Thanks to programs such as 20/20, 60 Minutes and countless pop culture references, we have all heard stories of famous email scams, like the infamous Nigerian prince with a sudden windfall who needs you to send him your bank account number.
Archive for the ‘Uncategorized’ Category
Hail Hydra: How Cyber Attacks Are Like Marvel’s Hydra
How Cyber Attacks Are Like The Hydra
Data Loss Prevention: Overcoming Fear Of Failure
We all fear failure. And for those of us working in technical IT support, the two words which immediately strike fear into even the hardiest of souls are – Failed Array
To explain what a failed array is you first need to know a couple of things about computer servers.
And to get us started, let’s answer:
What Is An Array?
An array is a series of hard drives that can be combined in multiple ways to appear as a single large drive. Unlike most desktops, computer server systems often have two or more hard drives attached to them in what are then called redundant arrays, or more commonly:
RAID (Redundant Array of Independent Disks)

How To Stop Malware Attacks – Six Easy Steps Keeping You Safe
In my last blog post, we discussed the basics of malware, reviewed the conditions malware requires and also introduced a few of the most common forms that it takes. Now that you’ve got a basic understanding of “what” it is, it’s time this IT support technician taught you how to avoid malware attacks before they can take hold of your systems.
Your IT Technician’s Top 7 Tips to Keep Your Business IT and Networks Safe
Want to Keep Your Network and Your Business Safe?
Here’s What Your Employee End Users Really Need to Know: Advice from Your IT Support Technician

One of the most common things that people forget when thinking about office technology and network management is actually one of the its important elements: the basic security and daily habits of end users.
While those of us who work in IT solutions can put as many locks on the gates as we can possibly think of, it does absolutely NOTHING, if the people who actually use the business network don’t use, or don’t want to use, or simply don’t know how to use the fundamental security protocols listed below:
1.) Always Use Strong Passwords: Use passwords with at least 8 characters and three different variables of at least one uppercase letter, one lower case letter, and one number or symbol.
Your Protections Need Strength (and Complexity)
For example: 1L0v3B@y! or J@m3$=Kool

Common and Simple Passwords Don’t Keep You Protected (more…)
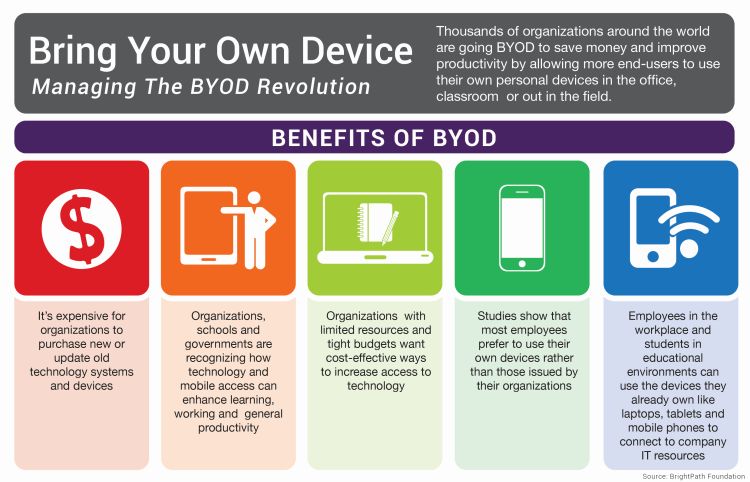
BYOD and Your Business Technology: Why BYOD Policies Are Key to Success
Bring Your Own Device: Right for Your Office IT?
Another day, another acronym…Things have changed over the years and while BYO (Bring Your Own) may have different meanings depending where you find yourself, the popularity and importance of Bring Your Own Device (BYOD) has continued to grow rapidly over the last few years.
Why Are Businesses Choosing BYOD?
Organizations and businesses throughout the Bay Area have taken note of the:
- Cost-Savings Opportunities
- Employees’ Preferences
- Streamlining Potential
- And the Benefits of Greater Flexibility
Associated with allowing employees to bring and use their own personal laptops and mobile devices at work.
BYOD and Your Business: Why BYOD Policies Are Key to Success
Bring Your Own Device: Right for Your Office IT?
When you first hear “BYO” mentioned, office technoligies may not be the first thing that springs to mind…
Things have changed in the workplace, and BYO (Bring Your Own) has taken on a new significance as the popularity and importance of Bring Your Own Device (BYOD) has continued to grow rapidly over the last few years.
Why Are Businesses Choosing BYOD?
Organizations and businesses throughout the Bay Area have taken note of BYOD’s:
- Cost-Savings Opportunities
- Incorporation of Employees’ Preferences
- Streamlining Potential
- And the Benefits of Greater Flexibility

How Ransomware Held Police Hostage
Megacode Malware Takes Hold Of Police Servers
As the ransomware problem heats up, even police servers aren’t safe!
Just a few weeks ago, Megacode cryptoware brought down four police offices and a sheriff’s department with a server attack and put sensitive personal and police data at risk. It’s no longer just private businesses who choose are affected by online ransom demands when it comes to ransomware, and even the police are starting to give in.
Businesses without the right IT support often get hit the hardest because they are: (more…)
5 Signs You Need Professional IT Support
It can be tempting to get by with a makeshift IT system. Third-party professionals will charge you for IT services, and if you’re just backing up to a couple of hard drives, why not let the savvy computer guy handle it? Then your whole office gets hit with a virus and the computer servers crash.
Top 15 Weakest Passwords Of 2015
Common Passwords, Common Problems

