Archive for the ‘Uncategorized’ Category
OCIE’s Focus on 2015 Cybersecurity Examination Initiatives
84% of Dropper File Malware Attacks Hit Healthcare – Here’s What to Do
File Dropper Malware Targets Healthcare
As organizations worldwide work to increase data protection, cyber criminals are continuing to launch increased attacks against businesses. One of the greatest risks facing modern organizations are “dropper files.” These common risks are a form of advanced malware that gain entry into business systems through vulnerabilities to gather protected information to sell.

Stegoloader Malware Targeting Healthcare Providers Throughout North America — Is your Practice Safe?
Stegoloader Malware Targeting Healthcare Providers Throughout North America—Is Your Practice Safe?
There have been number of reports about how stegoloader malware is being used to target healthcare providers across North America, which is cause for concern because the malware is sophisticated enough to go undetected. To avoid being targeted, partner up with experienced IT security experts who have the skills to detect this complex malware. Read on if you live in the San Francisco Bay area to find out how we can help your organization.
When It Comes to Patch Management, Zero Day Can Be the Longest Day
Zero-Day, the Longest Day?
Ever since childhood, you learn that things go “Boom!” when you count down to zero…
Sometimes that’s a good thing: The engines ignite and a rocket lifts off
Sometimes that’s a bad thing: A bomb detonates
The question for software development and IT support teams is what does zero-day mean in terms of impact on end-users and what, if anything, they can and should do about it. (more…)
‘Backoff’ Malware Steals Directly From POS Systems
‘Backoff’ Malware Steals Directly From POS Systems
Whenever new of the latest data breach hits the airwaves, chances are, it’s already too late. Why? As stories gain coverage, consumer awareness rises and preventative measures start being implemented, which is exactly why cybercriminals are constantly upping the ante to stay ahead of the curve.
With that in mind, every day new malware threats emerge, developed with the intent of infiltrating and infecting computers to enable hackers to steal valuable private information from businesses. The “treasure” malicious hackers are after can vary, yet personal data and payment card information such as credit card numbers are top targets.

Point-of-Sale (POS) outlets (which have become standard in small business environments for payment card processing) connect to online systems and present an extremely enticing target for cybercriminals using malware for their exploits. One of the most effective exploits in recent years has proven to be the Backoff group of malware programs, which specialize in spreading to POS software running on Windows systems.
IT Services Security Alert: Cryptowall Ransomware
IT Services Security Alert: CryptoWall Ransomware
CryptoWall: Holding Your Data for Ransom
On June 23, 2015, the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) issued a warning about CryptoWall, a ransomware threat that can endanger your business and cost you money. Ransomware is malicious software that infects your computer and encrypts your data, locking you out of your files. Your information is held for “ransom,” a request for money usually between $200 and $10,000. Failure to pay by a certain deadline results in your data being destroyed.
The FBI has received more than 992 complaints of CryptoWall incidents since April 2014. They estimate the cost of these incidents totals more than $18 million. This cost not only includes the ransom itself, but recovery expenses and potential legal fees.

