Latest News and Resources
EHR HIPAA Compliance: Essential Guidelines
Five Steps: Is Your EHR Managment HIPAA Compliant?
The advent of electronic health records (EHR) have improved many aspects of health care: faster data sharing, better care coordination, increased patient participation, reduced errors and more.

But it also means that additional steps are necessary to ensure that your patients’ electronic protected health information (ePHI) is protected and that your practice is compliant with the Federal Health Insurance Portability and Accountability Act of 1996 (HIPPA).
Five Starting Steps: EHR and HIPAA
The implementation and maintenance of the following five steps may require specialized expertise, which should be available among your technology support staff. These experts can help your EHR operations run smoothly and help you navigate complex technology-related challenges.
Analyze Risk
The first step in HIPPA compliance is a risk analysis, which can identify potential threats. According to the Office for Civil Rights, a risk analysis involves identifying all sources of ePHI and all potential risks to confidentiality. Once identified, steps can be taken to protect, mitigate, or correct for problems.
Encrypt ePHI
The second step is technological: encrypting ePHI. HIPPA rules require, “the use of an algorithmic process to transform data into a form in which there is a low probability of assigning meaning without use of a confidential process or key.” Your technology services team can help ensure that the right IT solutions are implemented to keep your data properly encryptedat all times.
Secure Hardware
The third step is similar to a locked file cabinet; it provides access only to those with a key. The United States Department of Health and Human Services recommends both physical and technical safeguards for ePHI. Physical safeguards limit access to the hardware site and provide use restrictions to workstation facilities. Technical safeguards include:
- Unique identification
- Passwords
- Automatic logouts
- Emergency access procedures
Establish Clearance Levels
The fourth step is establishing an access hierarchy. Make sure you have clear definitions of who can see what information and for what reason setup properly by your computer support specialists.
As part of this process, your practice may want to create processes to assign access rights based on position levels within your organization (depending on the size of your practice) to serve as an extra precaution instead of relying solely on ad-hock access approvals
Conduct Audit Reports and Periodic Evaluations
The final step is evaluating how well your implementation is performing. This involves routine audits of which users have accessed sensitive information and the review of any healthcare IT related problems and processes observed.
As a busy medical practitioner, you are busy dedicating yourself to providing the best patient care possible. Now with HIPAA Compliance coming down the pipeline, you and your practice may be feeling overwhelmed by the seemingly endless list of requirements necessary to be HIPPA compliant.
Work with your Bay Area IT services provider to ensure that the proper roles for compliance are defined and to establish the policies and procedures necessary to proactively prevent, detect, contain and correct security problems. Our organization is readily available to answer any healthcare IT questions you may have or to set up a free assessment of your HIPPA compliance readiness.
Read MoreHow Healthcare IT Support Enhances Patient Care
Healthcare IT: Free Up Your Practice to Focus on Patients
Top-rate medical practices are often let down by sub-par technical support, so it may be time to source the professional-caliber IT support services you need. However, that is sometimes easier said than done, and it’s important to know what support services your practice requires to protect your electronic health records (EHR) and the Electronic Personal Health Information (ePHI) you deal with each day.

