Latest News and Resources
What Is IT Service Management: Key Concepts and Benefits
IT Service Management (ITSM) is a strategic approach to designing, delivering, managing, and improving the way businesses use information technology.…
Read MoreWhat Is Cloud Computing: A Comprehensive Guide
Cloud computing has transformed how businesses and individuals access and manage data worldwide. It is the on-demand availability of computing…
Read MoreData Loss Prevention: Essential Strategies for Modern Enterprises
We all fear failure. And for those of us working in technical IT support, the two words which immediately strike fear into even the hardiest of souls are – Failed Array
To explain what a failed array is you first need to know a couple of things about computer servers.
And to get us started, let’s answer:
What Is An Array?
An array is a series of hard drives that can be combined in multiple ways to appear as a single large drive. Unlike most desktops, computer server systems often have two or more hard drives attached to them in what are then called redundant arrays, or more commonly:
RAID (Redundant Array of Independent Disks)

Now RAID started out as “Redundant Array of Inexpensive Disks” at a time when hard drives:
- Were more expensive
- Had less data storage capacity
- Lacked failover protection/ fault tolerance
Because of these factors, RAID systems were first created using multiple inexpensive hard drives into single, more powerful, and faster volumes. Even more importantly, the design of RAID systems enabled redundancy as a protection against single points of failure.
For example, if you have two 1 Terabyte (Tb) hard drives in what is called a Raid 0, those two individual drives will appear as a single 2Tb drive.
1TB + 1TB = 2TB.
While the ways in which you can assemble a RAID system vary depending on what your business needs are and how much your business has budgeted, outside of RAID 0 (single volume), the end results are nearly always seeking to serve the same basic purpose.
Which is to serve as a nice large drive that your business network can see and use to fulfill your data redundancy and performance needs.
That is of course, until something goes wrong.
It should be noted- Just as an array can be configured in countless different ways, there are also many different ways in which they can fail.
The most common problems usually involve a hard drive failure of some sort, which is why any reliable IT provider will always push you to incorporate data redundancy into your computer networks and technologies.
Whenever a hard drive failure does happen, having a local Bay Area IT services team ready to provide you the technical support your desperately need is key.
Not only will they be able to hit the ground running (by being familiar with your business IT setup) but it is their job to stand between you and the dreaded monster called… DATA LOSS (cue appropriately ominous music).

Data Backups: The first and most important step of file maintenance
The very first way in which we handle IT work to help maintain all of your files is through backups. If you ever work with an experienced IT professional, chances are you’ll often hear the battle cry, backup, backup, BACKUP!!!
Data backups can be accomplished through a number of different methods, but the first step is dictated by the demands of your business needs, followed by the relative size of the budget that your company has available.
Depending on which data backup options are available, the means of backing up can be as simple as copying data from one hard drive to another (often known as data replication) all the way up to advanced virtualization and the replication of your data to multiple locations (known as data redundancy and replication).
So what happens after you realize that one of your files is corrupt?
With the right backup and data recovery solutions in place, the emergency which previously would have spelled disaster and mayhem is suddenly tamed when you can just call your IT services provider.
Having data backups in place allows you to avoid the irreparable damage of a data loss event. With a pre-planned data recovery solution, you know that your IT support team has reliable access to your most recent backups and can restore your data to where you need it to be.

How Does An Array Fail? Why Does An Array Fail?
Now after we have retrieved the files that you need, it’s on to step two: Finding out why your array failed.
As I stated previously the most common and dastardly ways that an array can fail is through simple hard drive failure. Most server hard drives spin at over 10,000 RPMs a figure most sports cars would envy. When they spin so fast, any bump or collision with the server can cause over 250 of G-force damage.
Context: If you or I were to suddenly encounter 250 G’s we would instantly be turned into pudding. Now if your business is lucky (e.g. well prepared and well-funded), hard drive failure can sometimes be as simple a matter as changing out the drives which are indicated by the red lights on the front of your server.
Yet occasionally, it isn’t so easy.

