forget to log out of their work station. Such mistakes lead to about 25 percent of security breaches, including identity theft and access to patient information records. Unless employees are given adequate security training, all security revamps will only be wasted effort.
Bring Your Own Device (BYOD)
BYOD permits healthcare employees to access work data via their personal devices. This trend adds a whole new dimension to patient health information security. Without an inclusive, operable and strictly followed security system in place, BYOD is the equivalent of encouraging a jewel thief to gate crash a celebrity wedding.
Business Associates (BA)
Most external threats to patient information security are due to the carelessness of BAs who have access to such information. They are the cause of about 20 percent of recent security breaches.
The Technology-Expertise Gap
Often, even if healthcare organizations have the budget to implement the right technology to detect pitfalls, the security technology remains unexploited because most in the organization are not trained and equipped to implement it.
The key to countering security threats, whether external or internal, is awareness and training. Training should be an ongoing process in order to address changes in technology and new threat sources.
Read MoreWindows 10: Helping Your Office Bridge the Gap Between PCs and Tablets
Windows 10: Helping Your Office Bridge the Gap Between PCs and Tablets
When
Universal Apps
Apps from the Microsoft App store
Redesigned User Interface
One of
Seamless Tablet Mode
Some of the
Windows 10 learned many lessons from Windows