As a physician, worrying about your healthcare IT services is not what you need to spend your day focusing on. Your job is to tend to your patients, and a company that offers a skilled support service enables you to do that. Support for your EMR/EHR software (such as NexTech) includes preventing inappropriate use, malware protection and training in best practices.
Inappropriate Use
Inappropriate use often involves interaction on social media, such as Facebook and Twitter, or even on your own practice’s website. Research shows that displaying ill-chosen photographs, using discriminatory language, violating patient privacy and posting negative comments are ways that medical practices may overstep ethical rules and legal regulations. A professional IT company can enable the monitoring and disabling of inappropriate use on practice computers, whether it’s inadvertent or deliberately malicious. This enables you as a physician or office manager to devote yourself to what you are specialized in instead of having to waste precious time on policing employees.
Antivirus and Malware Software
Viruses, worms and malware destroy and steal or even ransom medical records and sensitive ePHI, so it’s imperative that your practice has the proper protections in place against them. Like the human variety, viruses that attack computers are constantly mutating, doing so through the workings of Internet hackers. An IT firm of good standing always keeps your office up to date with the right selection of antivirus solutions, preventative programs and safeguards against malevolent cyber invaders, giving peace of mind to you and to your patients.
Best Practices to Avoid Malicious IT Attacks
Cyber criminals are constantly searching for valuable, vulnerable data such as:
- Names, email and physical addresses of patients and employees
- Social Security, medical ID numbers, Protected Health Information (PHI or ePHI)
- Payment card info (regulated by PCI-DSS, or Payment Card Industry Data Security Standards)
This information is usually sold in bulk to the highest bidder and used for a variety of nefarious activities. Don’t risk losing your patients’ trust simply because of weak IT management.
Implementing industry standard best practices to ensure your business and office operations are secure against cyber-attacks is not always simple.
Training staff, using strong passwords that are frequently changed and limiting network access are just the beginning when implementing the necessary procedures.
Mobile devices are particularly vulnerable to cyber and physical theft, so and all patient related data needs to be encrypted before being sent across public networks. All devices, whether mobile or office-based, should be frequently backed up to preserve data. A trustworthy IT services company can develop and execute a cyber-security strategic plan for your practice.
Choose Carefully
One of the challenges faced by physicians during 2015, according to Medical Economics, is keeping abreast of modern technology. A fairly significant number of medical practices have, to their detriment, bought low-cost EHR software only to discover that support services were sadly lacking or simply nonexistent. Physicians Practice recommend that one of the most effective ways of protecting your practice against data breaches is to contract with IT support service firms that are familiar with EHR and compliance issues.
Concern about problems such as inappropriate use and cyber-attacks from hackers takes physicians away from what they do best — caring for patients. Contact our support team at Bay Computing for information about best practices to prevent malicious invasions of your electronic systems.
Read MoreWhat is Rombertik? Latest Spyware Attacks Your Computer if Detected
What is Rombertik? Latest Malware Attack Triggers Destruction Tactics Upon Detection
Just yesterday, security experts discovered the latest strain of malware, nicknamed “Rombertik”, a specialized “wiper” malware smart enough to actively take precautions to help itself avoid detection.
But most importantly: If Rombertik even suspects, let alone confirms malware analysis, it will activate a number of “self-destruct” type functions on the host computer it has infected to stop you in your tracks. Here’s hoping you have updated backup solutions in place…
Why self-destruct? Doesn’t that harm Rombertik’s goals too?
One of the greatest dangers of Rombertik is the malware’s obsessive secrecy, for its creators are determined not to allow malware analysis to be run on their latest masterpiece. Chris Stobing has gone as far as dubbing “Suicide Bomber” of malware attacks.
Why such an extreme title? As soon as it suspects detection, Rombertik overwrites all vital information on your computer, which in turn makes you lose all of your data and forces you to reinstall your operating system and restore your files from backups.
How does it know? What triggers Rombertik’s destroy function?
In the beginning of its attack, as soon as it is up and running, Rombertik completes multiple checks to ensure that it has not been detected.
According to the Talos team of cybersecurity experts responsible for its discovery, Rombertik, “is unique in that it actively attempts to destroy the computer if it detects certain attributes associated with malware analysis.”
How is this conducted? Don’t most malware attacks try to avoid detection?
While most malware attacks these days include instructions and commands to help them evade discovery, Rombertik will automatically compute a 32-bit hash and encrypt its victim’s hard drive if at any point the infection suspects a disturbance to its operations.

Furthermore, the Rombertik’s infection methodology, “incorporates several layers of obfuscation along with anti-analysis functionality,” (meaning that it has the capability of actively fighting off malware analysis in multiple different ways).
The attackers have also developed a way of evading sandboxes, which have traditionally been overcome by enforcing extended “sleep” periods before executing in order to get past sandbox timeouts.
As security specialists identified this method, sleeping lost effectiveness, which is why Rombertik instead chooses flood memory by the writing of a byte of random data to memory 960 million times.
By exploiting the scale of this new strategy, Rombertik is able to consume time without being flagged as sleeping, and also manages to flood application tracing tools with over 100 gigabytes of logged data, which further complicates and derails any potential analysis.