I still remember one instance where I was working with a client who had a server that didn’t have the normal, nice, clear and easy indicator lights to tell us which drive was failing.
After polling the backups and getting the data in a safe state, we had to go through and manually determine which drive was failing.
The problem with this is, if you pull the wrong drive, you can destroy the array entirely. Basically, this turns a relatively simple job of changing out a hard drive, into a task more akin to trying to decide which wire to cut before the bomb goes off…

So the first thing that I did (after creating yet another tertiary backup) was to go into the bios of the computer and see if there were any clues there.
After that failed, we were able to run a utility built into the server which scanned the array and told me which drive wasn’t responding properly.
Using this new information, I was able to carefully trace each connection on the server to each drive and with a magnifying glass, then look at the labels on the motherboard.
After all of those steps and extra precautions, I finally found the path which led me to the correct drive.

Now once the failed drive was identified and located, it was simply a matter of replacing the drive and rebuilding the array (And then of course, creating yet ANOTHER backup.)
While we were able to fix all of the problems involved and get the client under way with the minimum level of downtime possible, the true hero of this story still is and will always be the backups that we had implemented.
Without those data backups, each and every step we took, including merely scanning the hard drive, would have run the risk of permanently destroying the array and losing years of work.
Long story short, we’re back to the battle cry: Backup, Backup, BACKUP!!!
Find yourself wondering if your company’s your data backups and data recovery options are enough to keep you safe?
Feel free to Contact Us with any questions you may have about RAID, backups or redundancy options at 925.459.8500!
Read MoreHow To Stop Malware Attacks: Essential Prevention Strategies
In my last blog post, we discussed the basics of malware, reviewed the conditions malware requires and also introduced a few of the most common forms that it takes. Now that you’ve got a basic understanding of “what” it is, it’s time this IT support technician taught you how to avoid malware attacks before they can take hold of your systems.
Here are 6 simple yet crucial steps which will help prevent “disaster” situations from happening to your organization. As we continue, I’ll be providing you additional advice and malware protection tips from my years of experience working in the field of IT support services throughout the Bay Area.
1.) Have Two User Accounts

Log in to your PC as a standard user, not as an Administrator.
This means you should have two user accounts: one non-privileged user account, and one privileged user account. That way, anything that requires “elevated” access (non-standard privileges) will need to explicitly ask for your permission.
In order to maintain security, your administrator account should have a different password from your main account.
2.) Read Pop-Up Messages That Appear On Your System
This is an important part of avoiding malware problems in the first place. Do NOT just click “OK” to everything.
- Try not to get into the habit of hitting “OK” to everything: Web sites can create pop-up windows that masquerade as system warnings or update reminders.
- Without reading every pop-up, you could unknowingly enable a malware attack.
- If you are in doubt about a particular pop-up message that appears on your screen, try dragging it to the right or left of the web browser window.
If you can’t drag it outside of the web browser, it is not a system message.
Use the [X] button on the window to close it, and you may want to close your web browser as well (and avoid that web page in future!).
3.) Double-Check Application Updates

When you are prompted to install updates for well-known applications, make sure that it is something you actually have installed on your system. If you are in doubt about an update, close the window (using the [X] button) and visit the web site of the application vendor to check for the update.
4.) Use Automatic Updates For Existing Applications
If there is a way to automatically apply updates for an application you want, need, and trust, use that update method. It is better to allow trusted programs to update themselves automatically.
Example: If you have told Flash Player to “Always Update” without prompting you, and later you suddenly get a prompt to update Flash Player, you can be pretty sure it is a malware attack of some sort.
5.) Let Windows Update Download And Install Critical Updates.
Try to set a schedule for when you download full system updates. This will ensure that the download goes smoothly, and does not crash your computer. The ideal time is when your computer will be on, and your network connection will not be overloaded.
6.) Delete Questionable Emails
The simple rule for e-mail is when in doubt, throw it OUT.

- Be highly skeptical of any attachment or link, even from people you know, unless it is something you know in advance is coming.
- It doesn’t hurt to call or text or e-mail someone to make sure. When an email seems out of place think of what Professor Moody always reminds Harry Potter: “Constant Vigilance!”
- Be especially wary of email messages purporting to be from your bank, from software vendors, or claiming to be fax messages.
- Example: If PayPal, Amazon or your bank sends you a link, it doesn’t hurt to simply open up the web site separately yourself, instead of clicking a link sent via e-mail.
- There are now many different ways to disguise a link – even experts can be fooled.
While these malware protection methods may take a few extra seconds, in the long-run they will help you avoid hours of downtime on clean-up and data recovery. If you are interested in a more advanced form of data security, give Bay Computing a call at 925.459.8500 to ask about our IT security solutions!
Read MoreTop IT Tips to Keep Your Business Safe
Want to Keep Your Network and Your Business Safe?
Here’s What Your Employee End Users Really Need to Know: Advice from Your IT Support Technician