Understanding the SEC OCIE’s Cybersecurity Examination Initiative
OCIE Focusing In On Cybersecurity Exam Initiatives:
The SEC’s top 6 priorities, and how working with an IT services provider ensures your firm is fully prepared
With the Securites and Exchange Comission’s Office of Compliance release of cybersecurity summary reports and exam intiatives, many financial services firms are being forced to reprioritize cybersecurity in preparation for potential SEC exams.
Without the right technology services partner in place, the initiatives are daunting, and getting started can feel overwhelming. Just look at the numbers.
In its summary report of those examinations, released in February of 2015, the OCIE stated that of those organizations it examined, 88 percent of the broker-dealers and 74 percent of the RIAs had experienced a cybersecurity incident recently.
This year, OCIE followed up with the Examination Priorities for 2016, where it was confirmed that in 2016 emphasis will be placed on testing how firms have implemented the procedures and controls initially examined in 2015.
The OCIE further announced that it planned to focus on cybersecurity compliance in its 2015 Examination Priorities. Last September, the office released the 2015 Risk Alert providing compliance guidance for industry entities that might be subject to examination.
5 Ways Managed IT Services for Insurance Companies Help Reduce Your Operation Expenses
Top 5 Ways for Insurance Firms to Reduce Operational Costs by Using Managed IT Services
Visual Based Post [Blogging Blueprint]
INTRODUCTION:
An image post uses a visual element as the centerpiece of your post, such as a SlideShare presentation, infographic, comic, or high-resolution images.
Use your introduction to provide a caption for your image(s). Why is it valuable? What’s the point? Image posts don’t require a lot of text, so choose your words wisely.
Here are some examples of how we use Visual blog posts here at HubSpot:
Test
INTRODUCTION:
An image post uses a visual element as the centerpiece of your post, such as a SlideShare presentation, infographic, comic, or high-resolution images.
Use your introduction to provide a caption for your image(s). Why is it valuable? What’s the point? Image posts don’t require a lot of text, so choose your words wisely.
Here are some examples of how we use Visual blog posts here at HubSpot:
How to Improve Patient Care Using Healthcare Technology Strategically (Clone)
Dual Customer Focus – Healthcare IT Best Practices That Benefit Patients and Employees Alike
While many organizations place the heaviest emphasis on customer experience, the focus of healthcare information technology must seek to serve the needs of two different bases: both employees (your internal customers) and patients (your external customers).
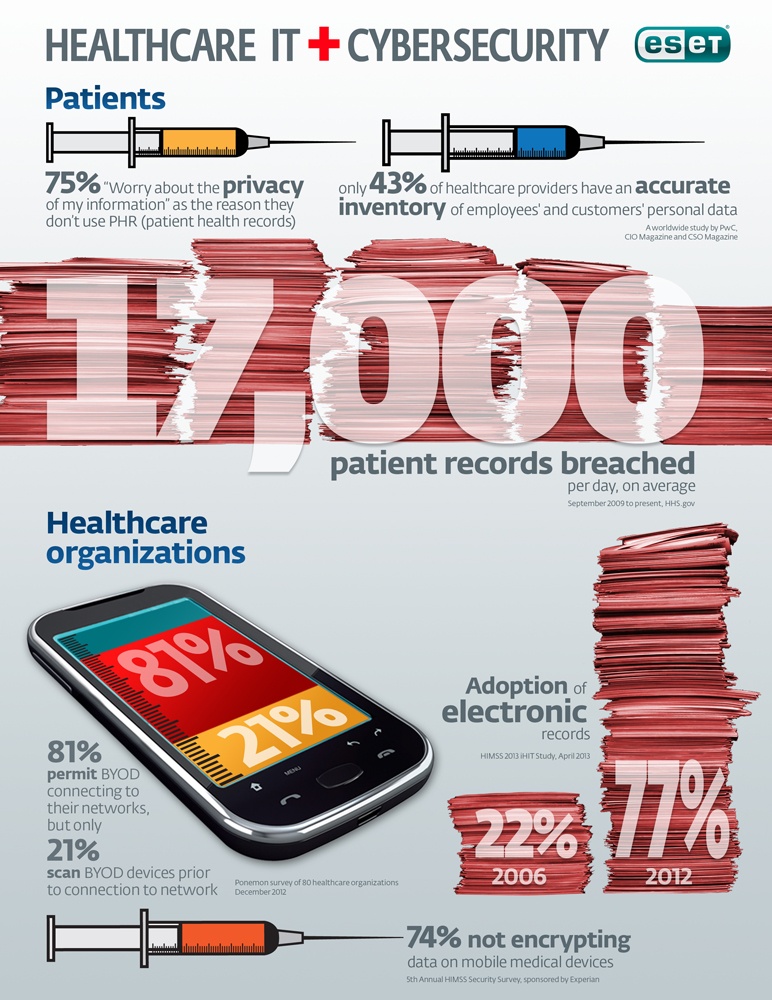
If you’re looking to please both crowds, keep in mind the following healthcare IT principles and practices.
How To Add Apple Computers To Your Domain
A common challenge system administrators face is having to choose if they will allow Apple-based systems into their computer networks. While there are many pros and cons to weigh, one easy way of working around this challenge is to add a Mac OS X operating systems to your domain.