The Final Punch/ Going in for the Kill
Remember that 32-bit hash we mentioned? As a final anti-analysis tactic, Rombertik will computer a 32-bit hash of a resource in its host machine’s memory, which it then compares to the timestamp of is original sample upon creation. If the malware discovers that the sample has been accessed or altered in any way, Rombertik goes into “Destroy” mode.
This Includes:
1.) Overwriting the Master Boot Record (MBR) of PhysicalDisk0, which will fry your machine and leave it inoperable
2.) If it is unable to overwrite your MBR, Rombertik will destroy all files in the user’s Home folder and encrypt each one using a randomly generated RC4 key.
3.) Following the completion of MBR overwrites and Home folder encryption, Rombertik restarts its victims’ computer, but not without implementing code which forces an infinite loop and stops the system from being able to continue onto fully rebooting.
So what is this malicious spyware attack after?
Its sophisticated software for attacking to avoid detection is what makes it unique, but in terms of data capture, Rombertik isn’t picky.
Once it has infected your computer, it gathers any and everything that you do through monitoring all of your behavior on the we and each and every keystroke that you make.
Why? By capturing all of your activity before transmission, secure methods such as HTTPS become irrelevant. This method of lying in wait methodology helps Rombertik evade detection while it discovers the details of your business and your users’ sensitive data.
Once Rombertik has succeeded in transmitting the the data it has gathered while spying on you, specialized scripts can be used to identify your login credentials, passwords and payment information from the logs ofyour behaviors on the web and each keystroke that you make.

How do I keep this from happening to my business?
Considering that Rombertik relies heavily on spam and phishing attacks, the best place to start is by implementing strong security practices. For more information on how you can avoid malware attacks, check out this blog from one of Bay Computing’s senior technicians, Matt Simpson.
Need a quick overview? As an intro your organization should:
- Make sure anti-virus software is installed on all machines accross your organization
- Regularly update your anti-virus solution
- (The best option is working with your IT managed service provider to implement a centrally managed antivirus solution which automatically takes care of all updates for you)
- Teach users not to click on attachments from unknown senders or messages which seem out of place from known senders
- (Think safe, not sorry when it comes to malware)
- There is never a failproof solution, but implementing and following best security practices is one of the most effective methods out there
- Implement the right Spam filter to block suspicious emails and attachment types
- Utilize backup and data recovery solutions to ensure that your business continuity is protected, no matter what happens.
- Double-check (and then triple-check) that your backups are set to occur regularly and that they are completed successfully
- Work with your technology provider to ensure that your computer network services are implemented with a threat-centric approach which incorporates protections across your extended network and your full business IT environment.
If you have any questions about implementing the right security solutions for your organization, need help fighting your way through a malware attack or are simply looking for the right IT service provider for your Bay Area business, contact us today!
Read More
How To Implement Best Practices For Business IT
As a business owner, it can be overwhelming trying to stay up to date in the latest and greatest best practices for business technologies, but you know you need to keep your network, systems, and data safe in order to keep your office operations humming along.
Having a comprehensive IT management plan is a key step in the right direction. The problem is, there is no single set of rules or protocols that will work perfectly for every business and accross all office needs.
When you work directly with an IT services provider, a team of experienced technicians helps you identify the technology needs of your organization and employees, and then designs your customized, reliable and comprehensive IT solutions plan.
As for mapping out the details of each IT solutions plan, the requirements and specific policies will vary greatly based upon each organization’s:
- Hardware limitations
- Industry-related security requirements (HIPAA requirements, PCI Compliance, etc.)
- Data transfer
- Data access demands
- Backup needs and requirements
- Business obligations for unified configurations
But keep in mind, there are a number of fundamentals each business must consider when developing, maintaining or revamping their IT systems and networks. Here is a walkthrough to cover the basics of office IT necessities to help you cover the best practices for your business.
1) Disaster Recovery and Data Backup