One of the most common things that people forget when thinking about office technology and network management is actually one of the its important elements: the basic security and daily habits of end users.
While those of us who work in IT solutions can put as many locks on the gates as we can possibly think of, it does absolutely NOTHING, if the people who actually use the business network don’t use, or don’t want to use, or simply don’t know how to use the fundamental security protocols listed below:
1.) Always Use Strong Passwords: Use passwords with at least 8 characters and three different variables of at least one uppercase letter, one lower case letter, and one number or symbol.
Your Protections Need Strength (and Complexity)
For example: 1L0v3B@y! or J@m3$=Kool

Common and Simple Passwords Don’t Keep You Protected
More Specifically, full words, sequential numbers, etc. such as: “123ABC” “LetMeIn” or “Sunshine15” are easily guessed and far too weak to keep your business safe
Think of it this way, would you feel comfortable sending off this “strong” little lady to fight/ fighting off your bad guys?

Why Should You Bother? Current reports state it can take cybercriminals under 1 minute to hack through to your network when passwords consist only of letters without any variables.
2.) Change Your Password Often: The industry standard is to change your password every 90 days, but firms concerned with the security of their technology solutions may enforce expiration dates at the 30 day or 45 day mark.

Why Does It Matter? One common attack method the bad guys use is to find out your password and then continue to use it, or even publish it to others for their use, so you want to make sure that you change your passwords at a regular basis to avoid this sad fate.
3.) Never Use the Same Passwords Simultaneously on Multiple Accounts: Try to use a unique, different password for each of your main accounts and or logins. Don’t give cybercriminals the keys to your castle!

For example, create a single, unique password for your gmail account, another unique password for your bank, and a third one for your office IT logins.
Why Is It Worth My Time? One of the easiest ways for hackers to bypass all the security measures your business has invested to put in place is for them discover the password of something “innocent” or innocuous… Think of something like your Twitter account, which you may leave open on different devices or have a simplified password for.
From there, your attackers then use that password to try to get into your email, your banking accounts or other crucial accounts where the real damage can be done. If you use the same password across different accounts, you’ve suddenly given your attackers the keys to your kingdom and it’s suddenly a cakewalk for them to access ALL of your systems.
4.) Avoid Pop-Ups Like the Plague: If you see a pop up window always avoid clicking on anything related to it and call your IT solutions provider immediately.
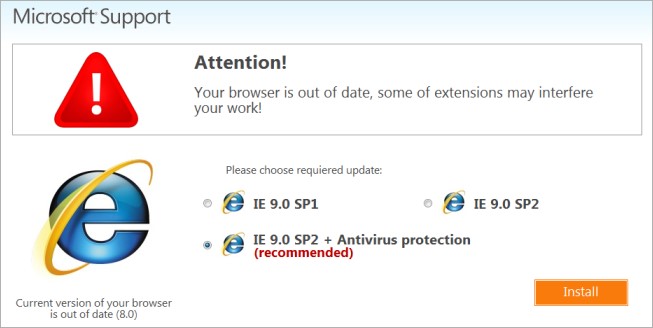
One of the most common and clever ways hackers use to get into your business systems is to masquerade and present themselves as a reliable, trusted, and often authoritative party such as a government agency or even as an anti-virus update for your system.
Please, keep in mind that NO reputable anti-virus system will ever create a pop-up prompt on your screen.
If you see this type of prompt, you should IMMEDIATELY close down your browser and power off your machine (without clicking on any links) and contact IT support.
Why so extreme? The latest Breach Investigations Report has shown that the median time it takes for an employee to open a phishing message, have it land on the company network and then compromise their business’ data is only one minute and 20 seconds. If you cannot close the browser do not click on anything, turn off your computer ASAP and contact your IT services provider.
5.) Do Not Save Passwords: Just as you wouldn’t hide a house key right under the front doormat, you shouldn’t leave your passwords saved.
When a website has a password requirement and your browser asks if you want to save your password avoid doing so, because this embeds the passwords onto your system’s hardware.