You lead a busy life, and it’s tricky enough having to remember all of your daily tasks and errands, let alone a new password for each and every account that you have.
How to Prepare for Windows Server 2003 End of Support
Coming Soon: Windows Server 2003 End of Support Date
It is almost time for Windows Server 2003 to shuffle off to that big network in the sky. The official End of Support date (EOS) for the operating system is July 14, 2015, after which it will no longer be actively supported by Microsoft. Everyone working in Bay Area IT services is currently scrambling to meet the demand caused by this changeover.
Is It a Big Deal?
Very much so. It’s vital that software is regularly monitored against emerging security threats, especially on an enterprise level where the stakes are so high. If your systems are not up-to-date, with the latest patches to repair the most recent exploits, then your entire network is vulnerable to hackers.
In 2013, Microsoft issued 37 critical updates for Windows Server 2003. That’s roughly one every ten days. After July 14, you’re on your own.Your “how to” blog post should teach the reader how to do something by breaking it down into a series of steps.
Begin your blog post by explaining what problem you are going to solve through your explanation and be sure to include any relevant keywords. Add in a personal story to establish your credibility on this topic. And make sure to end your blog post with a summary of what your reader will gain by following your lead.
Need some inspiration? Check out these “How-To” examples from the HubSpot blog:
IT Services Bay Area – Windows Server 2003 Going Out of Support
How to Prepare for Windows Server 2003 End of Support
It is almost time for Windows Server 2003 to shuffle off to that big network in the sky. The official End of Support date (EOS) for the operating system is July 14, 2015, after which point businesses will no longer be actively supported by Microsoft.
With the deadline rapidly approaching, businesses throughout San Francisco and the Bay Area are currently scrambling to find technical help as they look to update and transition their systems.

As a result, those of us working in Bay Area IT services have been hard at work to meet the demand caused by this changover as we work help improve our clients’ systems and properly educate our users as they take action.
7 Key Ways Professional IT Support Helps Improve Business Operations
![IT Solutions Provider Helpdesk Technicians at Work IT Solutions Provider Helpdesk Technicians at Work]() 7 Ways Professional IT Support Helps Your Business Flourish
7 Ways Professional IT Support Helps Your Business Flourish

Technology is the backbone of modern commerce, so strong technical support is vital to the success of any business. But with steadily increasing overhead costs and thinning profit margins, allocating precious funds to professional IT support often seems unnecessary. After all, when computer literacy is the norm, how does having professional IT support really benefit your business? As it turns out, there are quite a few answers.
Best Practices for Choosing a Cloud Provider in the Healthcare Sector
Best Practices for Choosing a Cloud Provider for an Elective Healthcare Practice
Although cloud computing is often regarded as a fairly new phenomenon, it has in fact been in use in one form or another since the late 1990s. However, its adoption by medical practices, including those in the elective healthcare sector, has been slow. By employing these best practices when choosing a cloud provider, you can make sure you’re getting an IT services firm that is the correct match for your organization.
Before You Hire IT Services Consultants, Ask These 5 Questions
5 Questions to Ask IT Consulting Firms
The days when only big business worked with IT consultants are long gone. Increasingly, small and medium size businesses (SMBs) understand that outsourcing some or all of their IT projects to consultants can help them focus on core business objectives, leverage expertise they don’t have in-house and cut overall costs.

5 Quick Checks: Is Your EHR Management HIPAA Compliant?
Five Steps: Is Your EHR Managment HIPAA Compliant?
The advent of electronic health records (EHR) have improved many aspects of health care: faster data sharing, better care coordination, increased patient participation, reduced errors and more.

But it also means that additional steps are necessary to ensure that your patients’ electronic protected health information (ePHI) is protected and that your practice is compliant with the Federal Health Insurance Portability and Accountability Act of 1996 (HIPPA).
Healthcare IT Support: How Working With an IT Service Provider Improves Patient Care
Healthcare IT: Free Up Your Practice to Focus on Patients
Top-rate medical practices are often let down by sub-par technical support, so it may be time to source the professional-caliber IT support services you need. However, that is sometimes easier said than done, and it’s important to know what support services your practice requires to protect your electronic health records (EHR) and the Electronic Personal Health Information (ePHI) you deal with each day.

As a physician, worrying about your healthcare IT services is not what you need to spend your day focusing on. Your job is to tend to your patients, and a company that offers a skilled support service enables you to do that. Support for your EMR/EHR software (such as NexTech) includes preventing inappropriate use, malware protection and training in best practices.
What is Rombertik? Latest Spyware Attacks Your Computer if Detected
What is Rombertik? Latest Malware Attack Triggers Destruction Tactics Upon Detection
Just yesterday, security experts discovered the latest strain of malware, nicknamed “Rombertik”, a specialized “wiper” malware smart enough to actively take precautions to help itself avoid detection.
But most importantly: If Rombertik even suspects, let alone confirms malware analysis, it will activate a number of “self-destruct” type functions on the host computer it has infected to stop you in your tracks. Here’s hoping you have updated backup solutions in place…
How To Implement Best Practices For Business IT
As a business owner, it can be overwhelming trying to stay up to date in the latest and greatest best practices for business technologies, but you know you need to keep your network, systems, and data safe in order to keep your office operations humming along.
Best Practices in Securing Mobile Healthcare Devices
Best Practices in Securing Mobile Healthcare Devices
Many physicians and practice support staff participate in bring your own device (BYOD) arrangements at work. Having a BYOD policy is both convenient for staff and cuts the cost of supplying staff with electronic hardware. However, without proper technology management BYOD can easily turn into a nightmare with regard to security, so follow these best practices to ensure your practice is safe.