First and foremost, when your business has crucial data, your office IT systems must have the right backup solutions in place. Whether you run a botique wealth management firm or a multi-office cosmetic surgery practice, data should be backed up religiously.
Not only does the success of your business depend upon having reliable, up-to-date versions of your files, but you can’t allow a natural disaster, theft or rogue user take down your operations!
A key component of protecting your business is creating the processes and procedures to properly assign the responsibility for backing up your business data each day.
Yet the hardest part can be making sure they are actually implemented and completed daily to ensure that your day’s work doesn’t go missing.
When you ensure that your information is stored, saved and replicated, you lay the foundation for proper business continuity and enable your business’ disaster recovery planning
Here are some of the most common data backup solutions used by local businesses and organizations:
- Manual Back-Up – One of the simplest ways to back up data is to move all your information into one file, and then transfer that file to a portable hard drive.
- This is a common data backup ritual for small businesses, but it has many drawbacks and can present significant risks to your Office IT:
- When backing up large amounts of data, it is a slow, tedious process
- The hard drives you use are just as likely to get lost, corrupted, or damaged in some sort of disaster scenario (fire, earthquake, etc.) if they are stored in the same location
- If you do keep your external drives at a separate location, it is quite common to see actual backups fall behind and out of date as drives must be transported round trip and time must be allocated for periodic backups.
- Without automated processes in place, your business becomes reliant on the manual process and employees not getting side-tracked by daily work operations
- Remote Servers – Many businesses backup their data by transferring it to a set of computer servers at another location.
- This is a form of secure P2P file-sharing called “friend-to-friend,” and it is especially helpful for businesses that have multiple offices.
- There chance of data getting stolen along the way is lower than with other options, and the information will be stored safely in multiple locations. However, there is still the risk of both servers being destroyed in a large-scale disaster situation.
- Cloud Storage – One of the newest, most advanced forms of data backup is Cloud storage, which stores your data on multiple remote computer servers.
- These cloud servers are maintained by a hosting company that ensures the data security and redundancy of their services.
- In terms of continuity, cloud technology offers one of the strongest forms of data backup solutions as it involves having multiple copies of your data created, accessible from any location with a secure Internet connection.
2) Security

The modern world is overrun with threats from cyber criminals attempting to exploit people online.
Some are sophisticated hackers looking to steal money or electronically stored protected personal health information from secure computer systems.
Others may be mere spammers attempting to inundate your company with junk mail or advertisements with hopes of hoodwinking your employees into the latest cyber scam.
Their weapons may be relatively simple (phishing attack), slightly more advanced (spear-phishing attacks) or possibly quite advanced and sophistacted in their methods (Rombertik and “wiper” malwares)
There are even “hackers for hire,” who are the digital mercenaries hired by competitors to crash your systems or harm your business reputation. Whatever the threat, you must stay prepared.
Know that different operating systems require different malware protection, but there are some basic data security tips that will keep your office IT system as foolproof as possible. Consider the following:
- Choose unique passwords
- Diversify your password
- Regularly update your anti-virus software
- Avoid pop-ups
- Limit Administrator access to one person
3) Maintenance

When it comes to office IT, it is important to make sure that you have your computer maintenance consistently covered.
This includes everything from server maintenance to scheduled software updates, and the bigger your invesment, higher the likelihood that you should also invest in an extended manufacturer’s warranty.
Whenever our clients make major investments in their technologies, we always investigate the best warranty options for them and help them evalaute if the investment is worthwhile, depending on the terms.
There are far too many variables to accept hard-line rules across the board when it comes to IT maintenance. The only thing you can know for certain is if you have the right resources on your side to ensure that you will always be able to handle dealing with any unexpected tech support problems or even IT disaster recovery necessary situations.
Basically ask yourself, “Do I know who to call?”
Computers break like everything else, and when your data is lost or your work flow is stalled, this can be a disastrous time to try “DIY” computer maintenance. Having a managed IT services provider is the best way to get your equipment back up and running in no time.
4) Disaster Planning