Why does it matter? When you save your passwords, if your system gets lost or stolen the thieves suddenly have access to all of your and your clients’ information.
Additionally, if you encounter any problems or have to reach out to your bay area IT services team for troubleshooting on your account, people who save their passwords usually proceed to forget those passwords. This means that whenever you request IT support, your support technicians will then have to request a new password for you.
While we are happy to help you navigate any password issues you may encounter, the reset process often leads to delays which can significantly inflate the time needed to complete your helpdesk service request and to resolve your problem.
6.) As a Rule of Thumb, NEVER, install anything yourself, EVER: One of the top ways cyberattacks succeed is through tricking employees and end users into actually installing a viruses or malicious software (malware)for the hackers; believe it or not, they get you to do their dirty work for them!

Really? But I Know Who This Is From: Even those applications that you know are from trusted sources can cause other problems further down the road if they are not installed properly. These issues pop up like weeds if there were any other kind of requirements or special configurations which may not have been installed properly or completed beforehand.
Pro-Tip: When you have the right IT support company on your side, you have the resources necessary to ensure sure your computers are configured and maintained properly. Keep things simple for yourself and use this to your advantage! (Plus, who doesn’t love coming back from lunch and finding that annoying task you were dreading fully taken care of for you?)
7.) Always Update Your Anti-Virus, and If Possible, Choose a Centrally Managed Anti-Virus: Viruses, malware and all other forms of cyberattacks are always changing, ever-evolving and improving every day.

I Already Have Anti-Virus, and Those Updates Are Annoying: Just because you have an anti-virus installed on your device does not mean that you are safe. With each new attack, both the good guys and the bad guys learn something new, and that’s exactly why it is absolutely crucial that you make sure you update your anti-virus on a regular basis.
I strongly advice that if at all possible, you work with your IT provider to find the right centrally managed anti-virus solution because this eliminates the risk of having an “oops” and “ut-oh, I forgot” moment spiral into a disaster.
With centrally managed anti-virus, your helpdesk team takes care of ensuring that updates are completed across your organization’s system on a dependable basis, and if an update fails for whatever reason, they know and can reach out to you to verify what’s going on. Without this built in-protection, it just becomes too easy to fall trap to waiting until “tomorrow.”
Read More
BYOD and Your Business Technology: Why BYOD Policies Are Key to Success
Bring Your Own Device: Right for Your Office IT?
Another day, another acronym…Things have changed over the years and while BYO (Bring Your Own) may have different meanings depending where you find yourself, the popularity and importance of Bring Your Own Device (BYOD) has continued to grow rapidly over the last few years.
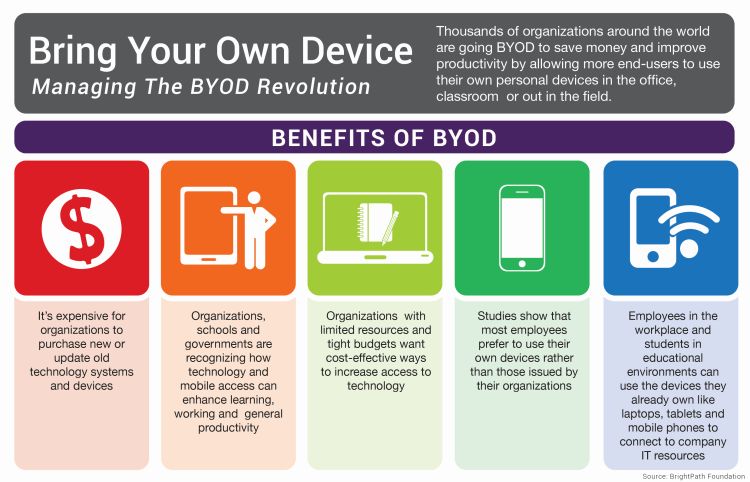
Why Are Businesses Choosing BYOD?
Organizations and businesses throughout the Bay Area have taken note of the:
- Cost-Savings Opportunities
- Employees’ Preferences
- Streamlining Potential
- And the Benefits of Greater Flexibility
Associated with allowing employees to bring and use their own personal laptops and mobile devices at work.
Before you introduce BYOD into your workplace, it is crucial for your organization to identify, recognize and address the potential impacts of providing full business access on employee-owned devices to your files, your data security, your business operations and even your clients.
How to get started: Proactively implement policies and procedures to govern their use from the very beginning.
Think of it this way, you want the tracks in place, headed in the right direction before you start running the train.
Why Do We Need An Official BYOD Policy?
It’s hard to remember, but those daily details such as not saving work-related login credentials may seem obvious to one user, yet could easily appear completely benign to the next.
Without the context provided by employer education or at the very minimum, a BYOD Policy (and possibly Mobile Device Management, or MDM Policy), what at first seems like a simple, seamless transition can accidentally spin out of control into a company-wide data breach or worse.

