Your IT Technician’s Top 7 Tips to Keep Your Business IT and Networks Safe
Want to Keep Your Network and Your Business Safe?
Here’s What Your Employee End Users Really Need to Know: Advice from Your IT Support Technician

One of the most common things that people forget when thinking about office technology and network management is actually one of the its important elements: the basic security and daily habits of end users.
While those of us who work in IT solutions can put as many locks on the gates as we can possibly think of, it does absolutely NOTHING, if the people who actually use the business network don’t use, or don’t want to use, or simply don’t know how to use the fundamental security protocols listed below:
1.) Always Use Strong Passwords: Use passwords with at least 8 characters and three different variables of at least one uppercase letter, one lower case letter, and one number or symbol.
Your Protections Need Strength (and Complexity)
For example: 1L0v3B@y! or J@m3$=Kool

Common and Simple Passwords Don’t Keep You Protected
More Specifically, full words, sequential numbers, etc. such as: “123ABC” “LetMeIn” or “Sunshine15” are easily guessed and far too weak to keep your business safe
Think of it this way, would you feel comfortable sending off this “strong” little lady to fight/ fighting off your bad guys?

Why Should You Bother? Current reports state it can take cybercriminals under 1 minute to hack through to your network when passwords consist only of letters without any variables.
2.) Change Your Password Often: The industry standard is to change your password every 90 days, but firms concerned with the security of their technology solutions may enforce expiration dates at the 30 day or 45 day mark.

Why Does It Matter? One common attack method the bad guys use is to find out your password and then continue to use it, or even publish it to others for their use, so you want to make sure that you change your passwords at a regular basis to avoid this sad fate.
3.) Never Use the Same Passwords Simultaneously on Multiple Accounts: Try to use a unique, different password for each of your main accounts and or logins. Don’t give cybercriminals the keys to your castle!

For example, create a single, unique password for your gmail account, another unique password for your bank, and a third one for your office IT logins.
Why Is It Worth My Time? One of the easiest ways for hackers to bypass all the security measures your business has invested to put in place is for them discover the password of something “innocent” or innocuous… Think of something like your Twitter account, which you may leave open on different devices or have a simplified password for.
From there, your attackers then use that password to try to get into your email, your banking accounts or other crucial accounts where the real damage can be done. If you use the same password across different accounts, you’ve suddenly given your attackers the keys to your kingdom and it’s suddenly a cakewalk for them to access ALL of your systems.
4.) Avoid Pop-Ups Like the Plague: If you see a pop up window always avoid clicking on anything related to it and call your IT solutions provider immediately.
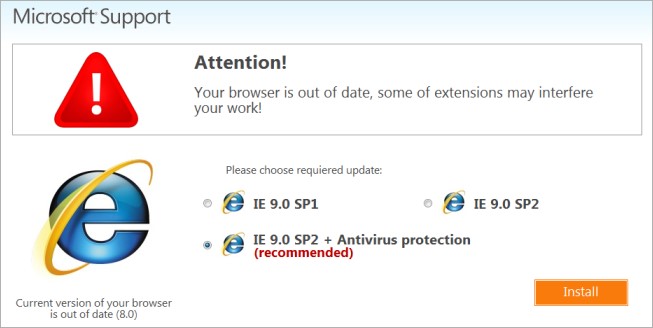
One of the most common and clever ways hackers use to get into your business systems is to masquerade and present themselves as a reliable, trusted, and often authoritative party such as a government agency or even as an anti-virus update for your system.
Please, keep in mind that NO reputable anti-virus system will ever create a pop-up prompt on your screen.
If you see this type of prompt, you should IMMEDIATELY close down your browser and power off your machine (without clicking on any links) and contact IT support.
Why so extreme? The latest Breach Investigations Report has shown that the median time it takes for an employee to open a phishing message, have it land on the company network and then compromise their business’ data is only one minute and 20 seconds. If you cannot close the browser do not click on anything, turn off your computer ASAP and contact your IT services provider.
5.) Do Not Save Passwords: Just as you wouldn’t hide a house key right under the front doormat, you shouldn’t leave your passwords saved.
When a website has a password requirement and your browser asks if you want to save your password avoid doing so, because this embeds the passwords onto your system’s hardware.

Why does it matter? When you save your passwords, if your system gets lost or stolen the thieves suddenly have access to all of your and your clients’ information.
Additionally, if you encounter any problems or have to reach out to your bay area IT services team for troubleshooting on your account, people who save their passwords usually proceed to forget those passwords. This means that whenever you request IT support, your support technicians will then have to request a new password for you.
While we are happy to help you navigate any password issues you may encounter, the reset process often leads to delays which can significantly inflate the time needed to complete your helpdesk service request and to resolve your problem.
6.) As a Rule of Thumb, NEVER, install anything yourself, EVER: One of the top ways cyberattacks succeed is through tricking employees and end users into actually installing a viruses or malicious software (malware)for the hackers; believe it or not, they get you to do their dirty work for them!

Really? But I Know Who This Is From: Even those applications that you know are from trusted sources can cause other problems further down the road if they are not installed properly. These issues pop up like weeds if there were any other kind of requirements or special configurations which may not have been installed properly or completed beforehand.
Pro-Tip: When you have the right IT support company on your side, you have the resources necessary to ensure sure your computers are configured and maintained properly. Keep things simple for yourself and use this to your advantage! (Plus, who doesn’t love coming back from lunch and finding that annoying task you were dreading fully taken care of for you?)
7.) Always Update Your Anti-Virus, and If Possible, Choose a Centrally Managed Anti-Virus: Viruses, malware and all other forms of cyberattacks are always changing, ever-evolving and improving every day.

I Already Have Anti-Virus, and Those Updates Are Annoying: Just because you have an anti-virus installed on your device does not mean that you are safe. With each new attack, both the good guys and the bad guys learn something new, and that’s exactly why it is absolutely crucial that you make sure you update your anti-virus on a regular basis.
I strongly advice that if at all possible, you work with your IT provider to find the right centrally managed anti-virus solution because this eliminates the risk of having an “oops” and “ut-oh, I forgot” moment spiral into a disaster.
With centrally managed anti-virus, your helpdesk team takes care of ensuring that updates are completed across your organization’s system on a dependable basis, and if an update fails for whatever reason, they know and can reach out to you to verify what’s going on. Without this built in-protection, it just becomes too easy to fall trap to waiting until “tomorrow.”
Comments are closed.