Disaster planning is an integral part of any foolproof IT system. Whenever there is a large scale natural disaster (like the 2011 tsunami in Japan) businesses can be destroyed just as easily as homes. If you employ local backup solutions and lose your data along with your office/equipment, you may never recover. This is why you need a plan of action for the worst possible scenario.
Disaster preparedness, or business continuity, includes 3 important aspects:
- Data Recovery – You need to recover all of your data from the backup location (and immediately “backup the backup” since the first backup becomes your original)
- Replace Damaged Equipment – This can be difficult if an office or computer server was destroyed, but it is important to salvage whatever you can. Having a well-designed BYOD policy may also allow you to get by in the short term.
- Data Access – If your office was destroyed or rendered inaccessible (but your data was stored remotely) you need a way to access the backups while you sort things out. This is where Internet-enabled cloud computing becomes so valuable.
While technology advances each and every day, making sure that your IT is built upon sound foundation will always be a wise investment to enable your company to succeed.
As you seek out the best tech solutions and IT services for your business, make sure you have the right partner on board to help you develop the best strategy for storing, accessing and protecting your mission-critical data and for securing your network and systems.
There’s a reason that such for a wide range of businesses throughout the Bay Area depend on managed services providers:
When you work with professional IT services experts, your business becomes free to focus on your core competencies, key clients and most crucial projects to help keep your clients happy.
If you are interested in learning more about what options would work best for your organization, Contact Us at (925) 459-8500. With years of experience and our friendly team of technicians, Bay Computing is proud to serve as one of the premier IT service providers in the East Bay Area!
Read More
Best Practices in Securing Mobile Healthcare Devices
Best Practices in Securing Mobile Healthcare Devices
Many physicians and practice support staff participate in bring your own device (BYOD) arrangements at work. Having a BYOD policy is both convenient for staff and cuts the cost of supplying staff with electronic hardware. However, without proper technology management BYOD can easily turn into a nightmare with regard to security, so follow these best practices to ensure your practice is safe.
Authentication and Encryption of Mobile Devices
Strong passwords and dual or two-factor authentication (2FA), which involves the entering of a password and a personal identification number (PIN), greatly aid in preventing the illicit use of mobile devices.
Encryption of mobile devices ensures that if your equipment is lost or stolen, the data cannot be read by unauthorized users. If your practice has a breach in security, you will have to prove to the Department of Health and Human Services (HHS) that your devices are encrypted and that you have an encryption plan in place; if no encryption is being used, your practice will be in violation of HIPAA compliance requirements and is liable to get a fine.
Develop a Mobile Device Policy
A written mobile device policy is also essential if you have a BYOD policy for personnel. The policy should include:
- Who is allowed to access the practice network?
- What medium of access is allowed? Public WiFi networks are vulnerable, while virtual private networks (VPNs) are more secure.
- Which devices are acceptable?
- What data can be stored on the devices?
Other elements to incorporate in a mobile device policy are appropriate use, support and costs. Hand out the policy document to all staff involved in the BYOD scheme, and have them sign it to indicate that they understand the policy and that they agree comply with it.
Keep Up to Date with New Technology
Advances in mobile device management (MDM) are continually being made, and it’s important to know what’s available. For example, MDM software lets administrators know which devices are accessing data and from where, gives the ability to wipe lost or stolen devices completely clean, and monitors data that is coming into and leaving the network. Secure containers keep personal apps separate from practice data, preventing inadvertent divulging of the electronic protected health information (ePHI) of patients.
Best Practices Training for Staff
All BYOD users need to know how to activate security features, how to identify “friendly” apps, and to have guidance and controls implemented to ensure they know where it’s safe to upload sensitive data such as ePHI to. Your practice needs establish this technical know-how in all of your employees and get them on board with mobile device security as humans are most often the weakest link in the cyber- security chain.
Partnering with a reputable IT services company smooths the way to your successful implementation of mobile device security software. Contact the team at Bay Computing for advice and information about how to secure the mobile devices used each day in your medical practice.
Read More
Office IT Tips: DIY Internet and Router Troubleshooting
Simple Internet and Router Troubleshooting: DIY Tips for the Office
Modern information technology is a wonderful thing – that is, as long as it’s working. When it fails to do so, the results can range from a bad case of nerves to lost revenue for frustrated business owners.