But IT Security Is Simple! It’s Common Sense, Right?
What starts out as a small concern can easily go undetected and spiral out of control when well-intentioned yet uninformed users are behind the wheel. Rh
The effects of simple “ut oh” mistakes from well-intentioned yet uninformed users are exponentially magnified as soon as devices with unstandardized configurations, a hodgepodge of unapproved softwares and unknown applications gain access to your computer network, services or advanced IT management solutions.
When your configurations and installations are completed on-the-go, whenever a user sees fit, it’s common for key security safeguards such as antivirus installations and regular updates to fall through the cracks undetected.
While this may not always present a problem on a day-to-day business, but as soon as an attack slips through, you’re suddenly finding yourself trying to put out a five-alarm fire with a garden hose…
When it comes to BYOD, your employees have the capacity to make decisions which can have far-reaching (and sometimes unintended) consequences.
For example, if one of your veteran employees just purchased a brand-new MacBook Pro…and for convenience…and because they like it more… they started bringing that laptop to work.

Now that same employee has been thoroughly enjoying having all of their work files, credentials, and possibly even sensitive client information that they need to complete their job on their go-to device…
Fast forward, and now it’s Monday morning.
- That same employee is frantically telling you about how they were tying up some loose ends over the weekend…
- They were just a few steps away from their table, ordering another coffee, when a thief ran by, scooped up their beautiful new MacBook, and ran
- They can’t believe it, happened right in the middle of working- fully logged in, device unlocked, and with a report containing secured client information open.
Soon it starts to sink in… All of the project details, sensitive client information and even the small quick-reference workbook filled with your company’s account logins have been compromised.
But My Employees Would Never Try to Harm Us!
Clearly not, you trust your team, and you’re worked hard to find the right people for your Bay Area business. When BYOD fails, it’s usually obvious there was no malicious intent, just like scenario above. (And in the rare instances where malicious intent is at hand, a conversation on “social engineering” and “insider attacks” would be necessary.)
Yet it’s simple, unplanned events such as these which can leave you fighting to protect the precious intangibles of your business such as client trust and confidence in your capabilies as well as their security.
This es exactly why BYOD Policies are crucial. When employee owned devices are not fully discussed, their access levels examined and their rights agreed upon, the “grey” area becomes a danger-zone. .
Throughout your years working in Bay Area businesses and organizations, you’ve seen time and again know that the success of any process, procedure or campaign boils down to buy-in.
No matter how detailed, well thought out and comprehensive a policy document is, if users don’t understand or don’t care or know it won’t be enforced, a BYOD policy becomes useless.
How Do I Set My Business Up For BYOD Success?
When you have expert resources, make sure you use them!
You know the ins and outs of your organization’s operations, but when it comes to the details of your business network and advanced technology solutions, make sure you collaborate with your IT services provider to construct practical, easy-to-understand, and simple-to-enforce policies.
By working together you can make sure that:
- Proper IT security measures are being put in place
- They are crafted to be as user-friendly as possible from an end-user’s perspective
When your Bring Your Own Device guidelines and policies are easily understood, well-explained, and consistently enforced, you can rest easier knowing that you have set your users and your business technology solutions up for success.
If you’re considering implementing BYOD in your workplace- Don’t wait, get started on building a strong foundation for your business IT today!
Read More
BYOD and Your Business: Why BYOD Policies Are Key to Success
Bring Your Own Device: Right for Your Office IT?
When you first hear “BYO” mentioned, office technoligies may not be the first thing that springs to mind…
Things have changed in the workplace, and BYO (Bring Your Own) has taken on a new significance as the popularity and importance of Bring Your Own Device (BYOD) has continued to grow rapidly over the last few years.
Why Are Businesses Choosing BYOD?
Organizations and businesses throughout the Bay Area have taken note of BYOD’s:
- Cost-Savings Opportunities
- Incorporation of Employees’ Preferences
- Streamlining Potential
- And the Benefits of Greater Flexibility

Before you introduce BYOD into your workplace, it is crucial for your organization to identify, recognize and address the potential impacts of providing full business access on employee-owned devices.
More specifically, this is the time to consider how providing access to your files, increasing the scope of your data security responsibilities,and how introducing unintentional side effects could affect your business, your operations and even your clients’ experiences.
How to get started: Proactively implement policies and procedures to govern their use from the very beginning.
Think of it this way, you want the tracks in place, headed in the right direction before you start running the train.
Why Do We Need An Official BYOD Policy?
It’s hard to remember, but small details such as not saving work login credentials may seem obvious to one user, yet could easily appear completely harmless to the next.
Without the context provided by employer education or at the very minimum, a BYOD Policy (and possibly Mobile Device Management, or MDM Policy), what at first seems like a simple, seamless transition can accidentally spin out of control into a company-wide data breach or worse.