Fortunately, many computer-related maladies are fairly easy to fix. With that in mind, here are some simple Internet and router troubleshooting tips:
1. A new router fails to connect to the web
While this has many possible causes, a surprisingly common issue is that the modem is still attuned to the old router. To solve this issue, disconnect the network and power cables from the modem and from the new router. Leave everything alone for 30-60 seconds. Then reconnect the wires to the modem and wait until the little light that says WAN/Internet is burning. Then reattach the router cables, switch the router back on and try surfing the net.
2. Internet connection is spotty or non-existent
As with the previous issue, this can be caused by numerous problems, including overheating. To find out if this is the problem, simply place your hand on your router. If it feels uncomfortably warm, then move it to a spot where it gets plenty of airflow; you may even want to unplug it for a while to let it cool. If it works fine afterwards, then keep it in a well-ventilated location going forward.
3. A wireless connection runs slowly or frequently fails to work
Often a poorly placed router is the cause of this problem. All sorts of things can interfere with wireless signals, including brick and concrete walls, electrical wiring and other electronics. Try moving the router to a different room or, if that’s impractical, to a higher spot near the same location. You can also try moving your computer closer to the router.
One common yet unexpected office IT obstacle can stem from having your office microwave located too close to your business technology equipment. If you have a microwave in your business, make sure it is properly stored away from your wireless router if at all possible! If any of these steps help to solve the issue, then you’ve found the root of the dilemma.
4. Your Android tablet won’t connect to your network
With more and more people using mobile devices these days, this is an especially common issue. One quick fix that often does the trick is to go into your system settings, find the network to which are trying to connect and choose the “forget” option. Then try reentering the network password. This causes the system to flush out old, obsolete connection information.
5. Your wireless printer won’t connect to your network
The culprit might be your security suite. You might need to configure its settings to allow the printer to work. Avoid disabling the suite, however, as this may expose your system to malware.
If you’ve gone ahead and tried each of these simple Internet and router troubleshooting tips but find that they don’t take care of your office technology problem, then you may benefit from partnering with professional IT services support specialists.
When you have a dedicated team on your side, identifying the root causes of your technology issues is suddenly a priority and gets you on the road to keeping your business operations running smoothly, reliably and to maximizing office productivity. Contact us today to schedule your free business consultation and get started identifying the best options for your business!
Read MoreWays Professional IT Support Helps Your Business Succeed
6 Benefits of Outsourcing IT Services
Modern information technology (IT) is both amazingly useful and annoyingly imperfect. Computers freeze, connections go down and viruses infect. When these problems occur, having the right IT professionals can make the difference between a minor bump in the road and a crisis that threatens your company’s ability to survive a disaster.