But IT Security Is Simple! It’s Common Sense, Right?
What starts out as a small concern can easily go undetected and spiral out of control when well-intentioned yet uninformed users are behind the wheel.
It’s Hip to Be Square: While standard company issued laptops or PCs may scream Office IT and lack the “sexiness” of your personal top-choice device, there’s a reason corporate devices exist.
The effects of simple “ut oh” mistakes from well-intentioned yet uninformed users are exponentially magnified as soon as devices with unstandardized configurations, a hodgepodge of unapproved softwares and unknown applications gain access to your computer network, services or advanced IT management solutions.
Why Standards Matter

When your configurations and installations are completed on-the-go, whenever a user sees fit, it’s common for key security safeguards such as antivirus installations and regular updates to fall through the cracks undetected.
You may get lucky and manage to skirt problems in your day-to-day business, but as soon as an attack slips through, you’re suddenly trying to put out a five-alarm fire with a garden hose…
When it comes to BYOD, your employees have the capacity to make decisions which can have far-reaching (and sometimes unintended) consequences.
For example, if one of your veteran employees just purchased a brand-new MacBook Pro…and for convenience…and because they like it more… they started bringing that laptop to work.

That same employee has been thoroughly enjoying having all of their work files, credentials, and possibly even sensitive client information that they need to complete their job…
Fast forward, and now it’s Monday morning.
- That same employee is frantically telling you about how they were tying up some loose ends over the weekend…
- They were just a few steps away from their table, ordering another coffee, when a thief ran by, scooped up their beautiful new MacBook, and ran
- They can’t believe it, happened right in the middle of working- fully logged in, device unlocked, and with a report containing secured client information open.
Soon it starts to sink in… All of the project details, sensitive client information and even the small quick-reference workbook filled with your company’s account logins have been compromised.
But My Employees Would Never Try to Harm Us!
Clearly not, you trust your team, and you’re worked hard to find the right people for your Bay Area business.
When BYOD fails, it’s usually obvious there was no malicious intent, just like scenario above. (And in the rare instances where malicious intent is at hand, a conversation on “social engineering” and “insider attacks” would be necessary.)

Yet it’s simple, unplanned events such as these which can leave you fighting to protect the precious intangibles of your business such as client trust and confidence in your capabilies as well as their security.
This is exactly why BYOD Policies are crucial. When employee owned devices are not fully discussed, their access levels examined and their rights agreed upon, the “grey” area becomes a danger-zone. .
No matter how detailed, well thought out and comprehensive a policy document is, if users don’t understand or don’t care or know it won’t be enforced, a BYOD policy becomes useless.
How Do I Set My Business Up For BYOD Success?
When you have expert resources, make sure you use them!
You know the ins and outs of your organization’s operations, but when it comes to the details of your business network and advanced technology solutions, make sure you collaborate with your IT services provider to construct practical, easy-to-understand, and simple-to-enforce policies.
By working together you can make sure that:
- Proper IT security measures are being put in place
- They are crafted to be as user-friendly as possible from an end-user’s perspective
When your Bring Your Own Device guidelines and policies are easily understood, well-explained, and consistently enforced, you can rest easier knowing that you have set your users and your business technology solutions up for success.
If you’re considering implementing BYOD in your workplace- Don’t wait, get started building a strong foundation for your business IT today!
Read More
Ransomware Attacks on Police: Cybersecurity Threats
Megacode Malware Takes Hold Of Police Servers
As the ransomware problem heats up, even police servers aren’t safe!
Just a few weeks ago, Megacode cryptoware brought down four police offices and a sheriff’s department with a server attack and put sensitive personal and police data at risk. It’s no longer just private businesses who choose are affected by online ransom demands when it comes to ransomware, and even the police are starting to give in.
Businesses without the right IT support often get hit the hardest because they are:
1.) Missing the Right Guidance: Navigating in the Dark
Without regular technology advice or the manpower to implement the right IT security solutions and safeguards- It’s no coincidence that the police departments hit by the Megacode malware attacks were small to midsize offices.

Similarly, if your organization has been scraping by with ad-hoc technology and doesn’t have regular IT support and guidance, many task items and issues can easily fall through the cracks.
Your company teams focus in on keeping clients happy and getting their best work done on time. So when it comes down to choosing between helping a distressed customer or going through an antivirus update, chances are those small but critical details easily get pushed aide.
Decision Paralysis: Too Many Choices, Too Much Technology
Finding the right security solutions to suit your business needs can be extremely overwhelming when you are faced head-on with the endless variety of options on the market. Without a trusted IT firm to provide guidance, many organizations find themselves putting off the implementation of security solutions when it can “wait until tomorrow.”
Throw in all of the tasks necessary to maintain your office technologies, and it’s easy to see why many cybercriminals are increasingly targeting local businesses throughout the Bay Area.
Without the help of the right outsourced IT team, the police departments quickly found themselves struggling to fight back against Megacode attacking their networks and holding their servers hostage.
2.) Don’t Forget to Lock Up! Unaware Users Invite Attacks
Your users strive to help your business grow, and as they stay focused on your success, they may unknowingly be enabling the very cybercriminals who are constantly fighting to take your IT systems down!
Having the appropriate policies in place (for example, implementing BYOD policies), working with a regular computer and IT support provider and making tech help training materials from your help desk readily available can all help your organization cut back on user error related vulnerabilities and greatly decease the number of strategic mistakes made in daily operations.
When it comes to your business and office technology, think of things this way:
“It’s like a jail- it’s very safe and secure, but that can mean nothing if you leave the door unlocked”– Sheriff Brackett, victim of Megacode
3.) Spotting An Attack: Where There’s Smoke, There’s Fire
Users Need to Know How to Recognize When Something’s Wrong: It’s the only way to stop attacks
Ask your IT firm to provide you with the training materials and quick-reference information necessary to make sure your users know how to recognize malware attacks.
This is essential to keeping attacks from spreading
As soon as any device on your network has been infected it is absolutely crucial that your employees and management team be able to recognize
As Soon As They Happen –> Which enables faster response times and gives IT support teams the chance to minimize/ stop the damage from getting worse
4.) Data Recovery: Bulletproofing Your Business Data
Without data recovery options, organizations such as the Lincoln County Sheriff’s Office are faced with the touogh choice of having to either pay up or start over from scratch. Don’t let this be you!
Your people are there to focus in on what an antivirus goes out of
Without proper IT support, many businesses…
Read More5 Signs You Need Professional IT Support
It can be tempting to get by with a makeshift IT system. Third-party professionals will charge you for IT services, and if you’re just backing up to a couple of hard drives, why not let the savvy computer guy handle it? Then your whole office gets hit with a virus and the computer servers crash.
IT support is a lot like health insurance. It seems like you’re paying for nothing until disaster strikes. And in the long run, you end up using it a lot more than you think. Here are 5 surefire signs you need to put aside the pride and invest in professional Bay Area IT support:
1) Your IT Support Guy Already Works In The Office

Lots of small businesses handle IT support “in-house” by having their most computer savvy employee help them with computer issues. The problem is, there’s a difference between general knowledge of computers, and the ability to handle complex IT issues that relate to data security and cloud storage. If your resident computer guy seems over his head, he probably is. Don’t make the problem worse with a trial and error approach, contact an IT services provider to see about regular IT support.
2) You’re Paying For Advice (Not Help)

Many IT consultants make good money by giving self-serving advice. They will answer the phone, listen to your problems, and give you a sage-sounding solution to “try out”. And if that fails, then you have to call them back and get some more advice. The problem with this approach is that there is no understanding of the underlying condition that is causing recurring problems. A legitimate IT services provider can help you devise a system that prevents you from having to ask for advice…or solve the problem yourself.
3) You Keep Getting Viruses