As you research your options and consider how to best meet your IT needs, here are six of the most common reasons Bay Area businesses choose to entrust these key responsibilities to a dedicated professional IT support firm:
1. To level the playing field by harnessing the power of seasoned experts
Everyone knows that major players like GM, eBay and Amazon have the best IT professionals money can buy. This can create disadvantages for smaller firms that must make every dollar count. One way to even out the odds is to work with an IT services provider.
When it comes to diagnosing technology issues, experience in the field can be equally if not even more important than formal training or job title.
If your company depends solely on a limited (often times single) internal resource, as soon as that person is tied up, all of your other technology needs get pushed to the side where they rapidly start piling up…Soon enough, your users learn that whenever they have an IT problem, they are better off trying to fix it themselves (which opens the door to a whole host of new problems).
Instead of struggling each time your office technology starts having problems, you can turn this fact into an advantage by outsourcing your help desk support to a team of experts.
2. To enjoy the cost savings that come from economies of scale
Over the years, many clients who choose t
o work with external IT consultancy services have found that it is actually often more cost-effective than handling technology management in-house.
When you eliminate the need to source, screen, interview and vet candidates, you eliminate the time, cost and anxiety associated with struggling to find the best technicians possible for your available budget.
Instead of struggling to onboard a new technical employee, working with a it managed service provider allows your organization to save time, money and internal resources to help free up capital that’s needed elsewhere, thus enhancing efficiency and profitability.
3. To focus on your core competencies
In today’s business world, it no longer makes sense to be a Jack or Jill of all trades. Letting others handle your IT support services can enable you to concentrate on what it is that you do best, whether that’s providing the best care possible to patients within your healthcare practice or providing financial services to clients seeking to plan for the future in the San Francisco Bay Area.
4. To enable implementations of cutting-edge technology
Not only does outdated technology limit your productivity, it can even pose a threat to your business operations and cybersecurity.
Some enthusiasts would even argue that yesterday’s technology is nearly as useless to a modern enterprise as stone knives and smoke signals, but the right managed service provider understands how to take the specific needs of your business into account and to help facilitate the transition from legacy systems to the latest technologies.
Yet finding and hiring the right specialists with the requisite knowledge could take weeks or even months by using an in-house approach. You won’t have that worry when you outsource your IT services to a local IT support firm- a dedicated managed services provider takes pride in helping your company stay on top of the latest technologies and guides you through selecting the best solutions to meet your office and business technology needs.
5. To enjoy the benefits of ongoing relationships and deep understanding of your needs without the HR headaches
Hiring, training, onboarding and otherwise investing in new employees is always a gamble- Perhaps they will work out, perhaps not. Even when your new hire has the technical skillset necessary to complete their job responsibilities, there are a number of variables which can pose a threat to your success. Personality and corporate cultural fits, work ethic and management requirements, or even external influences such as staffing during an unexpected departure or employee illness can leave you unexpectedly stranded/ high and dry. You can avoid these uncertainties by letting trained specialists take care of your IT needs.
6. To enable you to conserve your mental energy
If you’re looking to improve the quality of your worklife and up your office productivity, get started on the path to progress with a free network assessment today.
How Healthcare BYOD Policies Affect Network Security
How Healthcare BYOD Policies Affect Network Security
Healthcare organizations
Simultaneously, technologies are also evolving in
Capability and Efficiency
Actual bandwidth requirements depend on several factors such as the location, number of users, real-time
Protect Your Network
A
Segment Your Network
Isolate the Electronic Health Record system on the network along
Detect
Install an intrusion detection system as it will drop
Audit Your Setup
Workstations accessing the EHR system must comply with
Review All Privileges
Manage user rights centrally and
Conclusion
Although HRSA does not mention
HIPAA Audits Made Easy with the Right IT Support
How to Show HIPAA Auditors Your Practice’s Good Faith Effort
Since the enactment of HIPAA in 2003, patient privacy has continued to be a priority for the federal government. To ensure compliance, the Office for Civil Rights (OCR) is performing a series of on-site and desk audits. Desk audits can be particularly tough, as auditors leave little time to comply with audit information and develop appropriate policies or conduct a comprehensive risk assessment. With entry-level HIPAA violations starting at $200,000, practices need to have policies in place is before an audit occurs.

What Auditors Want
Like their IRS counterparts, HIPAA auditors are looking for a good faith effort to follow the law. They’ll ask to see a comprehensive risk management procedure that outlines how each potential risk is handled. In addition, they’ll assess your breach policy, including how patients and the media will be advised of a potential data breach.
Finally, auditors will ask for complete documentation of all training for HIPAA compliance. HIPAA training, in their eyes, is not a single event, but continuing education.
Best Practices to Pass an Audit
Before you are notified of an audit, perform a risk analysis. Take into account all factors concerning HIPPA auditors—listed below—while performing your risk analysis.