This one is pretty self-explanatory. If you keep getting computer viruses or system malfunctions, it is probably time to call for professional IT support. The money you spend on a services provider will be nothing compared to the time and lost productivity of having your computers go down. Especially if important data is being lost in the process, or confidential client information is breached (opening you up to legal liability).
4) You’ve Maxed Out Your Data Storage Capacity
If your current data storage system is about to experience a Catch 22, you should seek out a Bay Area IT services provider to guide you through this critical transition. Potentially disastrous problems could include anything from an issue with filing nomenclature (computer filing applications may not recognize Patient 10,000 as a logical extension of Patient 9999) or a lack of data capacity that requires you to juggle important files between multiple hard drives. However you choose to solve an impending data storage problem, you will be better off with an Office IT specialist there to advise you.
5) You Don’t Know What Things Are

There is now a trend for small business owners (even from older generations) to employ the most advanced technology possible. They want to have a live Skype button on their website instead of a phone number. They want to share files via DropBox instead of emailing them. They want Blu-ray enabled PowerPoint presentations. And on and on.
Whatever the trend, many business owners find themselves regularly searching for advice on how to integrate new software or technology on the fly. Who wants that hassle? Investing in professional IT support means you will never have to worry about keeping your business up to date with the latest trends. Your IT services provider will be there to handle it all for you.
If you are interested in learning more about our Bay Area IT support services, Contact Us today to schedule a free on-site assessment!
Read MoreTop 15 Weakest Passwords Of 2015
Common Passwords, Common Problems

You lead a busy life, and it’s tricky enough having to remember all of your daily tasks and errands, let alone a new password for each and every account that you have.
So when it comes time to create passwords, you might choose something easy to remember, maybe a simple phrase or series of numbers… It seems obvious, right?
But you wouldn’t leave the doors unlocked to your house right before Christmas, especially with all the presents under the tree…
And likewise, you can’t leave your accounts unprotected by choosing easily-guessed, vulnerable passwords.
With Strong Passwords, You’ve Got 99 Problems… But a Breach Ain’t One

Think about the needle in a haystack, then picture it in a field of haystacks, surrounded by dozens of farms, all full of haystacks. When starting from scratch, cybercriminals have to look for an exact password match without knowing exactly which rules were used to create the passwords.
Thankfully most people have moved past using “P@$$w0rD” but there are a few general rules of thumb when it comes to creating a strong password:
Avoid “Common” Passwords
- For example: “Letmein” or “123456”

But think of your daily routine at work: flooded with deadlines, pulled in an endless number of directions and frazzled when your laptop starts acting up 5 minutes after your computer support technician has gone home. To top it all off, you urgently need access to the account which you use once every six months. And as luck would have it- that same account has conveniently locked you out and you have no idea what the password is.
Once you finally get logged back in, you may be thinking that you never want to deal with being locked out ever again. So of course you’re going to choose the easiest password to remember. After all, it’s just an account you use occasionally, it won’t matter, right? Come to think of it,“P@$$w0rd” is looking like a pretty solid password option. Easy, but not “obvious” right?
So what are a few examples of the weakest passwords of 2014? According to the annual study conducted by SplashData, the Top 25 Worst Passwords of 2013 were:
| Top 15 Worst Passwords of 2013 | |
| Rank | Password |
| 1 | 123456 |
| 2 | password |
| 3 | 12345 |
| 4 | 12345678 |
| 5 | qwerty |
| 6 | 1234567890 |
| 7 | 1234 |
| 8 | baseball |
| 9 | dragon |
| 10 | football |
| 11 | 1234567 |
| 12 | monkey |
| 13 | letmein |
| 14 | abc123 |
| 15 | 111111 |
It’s easy to make password mistakes, especially when they involve seemingly “small” choices. The important decision comes with knowing how to determine which “small” choices can have a surprisingly “big” effect on both you and your business.
As our team will tell you, spend enough time with computer help desk support and you’re bound to see at least a few of the weak passwords on this list. You’d surprised how many “common mistakes” are easily and understandably made when users are struggling without proper tech support for their computers and simply fighting to survive a stressful day.
You’re Not Alone
That’s exactly why managed IT services providers such as Bay Computing are here to help. Having your IT service team a phone call away means that those pesky troubleshooting issues can be taken care of how you need it, when you need it- no matter who is in your office.
How much simpler would it be to have an expert ready on the phone for those moments when IT problems have you ready to throw up your hands? Don’t give up and switch all of those troublesome passwords to “abc123” just yet.
With Bay Computing’s help, your dedicated team is on-call to help guide you through the whole process. Rest easy knowing you are making the right IT decisions for your organization while making the decision to make own your life easier.
Read More