Proper Documentation
Document the practice’s plans for data management, security training and notifying patients in the event of a data breach. These plans should be in writing and available for an auditor’s review.
Password Security
Keep a secure password policy. Passwords should meet security standards and not be stored where they are easily accessible.
Proper Encryption
All Protected Health Information (PHI) must be encrypted. Scans and images must be encrypted when being sent or received, as well.
Use SSL for Electronic Health Records
All electronically-transmitted PHI or EHR data, like test results or scans, must use SSL when accessed via the internet. Since most practices can access patient data from hospitals, SSL is vital.
Designate a Security Manager
Each practice should have a point person who acts as the security manager and is responsible for the encryption techniques. One or two additional staff members should also be familiar with the encryption in case the security manager is unavailable.
Use VPNs to Access Patient Data Remotely
Any staff member who accesses patient data remotely must do so over VPN (Virtual Personal Network) to ensure security outside the office environment.
Make and Practice a Disaster Recovery Plan
A disaster recovery plan must be documented and should be practiced at regular intervals.
Sources:
Get the IT Support Your Bay Area Practice Needs
Your Bay Area Medical Organization Needs Healthcare IT Pro Services

Professional IT support is a valuable investment for any business, but it is an especially important consideration for healthcare providers. Given the healthcare industry’s reliance on computer systems and the sheer amount of highly sensitive personal data healthcare practices retain, technical support is necessary for a secure and efficient office.
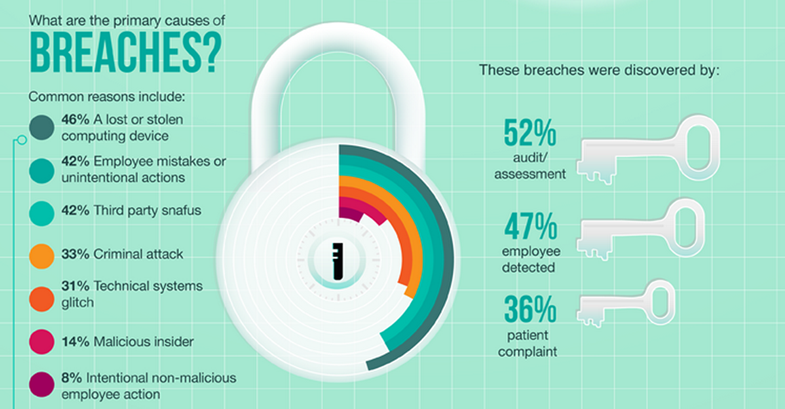
Security
Professional IT support offers many direct benefits to healthcare providers. Arguably, one of the most important components of your office technology support it IT security. Data breaches are a very real and increasingly common threat. Statistically, the vast majority of medical practices, regardless of size, area or specialty, will experience at least one data breach. Nearly half will suffer five or more instances of data theft. Given highly sophisticated theft methods and the vast amount of electronically-stored data, IT support is not an option, it’s a necessity. Professional technology support can customize security options for your office. Should a breach occur, IT will move quickly to neutralize the threat, restore operations and reduce damage.

Support
Computer systems, particularly those powerful enough to carry a medical practice, require maintenance, updates and repairs, all of which are time consuming and often frustrating. Should a system fail, even briefly, it may be difficult or impossible for a practice to continue until it’s fixed. By retaining support, offices have the assurance that IT professionals will respond quickly. This results in drastically reduced system downtime, which directly increases the office’s performance and efficiency.

Reliability
Solutions provided by professional IT Support are reliable. Whether tech support works with your practice on security issues, system performance, your network, database assistance or storage, professional IT support will work to develop the best solution for you. IT professionals will provide necessary support to ensure operations run smoothly.
Having local Bay Area IT support on-call significantly reduces the strain on doctors and staff, which results in more time with patients, more energy and effort to direct into the practice. This means increased efficiency and overall improved productivity as well. Not only do IT professionals assume a frustrating and time-consuming burden, they provide peace of mind, ultimately allowing you to spend your time providing care to your patients.
Read More